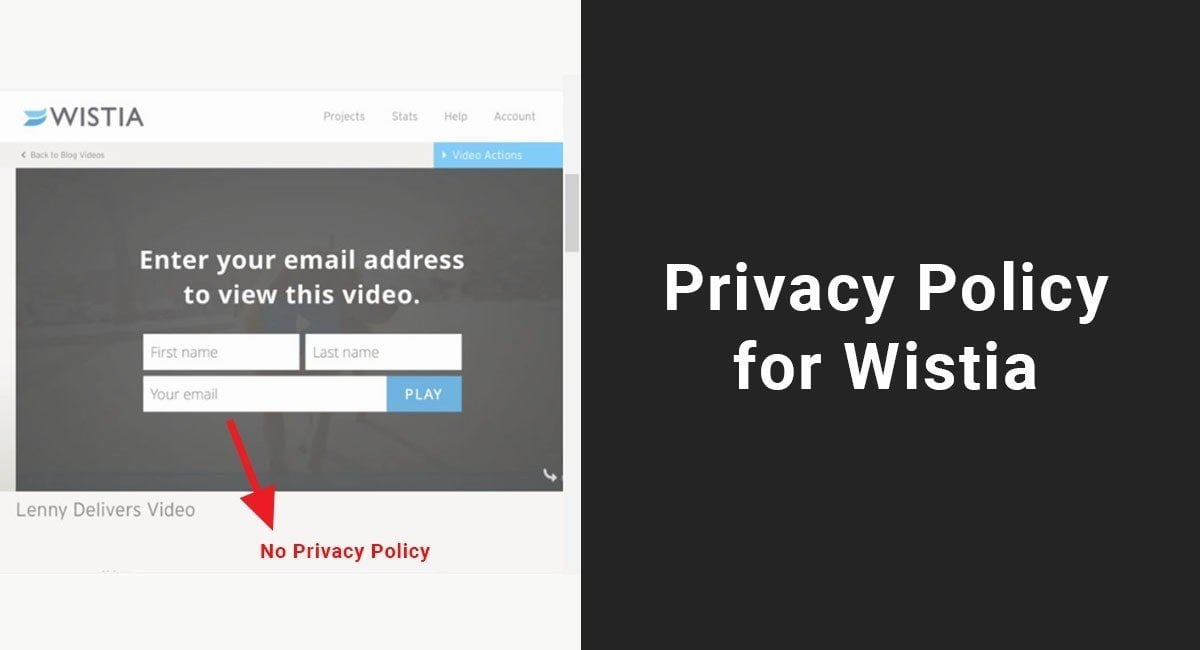
As businesses are increasingly working remotely, cybercriminals have been quick to take advantage of the vulnerable and unprepared. The FBI has warned of a surge in COVID-19-related cyberattacks. Cybersecurity companies claim that malware and phishing scams are on the rise.
Workers accustomed to face-to-face meetings might be finding it difficult to adapt to the new remote working environment. IT departments, too, are struggling to help workforces to get up and running at home.
This is a time of unprecedented financial turmoil for many businesses. But don't neglect the infrastructure that allows your employees to communicate and keeps your company's private information safe.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
At Step 1, select the Website option or App option or both.
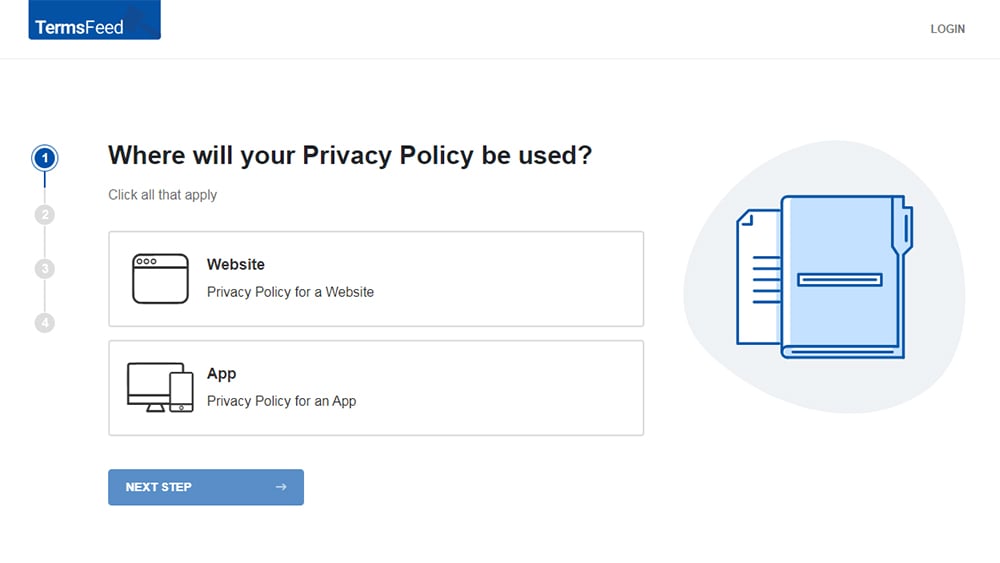
-
Answer some questions about your website or app.
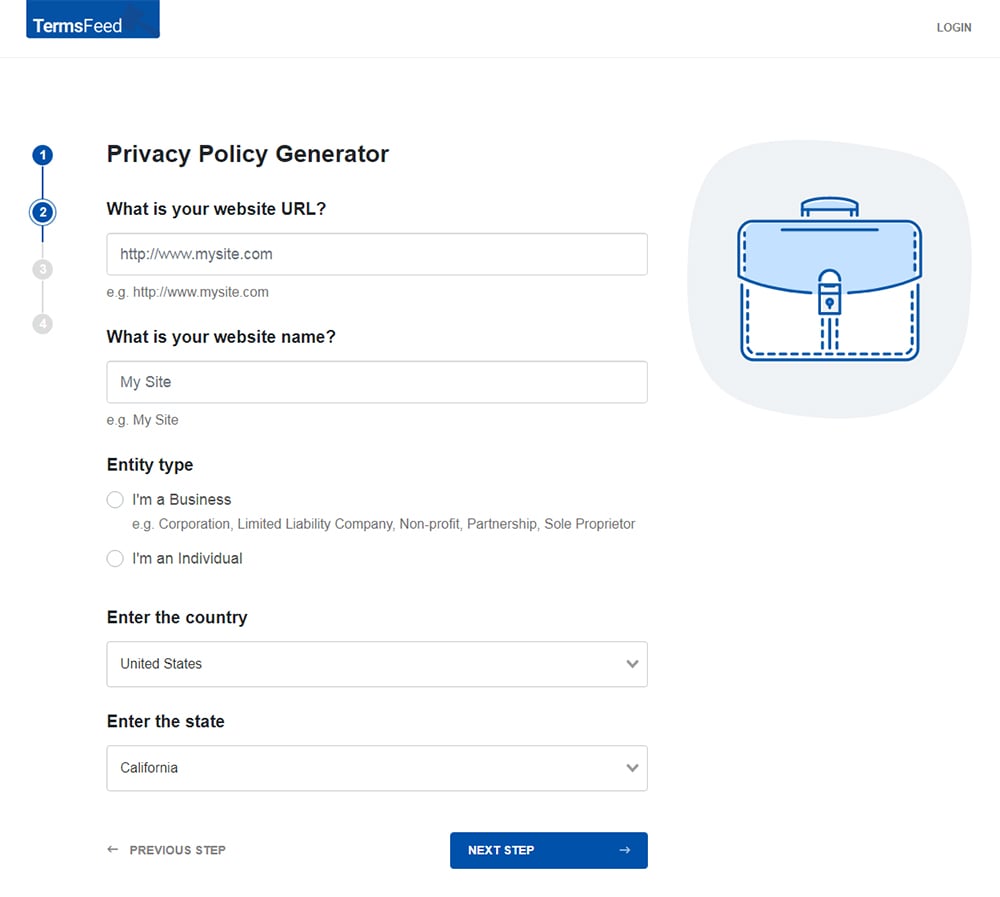
-
Answer some questions about your business.
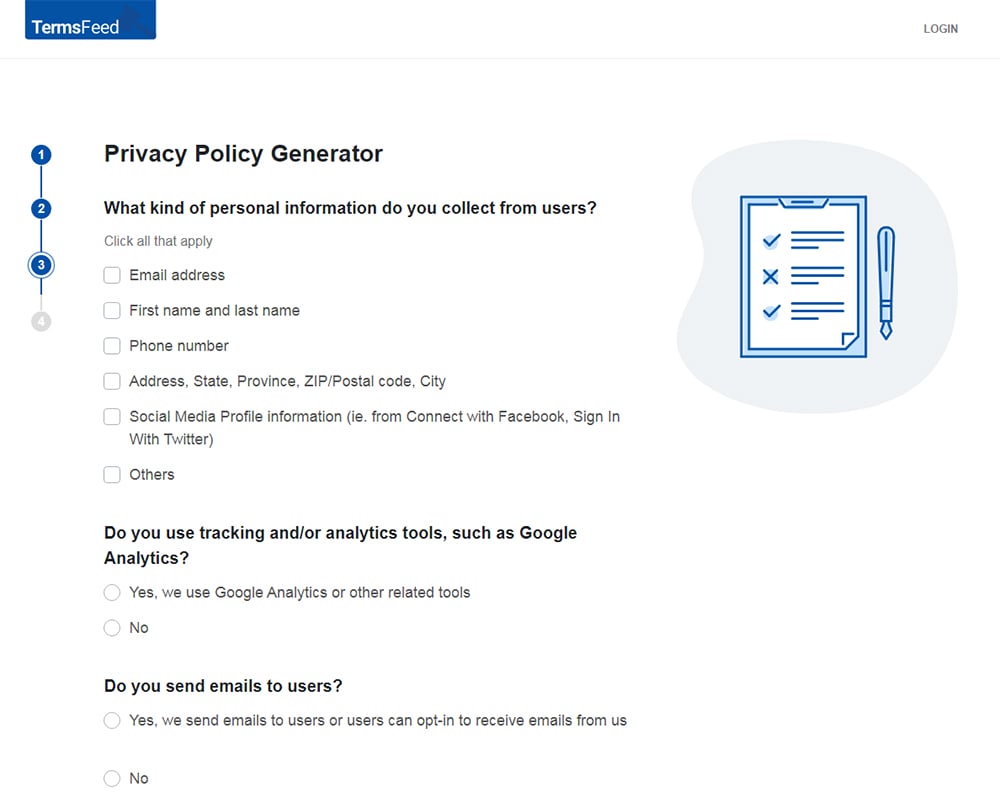
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
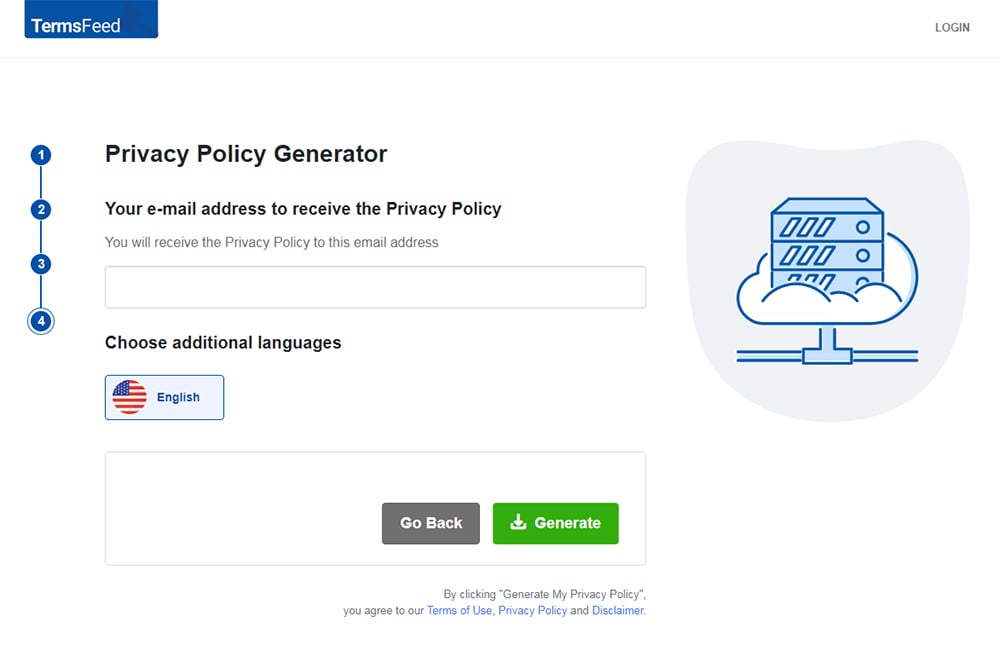
You'll be able to instantly access and download your new Privacy Policy.
- 1. Maintaining Security Standards Among Remote Employees
- 1.1. Keep Up to Date with Emerging Cybersecurity Threats
- 1.2. Provide Cybersecurity Training
- 1.2.1. Legal Compliance
- 1.2.2. Phishing Awareness
- 1.2.3. Safely Using Personal Devices
- 1.3. Consider Adopting New Security Software
- 1.3.1. Anti-Malware Software
- 1.3.2. Password Manager Software
- 1.4. Consider a Virtual Private Network (VPN)
- 1.5. Use Multi-Factor Authentication
- 1.6. Review Your Service Providers
- 1.6.1. Video Conferencing
- 1.6.2. Cloud Storage
- 1.7. Review Your Policies
- 1.7.1. IT Security Policy
- 1.7.2. Data Breach Policy
- 1.7.3. Privacy Policy
- 2. Summary
Maintaining Security Standards Among Remote Employees
Perhaps you've been managing remote workers for years. Or perhaps this environment is uncharted territory.
Either way, you can consider this an opportunity to take stock of your company's remote working practices and work towards the highest standards of cybersecurity.
Keep Up to Date with Emerging Cybersecurity Threats
It's important to remain up-to-date about emerging threats to your company's privacy and security.
The FBI, FCC, and even the WHO regularly release information about the latest threats and scams related to COVID-19.
You should also regularly check for updates to your online platforms and service providers. Companies such as Zoom and Microsoft regularly update their blogs to alert users about any vulnerabilities exposed in their software.
Provide Cybersecurity Training

Your employees' home networks and devices are unlikely to have the same level of security as is available at your business premises.
Mistakes can be costly and can lead to a breach of your company's or your customers' private information.
Cybersecurity and data protection training should be an essential part of your employees' development. If you've never conducted such training with your staff, now's the time to start.
Let's look at some of the elements of an effective cybersecurity training program.
Legal Compliance
Your company is obliged to comply with certain privacy and data security laws. Depending on where your business and your customers are based, such laws may include:
- California Consumer Privacy Act (CCPA)
- New York SHIELD Act
- The EU General Data Protection Regulation (GDPR)
- The UK Data Protection Act 2018
- Canada's Personal Information Protection and Electronic Documents Act (PIPEDA)
It's not enough for your CEO and your IT department to be aware of your company's legal obligations. Everyone in your business is accountable under the law.
Your cybersecurity training can explain:
- The laws and regulations to which your business is subject
- Employees' privacy and security obligations under these laws
- The consequences of failing to comply with privacy and security law
Phishing Awareness
There has recently been an unprecedented rise in "phishing" scams, whereby malicious actors trick people into giving up their personal or sensitive information.
Phishing scams take many forms. A common type of phishing scam is known as "domain spoofing," where cybercriminals set up a fake website that looks near-identical to a legitimate website to trick people into entering their login credentials.
Other phishing scams involve sending fraudulent emails or social media messages requesting personal or financial information.
Your cybersecurity training program can explain:
- How to identify various types of phishing scams
- How to use security software to help avoid falling victim to phishing
- How to respond to a suspected phishing attack
Safely Using Personal Devices
Whether it's out of necessity or a desire to stay in bed, your employees are more likely to access company information from their personal devices when working from home.
Using personal devices may be permitted, forbidden, or unavoidable. In any case, your cybersecurity training program can explain your company's rules on personal devices and provide instructions or advice on how to mitigate the associated risk.
Consider Adopting New Security Software

To ensure employees' home workspaces aren't vulnerable to cyberattacks and data breaches, consider asking them to install security software on any device used to access personal or sensitive data.
Anti-Malware Software
Anti-malware software is a crucial addition to any business workstation.
Attacks involving sophisticated malware, such as ransomware, are increasingly common. Protecting against such threats requires advanced cybersecurity software.
Anti-malware software should:
- Be purchased from a reputable online security company
- Be capable of detecting threats in "real time"
- Offer some degree of centralized administration
Password Manager Software
Poor password habits are a major source of data breaches.
Your employees should not be securing online accounts using easily-crackable passwords such as "password123." They also should not be using the same password for all of their accounts.
It's easy to resolve these poor cybersecurity practices by using password manager software. A password manager generates strong passwords, stores them securely, and automatically enters login information online.
Many password manager providers offer business packages that allow IT departments to centrally manage employees' passwords without invading their privacy. Password managers can also reduce the burden of resetting forgotten passwords.
Consider a Virtual Private Network (VPN)

When employees access your company's data remotely, there is a chance they will do so via an unsecured Wi-Fi network. This leaves your company's data vulnerable to so-called "man-in-the-middle-attacks."
Network security is a key vulnerability when using unknown or public Wi-Fi networks. While none of your employees is likely to be working in a coffee-shop any time soon, their home Wi-Fi network also might not be sufficiently secure.
To facilitate secure remote access to your company's servers, consider setting up a Virtual Private Network (VPN).
A VPN allows remote workers to access all resources on your office IT network via a secure, encrypted connection. A VPN will encrypt data flowing to and from your company's network even if accessed via an unsecured public network.
You can set up a VPN with a third-party provider without needing to install any physical hardware at your office. Reputable VPN providers such as NordVPN, ExpressVPN, and IPVanish all have ready-to-use VPN software solutions for business customers.
Use Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra security step when logging into company accounts.
When using MFA, your employees will need to verify their identity by providing multiple pieces of authenticating data. For example, as well as entering a password, they might be required to enter a verification code received via their email address or mobile device.
MFA is a requirement under certain cybersecurity laws, such as the NYDFS Cybersecurity Regulations (23 NYCRR 500, available here), and the EU Payment Services Directive.
Businesses can implement MFA into their login processes using software such as Microsoft MFA or password manager providers such as LastPass.
Review Your Service Providers

Many workers have had to familiarize themselves with new software applications in recent weeks. Using new service providers comes with privacy and security considerations.
Businesses subject to the CCPA or GDPR must only share personal information with service providers subject to a written contract.
For more information, see our articles The Complete Guide to CCPA Service Providers and GDPR Data Processing Agreement.
Video Conferencing
The COVID-19 lockdown has seen unprecedented use of video conferencing software such as Zoom, Microsoft Teams, and Skype.
Using video conferencing software involves inherent cybersecurity risks. Whatever platform you choose, it's worth conducting a risk assessment.
Consider:
- Does the platform feature end-to-end encryption, to protect audio, video, and text content?
- Can employees share files using the video conferencing platform? If so, is this secure?
- Are meetings vulnerable to intruders?
- Whose personal information will be transmitted using the platform (customers, clients, employees, etc)?
Note that there have been some controversies around the privacy and security practices of Zoom. For more information, see our article How to Securely Implement and Use Zoom.
Cloud Storage
If your team is working from home, this means cloud storage is more useful and convenient than ever.
Remotely sharing and collaborating on documents is simply not possible without using a cloud storage platform.
Whether you've used a cloud storage provider for some time, or you've only started recently as a result of the pandemic, think carefully about your practices.
- Does the cloud storage provider provide an appropriate level of security?
- Can you restrict access to certain sensitive information among certain employees?
- Are you storing personal information in the cloud? Is this appropriate?
Review Your Policies

As your working practices change, so should your policies. This applies to both internal company documents and your customer-facing Privacy Policy.
IT Security Policy
It's crucial to maintain a robust and comprehensive IT Security Policy to help employees navigate your rules when working from home.
You can't expect to be able to hold employees accountable for lapses in security unless your company's rules are clear.
Your IT Security Policy can detail information such as:
- The laws and regulations under which employees are accountable
- The roles and responsibilities of staff within your company
- The requirements around using anti-malware software
- Password protection rules
- Rules on the use of company email accounts
- Limitations on remote access to personal or sensitive information
- The disciplinary procedure that will apply if members of staff violate your IT Security Policy
Data Breach Policy
You should review your company's Data Breach Policy to ensure that it is appropriate in the current circumstances.
Your Data Breach Policy should explain:
- What qualifies as a data breach (e.g. loss or theft of personal or sensitive information)
- What employees should do if they suspect a data breach has occurred
- The relevant data privacy and security laws that apply in the event of a data breach
- The chain of command and responsibilities of various members of staff if a data breach occurs
Your company may not necessarily require a standalone Data Breach Policy. This information can be integrated into your IT Security Policy or staff handbooks.
In any case, it's essential that anyone with access to personal or sensitive data understands how to identify, contain, and respond to a data breach.
Privacy Policy
The change in working habits has implications for your company's Privacy Policy.
If you are introducing new communications, storage, or customer relationship management (CRM) platforms to help your company adapt to the new working environment, you should update your Privacy Policy to reflect these changes.
Here's how RStudio presents information about its third-party service providers in its Privacy Policy. Note that Zoom and other web conferencing software providers are on the list:
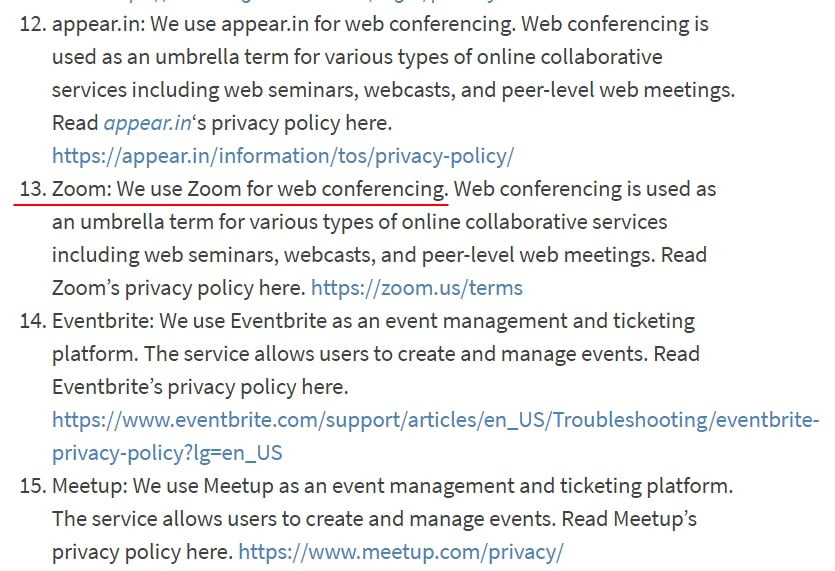
Be as transparent as possible about how your business uses consumers' personal information.
Summary
Managing your remote employees' cybersecurity practices might be a challenge. But you remain legally and ethically obliged to protect personal and sensitive information in your company's control.
Some ways to make this transition to remote more secure include:
- Keeping up-to-date on the latest cybersecurity developments and threats
- Providing remote cybersecurity training to your employees
- Adopting or updating security software such as anti-malware and password management software
- Setting up a Virtual Private Network (VPN) to ensure secure access to your company network
- Implementing Multi-Factor Authentication (MFA) for additional login protection
- Reviewing how you use service providers such as video conferencing and cloud storage companies

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.