The Stop Hacks and Improve Electronic Data Security Act (SHIELD Act) requires all covered entities to implement a "Data Security Program."
Complying with the SHIELD Act's Data Security Program requirement could consume significant time and resources. Businesses must put in place administrative, technical, and physical safeguards across 13 different metrics to safeguard the data of New York residents.
We've prepared some practical advice to help you meet each of the SHIELD Act's Data Security Program requirements.
There are two main reasons why you need a Privacy Policy:
✓ Privacy Policies are legally required. A Privacy Policy is required by global privacy laws if you collect or use personal information.
✓ Consumers expect to see them: Place your Privacy Policy link in your website footer, and anywhere else where you request personal information.
Generate an up-to-date 2024 Privacy Policy for your business website and mobile app with our Privacy Policy Generator.
One of our many testimonials:
"I needed an updated Privacy Policy for my website with GDPR coming up. I didn't want to try and write one myself, so TermsFeed was really helpful. I figured it was worth the cost for me, even though I'm a small fry and don't have a big business. Thanks for making it easy."
Stephanie P. generated a Privacy Policy
- 1. Who Needs to Implement a Data Security Program?
- 1.1. Reduced Obligations for Small Businesses
- 1.2. Exemption for Compliant Regulated Entities
- 2. Personal Information vs Private Information
- 2.1. Personal Information
- 2.2. Private Information
- 2.2.1. Type I Private Information
- 2.2.2. Type II Private Information
- 3. Components of a Data Security Program
- 3.1. Reasonable Administrative Safeguards
- 3.1.1. Designating Employees to Coordinate the Program
- 3.1.2. Identifying Internal and External Risks
- 3.1.3. Assessing Safeguards
- 3.1.4. Training Employees
- 3.2. Selecting Service Providers
- 3.2.1. Adjusting the Security Program
- 3.3. Reasonable Technical Safeguards
- 3.3.1. Assessing Network and Software Risks
- 3.3.2. Assessing Information Processing Risks
- 3.3.3. Detecting, Preventing and Responding to Attacks
- 3.3.4. Testing and Monitoring Controls, Systems, and Procedures
- 3.4. Reasonable Physical Safeguards
- 3.4.1. Assessing Information Storage and Disposal Risks
- 3.4.2. Detecting, Preventing and Responding to Intrusions
- 3.4.3. Protecting Against Unauthorized Access
- 3.4.4. Disposing of Private Information
- 4. Summary of Your NY SHIELD Act Data Security Program
Who Needs to Implement a Data Security Program?
Which two exceptions, the SHIELD Act requires "any person or business that owns or licenses computerized data which includes private information of a resident of New York [state]" to implement the Act's Data Security Program.
This applies to companies across the entire world, regardless of whether they have any presence in New York or even the United States.
Reduced Obligations for Small Businesses
Small businesses are not exempt from the SHIELD Act, but they can implement a reduced Data Security Program if appropriate.
Under the SHIELD Act, a "small business" fulfills one or more of the following characteristics:
- It has fewer than 50 employees,
- It had gross revenue of less than $3 million per year in each of the last three fiscal years, or
- It has less than $5 million in year-end total assets, calculated "in accordance with generally accepted accounting principles"
A small business only needs to implement a Data Security Program that is "appropriate," considering:
- The size and complexity of the business
- The nature and scope of its activities
- The sensitivity of the personal information it collects
Exemption for Compliant Regulated Entities
Certain entities that are compliant with other cybersecurity laws are exempt from the Data Security Program requirement of the SHIELD Act.
Your company will be exempt if it complies with one of the following regulations:
- Title V of the Gramm-Leach-Bliley Act (15 USC 6801 to 6809, available here)
- The "Privacy Rule" of the Health Insurance Portability and Accountability Act (HIPAA) (45 CFR parts 160 and 164, available here)
- The NYDFS Cybersecurity Regulation (23 NYCRR 500, available here)
- Any other federal or New York State cybersecurity law
Personal Information vs Private Information

The SHIELD Act distinguishes between "personal information" and "private information."
Personal Information
The SHIELD Act defines "personal information" as:
"any information concerning a natural person which, because of name, number, personal mark, or other identifier, can be used to identify such natural person."
This is a somewhat vague definition. It's important to note that, in addition to a name, number, and "personal mark," personal information includes "other identifier[s]." In certain contexts, identifiers might include an email address, username, or alias.
Private Information
The SHIELD Act's definition of "private information" is more complex. There are two types of private information, which we're calling "type I" and "type II" private information.
Type I Private Information
Type I private information comprises a data set that includes personal information plus one or more of the "data elements" listed below:
- Social security number
- Driver's license number or non-driver ID card number
-
Account number, credit or debit card number, in combination with:
- Any required security code, access code, password or other information that would permit access to an individual's financial account
-
Biometric information, meaning data generated by electronic measurements of an individual's unique physical characteristics, such as:
- Fingerprint
- Voiceprint
- Retina or iris image
- Other unique physical representation or digital representation of biometric data which are used to authenticate or ascertain the individual's identity
There's one more condition. In order to be considered "private information," the data element or the combination of both the personal information and the data element must be:
- Not encrypted, or
- Encrypted, but with an encryption key that has been accessed or acquired
In other words, if the information is encrypted, and the encryption key is safe, it's not private information.
Type II Private Information
Type II private information is:
"a user name or email address in combination with a password or security question and answer that would permit access to an online account."
Components of a Data Security Program

The SHIELD Act Data Security Program consists of three parts:
- Reasonable administrative safeguards, like having a policy in place for sending out data breach notices
- Reasonable technical safeguards
- Reasonable physical safeguards
Throughout this section, we'll be referring to other cybersecurity and data protection laws that impose similar requirements to the SHIELD Act, namely:
- EU General Data Protection Act (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- California Consumer Privacy Act (CCPA)
Reasonable Administrative Safeguards

Administrative safeguards include matters such as your risk assessments, policies, procedures, and staff training.
Here's the relevant section of the SHIELD Act, Section 899-BB.2.(b)(ii)(A):

This is the most extensive section of the SHIELD Act Data Security Program.
Let's consider how you can meet each of these requirements.
Designating Employees to Coordinate the Program
You must designate one or more employees to coordinate the security program.
The SHIELD Act does not give any specific requirements around who would be an appropriate employee. However, a similar requirement exists under the GDPR, appointing a Data Protection Officer, and Section 164.530(a)(1) of HIPAA (available here).
Where appropriate, an employee responsible for coordinating your Data Security Program should:
- Have expert knowledge of data security
- Be allowed to act independently
- Report to the highest level of management
Identifying Internal and External Risks
You must identify reasonably foreseeable "internal and external risks."
Consider risk assessment as a two-stage process:
- Identify potential security risks
- Determine how probable it is that the risks occur, and their potential magnitude
To identify potential risks, you must understand how data flows through your business.
-
Map the data you hold. Consider:
- Your sources of information (customers, third parties, public sources)
- Your storage locations (servers, terminals, laptops, mobile or USB devices)
-
Identify:
- What data belongs to New York residents
- What data is "personal information" and "private information"
- Whether encrypted data could become "private information" if the encryption key is compromised
-
Answer these questions:
- Who has access to private information? Can you restrict access to private information among your employees?
- Are employees accessing private information outside of the office?
For each set of private information, consider:
- Is it unlikely, possible, or probable that a data breach will occur?
- Would the resulting harm be minimal, significant, or severe?
- Based on the above, is the overall risk low, medium, or high?
For more information about data mapping and risk assessment, see our article Conducting a GDPR Data Audit.
Assessing Safeguards
You must assess the sufficiency of the safeguards you have put in place in place to control risks.
Administrative safeguards may include:
- Policies such as a Data Breach Policy or Data Security Policy
- A system of formal sanctions or warnings against staff who act carelessly or maliciously in respect of private information
- Records and logs of system activity detailing when private information has been accessed, deleted, modified, or shared, and by whom
- A process for conducting background checks on job applicants or contractors who could potentially access private information
Consider questions such as:
- Are your policies and procedures made accessible to all relevant employees?
- Do you have a process for regularly reviewing and updating your policies and procedures?
- Are employees made aware of the potential sanctions for misusing private information?
- Are access logs and records regularly reviewed by designated employees?
For more information about creating data safeguarding policies, see our article GDPR Data Protection Policy.
Training Employees
You must train and manage your employees in the practices and procedures of the security program.
It might be appropriate for you to either:
- Create a security training program internally, or
- Hire a suitably certified external provider to deliver a security training program
A security training program should make staff aware of topics such as:
- The SHIELD Act and any other relevant laws and regulations
- Your internal data security policies
- Technical matters such as malware protection and password management
- Dealing with requests to access private information
Where reasonably possible, you should extend your security training program to all employees, including temporary staff, management, and contractors.
Selecting Service Providers
You must select service providers that are capable of maintaining appropriate data security safeguards, and you must impose a contract that requires those safeguards.
You should conduct due diligence on any company with whom you share personal or private information. Consider whether the company is suitably certified, well-established, and legitimate.
Several other privacy laws, such as the GDPR and the CCPA, require a written contract between businesses and their service providers. The SHIELD Act does not specify what this contract should contain.
However, it should normally include at least:
- A clear explanation of the purposes for which you have engaged the service provider
- An agreement that any personal or private information that you share with the service provider will not be used for any purpose outside of the contract
For more information about service provider contracts, see our articles GDPR Data Processing Agreement and The Complete Guide to CCPA Service Providers.
Adjusting the Security Program
You must adjust your security program in light of changes to your business or new circumstances.
For example:
- If you start holding more sensitive private information, you may need to introduce tougher security measures.
- If you take on more employees, you may need to expand your security training program.
- If you start using a new software application or a new service provider, you should make your employees aware of the implications of this change.
- If you suffer a security incident, you may need to undertake a comprehensive review of your Data Security Program.
Reasonable Technical Safeguards

Technical safeguards relate to the technology you use to store, process, and safeguard data.
Here's the relevant section of the SHIELD Act, Section 899-BB.2.(b)(ii)(B):
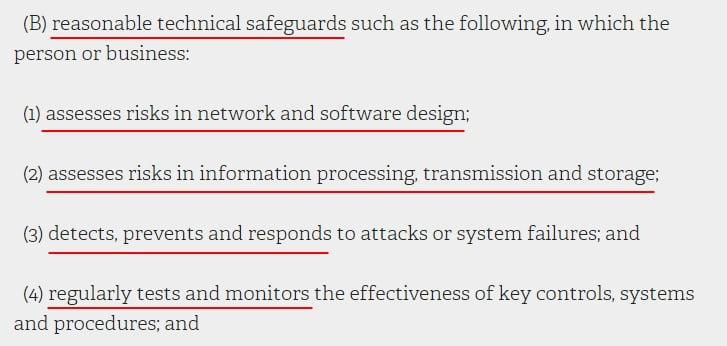
Let's look at how you can meet each of these requirements.
Assessing Network and Software Risks
You must assess risks in the design of your networks and software.
Here are some questions you can ask about your network and software security design:
- Does your IT department have centralized admin control over all endpoint terminals within your business?
- Do you have a process for ensuring firewalls and other network security measures are functioning and correctly configured?
- Are employees forbidden from accessing private information remotely via unsecured public networks?
- Is all software kept patched and up-to-date?
- Are all staff terminals and devices secured via anti-malware software, and is any such software effective and regularly updated?
Assessing Information Processing Risks
You must assess risks in the ways in which you process, transmit, and store personal information.
Here are some questions to consider:
- How do employees transmit personal and private information within your business, and what are the risks involved? For example, via email, secure links, private messaging, etc.
- How do you transmit information to, and receive information from, third parties and service providers?
- Where and how do you store information?
- Do your cloud storage providers offer an appropriate level of data security?
- How do you ensure information is encrypted prior to transmission and storage?
- Do you keep encryption keys separate from encrypted information?
Detecting, Preventing and Responding to Attacks
You must detect, prevent and respond to attacks or system failures.
Each part of your Data Security Program will help you achieve this. Here are some particularly important measures:
-
Install centrally-administered anti-malware software on all staff terminals.
- Ensure that the software can detect and protect against all types of malware, including ransomware
- Enable real-time protection
- Set up automatic deep scans and update checks
-
Develop a comprehensive Data Breach Policy so that employees know:
- How to identify a cyberattack
- Who to report it to
- How to help contain it
Testing and Monitoring Controls, Systems, and Procedures
You must regularly test and monitor the effectiveness of key controls, systems, and procedures.
Consider hiring a third-party company to run penetration testing on your systems. This will help identify vulnerabilities and backdoors that an attacker could exploit.
Reasonable Physical Safeguards

Physical safeguards are measures to protect hardware, equipment, and buildings from attacks and hazards.
Here's the relevant section of the SHIELD Act, Section 899-BB.2.(b)(ii)(C):

Let's look at how you can meet each of these requirements.
Assessing Information Storage and Disposal Risks
You must assess risks in how you store and dispose of information.
Consider how you store data. Your business is likely to use one of the following data storage solutions:
-
Public cloud (Amazon Web Services, Google Cloud,etc.):
- Cheap to set up and maintain
- Limited by your internet speed
- Can be unsuitable for highly sensitive data
-
Onsite data center/private cloud:
- Allows you to prohibit all third-party access to data
- Does not require internet access
- Expensive to install and maintain
-
Hybrid cloud:
- Enables you to store less sensitive data in a cheaper storage environment
- Offers some flexibility if you have unpredictable storage needs
Consider whether your chosen storage solution is appropriate given the nature, scope, and sensitivity of the data that you store.
Detecting, Preventing and Responding to Intrusions
You must ensure you can detect, prevent, and respond to intrusions.
You must also consider whether any information you store on site is physically accessible to an intruder. Consider measures such as:
- Security passes
- ID badges
- CCTV
- Security personnel
Ensure you regularly conduct audits of keys, security passes, and access permissions. Always retrieve keys and passes from employees and contractors who leave your company.
Set workstations to automatically log off if left unattended. Do not allow employees to alter this setting (or other important security settings).
Protecting Against Unauthorized Access
You must protect against unauthorized access to, or use of, private information, during or after the point at which it is:
- Collected
- Transported
- Destroyed
- Disposed of
Sensitive private information should be encrypted at all stages of collection, transportation, and deletion.
Consider using a Virtual Private Network (VPN) when transporting/transmitting data between locations.
Disposing of Private Information
You must dispose of private information within a reasonable amount of time after it is no longer needed for business purposes. You must do this by erasing electronic media so that the information cannot be read or reconstructed.
Consider creating a Data Retention Policy to formalize the periods over which you store different types of private information.
When it comes to data disposal, there are several measures that might be appropriate:
- Data wiping software
- Degaussing: Using magnetic fields to permanently erase data from physical media
- Disassembly
Ensure your employees recognize the importance of not disposing of data in the trash (whether stored electronically or on paper). Many data breaches occur when someone finds sensitive information in a dumpster.
Summary of Your NY SHIELD Act Data Security Program
Your Data Security Program consists of three main elements:
-
Reasonable administrative safeguards:
- Assess internal and external risks
- Designate employees to coordinate the program
- Create data security policies and procedures
- Train your employees in data security
-
Reasonable technical safeguards:
- Assess network and software risks
- Test and monitor software and networks
-
Reasonable physical safeguards:
- Assess information storage and disposal risks
- Transport, store and dispose of information in a secure way

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.




