Zoom, the video conferencing software operated by Zoom Video Communications Inc., has experienced a huge surge in users since the COVID-19 pandemic began.
As a relatively new player in the telecommunications market, Zoom has been hit by a flurry of controversies and allegations in recent months. Although it's undeniably user-friendly and convenient, some are questioning whether Zoom is a secure enough platform for private conversations.
Whether you're using Zoom to hold staff meetings, serve your clients, or chat with your grandma, it's important to be aware of the privacy and security risks of using Zoom and how to mitigate them.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
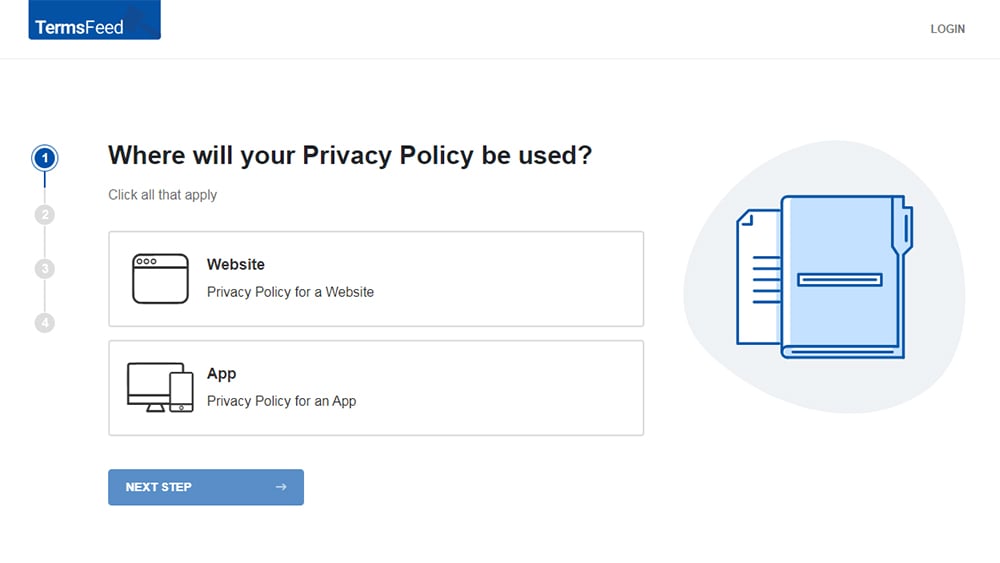
At Step 1, select the Website option or App option or both.
-
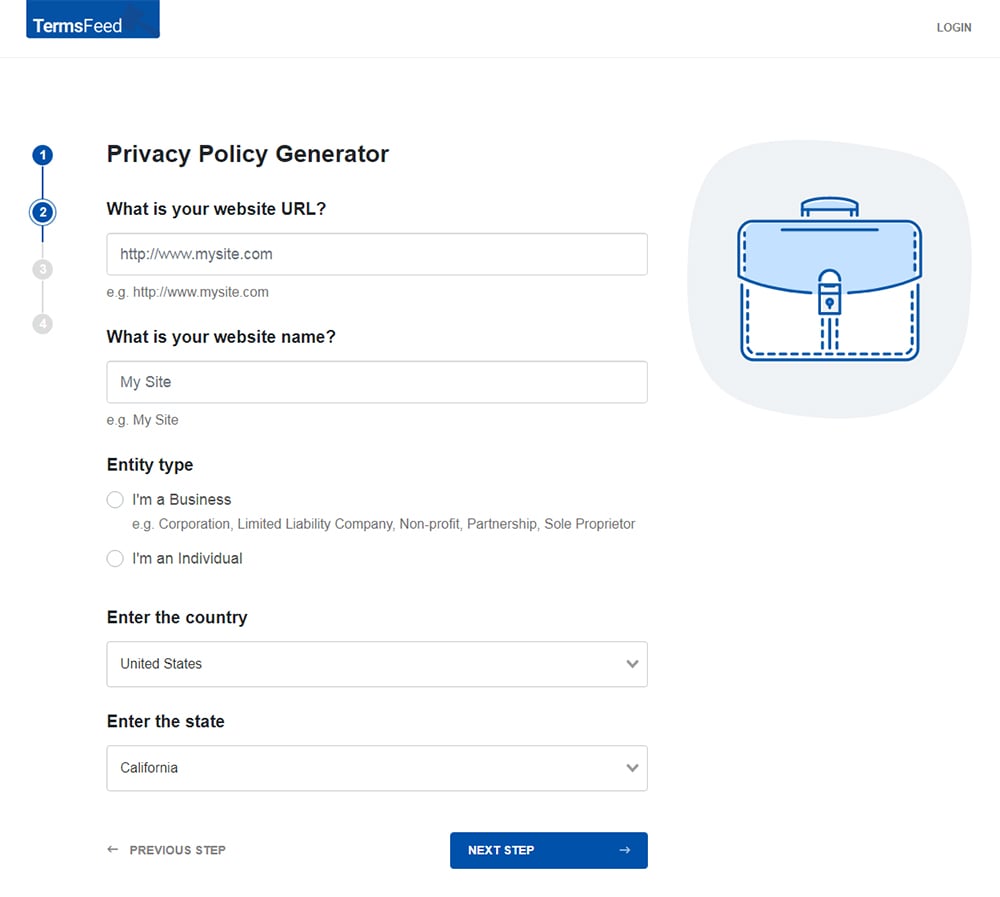
Answer some questions about your website or app.
-
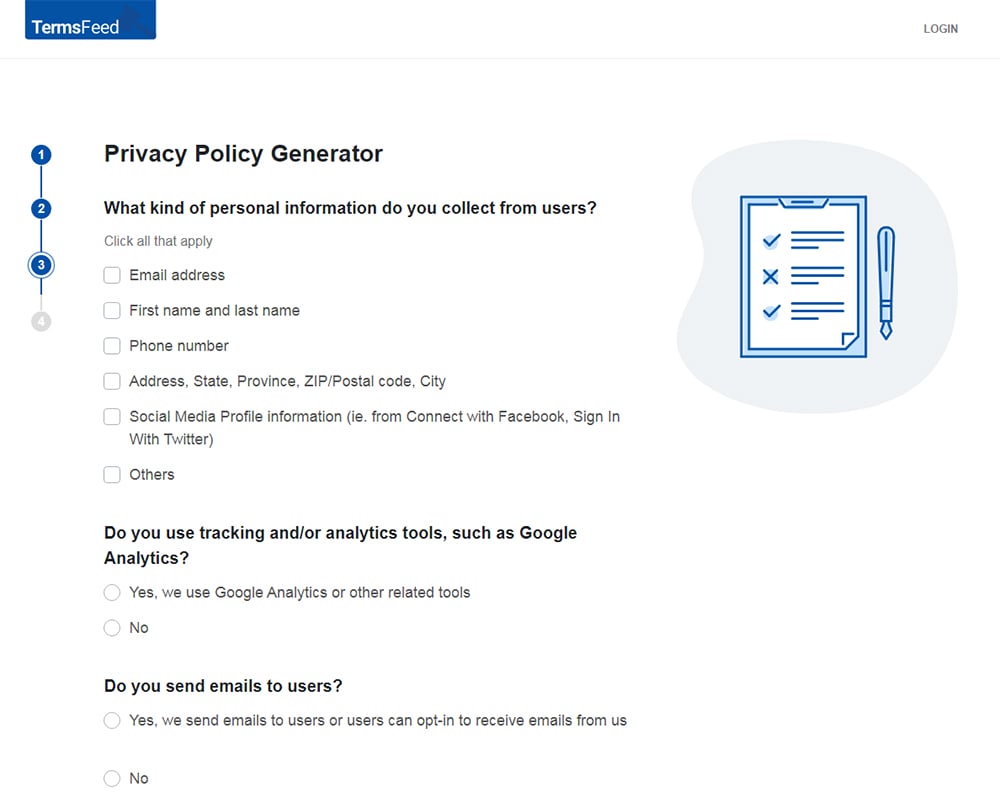
Answer some questions about your business.
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
You'll be able to instantly access and download your new Privacy Policy.
- 1. Is Zoom Secure?
- 1.1. Zoom-Bombing
- 1.2. Sharing of Data
- 1.3. Encryption Controversy
- 1.4. Do These Security Issues Really Matter?
- 2. Best Practices When Using Zoom
- 2.1. Update Your Privacy Policy
- 2.2. Password Protect Meetings
- 2.3. Enable Waiting Room
- 2.4. Lock Your Meetings
- 2.5. Disable File Transfer
- 2.6. Prevent Participants from Screen Sharing
- 2.7. Keep Meeting Details Private
- 3. Summary
Is Zoom Secure?
Before we talk about how to securely set up and use Zoom, it's important to establish the nature of some of Zoom's alleged security issues.
Zoom-Bombing
One of Zoom's most notorious security issues is so-called "Zoom-bombing."
Zoom-bombing occurs when an uninvited participant intrudes on a Zoom meeting that has not been password protected. It can lead to the video, audio, text, or files shared during the meeting becoming compromised.
Zoom-bombing works when an intruder generates a valid Zoom ID for a private meeting. The Zoom ID is a nine-11 digit number allocated to each Zoom meeting. Cybercriminals and trolls have figured out how to "guess" these numbers by brute force and other methods.
Since the COVID-19 lockdown began, Zoom-bombers have invaded meetings hosted by organizations such as the FBI and the University of Southern California, which complained of "racist and vile" messages being posted during online classes.
Sharing of Data
Zoom's data-sharing practices have come under scrutiny recently, particularly since Zoom users initiated a class-action lawsuit against the company alleging breaches of the California Consumer Privacy Act (CCPA).
Zoom's data-sharing issues came to light when it was revealed that Zoom's iOS app shared data including browser version, advertising ID, and time zone with Facebook whenever users logged into Zoom, regardless of whether they had a Facebook account.
The class-action against Zoom has yet to be heard, but if successful, it could end up costing Zoom hundreds of millions of dollars in damages.
Encryption Controversy
Zoom has long claimed to protect meeting data using "end-to-end encryption." This data protection technique ensures that data can only be understood by its intended recipient.
However, in March 2020, online publication The Intercept revealed that Zoom does not actually support end-to-end encryption, but instead uses transport encryption. While this form of encryption adequately protects data in transport, it does not prevent Zoom itself from viewing meeting data.
Zoom claims to have been using the term "end-to-end encryption" differently from how it is commonly understood. But this definition has been characterized as misleading by some cryptography experts.
Do These Security Issues Really Matter?

You may ask if these security issues are actually an issue. Perhaps you wouldn't really care even if someone did intercept your Zoom conversations.
After all, Zoom is being used by all manner of major businesses, schools, and public bodies. How bad can the security issues really be?
Whether you think these security issues really matter is a judgment call for your business. Bear in mind, though, that you're legally obliged to protect the personal information of your customers, clients, and employees.
Personal information is any information capable of being identified with a living individual. It includes information such as names, contact details, and even anecdotal information or opinions about others.
Person information is protected by law. Disclosing personal information via Zoom or any other platform is a legally-regulated activity. This includes whether you're disclosing personal information via audio, video, text, or by exchanging files.
Given the nature of your business and your purposes for using Zoom, this software may represent a sufficiently secure platform. If you're willing to take a risk with personal information (however small), you must take steps to minimize that risk, and you must be transparent.
Best Practices When Using Zoom

If you do decide that Zoom is the right platform for your business, you can take certain steps to make it as secure as possible.
Update Your Privacy Policy
Regardless of any steps you take to mitigate Zoom's potential security issues, you should be disclosing your use of Zoom in your company's Privacy Policy, particularly if you use it to collect, discuss or disclose personal information.
If you're using Zoom to provide services to your clients or customers, you could use your Privacy Policy to provide a link to Zoom's Privacy Policy or simply explain the purposes for which you use the platform.
Using Zoom to discuss individual customers, clients, or even employees (in certain jurisdictions) also requires disclosure in your Privacy Policy. Even if you don't believe any individual could be identified via your conversations on Zoom, you should make this disclosure just in case.
Relevant privacy laws that would require this disclosure include:
- California Consumer Privacy Act (CCPA)
- EU General Data Protection Regulation (GDPR)
- Canada's Personal Information Protection and Electronic Documents Act (PIPEDA)
Any business covered by one of the above laws should be explaining how it shares personal information with other businesses, and explaining its reasons for doing so.
Here's an example from Boxcryptor's Privacy Policy:
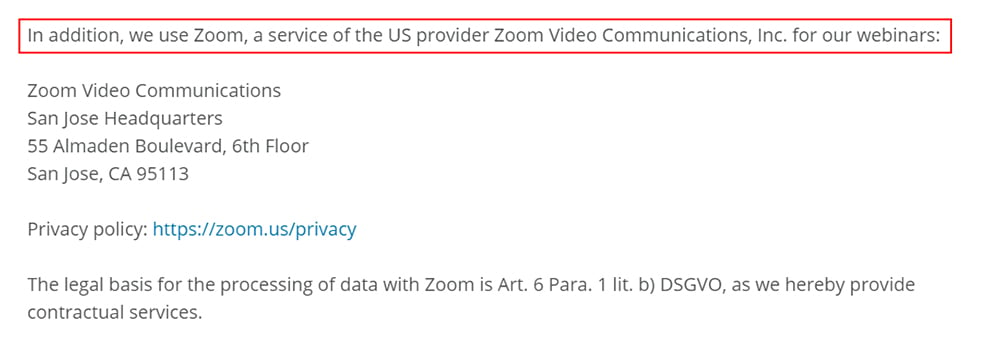
Boxcryptor explains its purpose for using Zoom, provides contact details Zoom, and a link to the company's Privacy Policy.
Boxcryptor also provides its legal (lawful) basis for processing personal information under the DSGVO, the implementation of the GDPR that applies in the German state of Berlin. This is important for any company with customers, clients, or employees in the EU or the UK.
Here's another example, from marketing company Amy Hall:
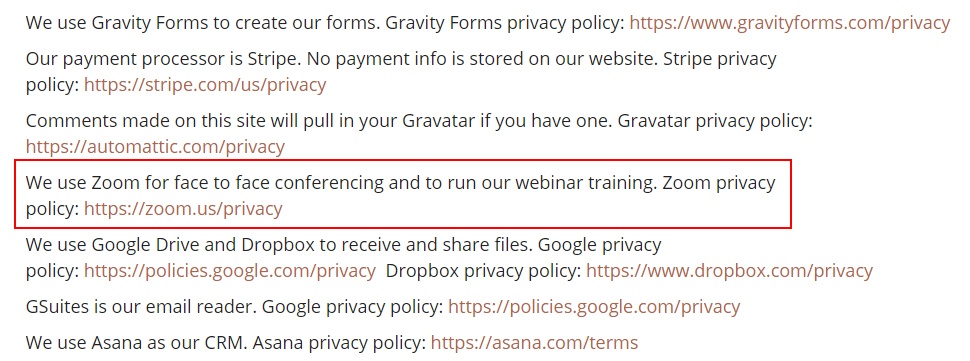
Amy Hall provides less detail than Boxcrytor, simply listing Zoom among several of the company's service providers.
However you use Zoom, you should be transparent about this in your Privacy Policy. This is particularly important in case you ever suffer a data breach or have a customer complaint involving Zoom.
Password Protect Meetings
Whenever feasible, you should password protect your Zoom meetings to prevent uninvited guests.
You can find this option when scheduling a meeting using Zoom's browser-based web app:
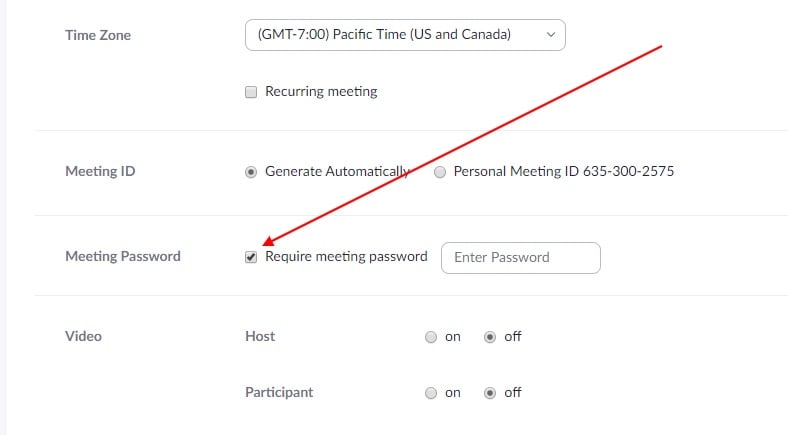
You can use the default password, or choose a longer one that's harder to crack.
Enable Waiting Room
Use Zoom's "Waiting Room" feature to ensure your meeting room remains invitation-only.
Since March 2020, the "Enable Waiting Room" setting is enabled by default. It's strongly recommended that you keep it that way.
On the Zoom desktop app, this setting lives under the "Security" tab on the main screen:
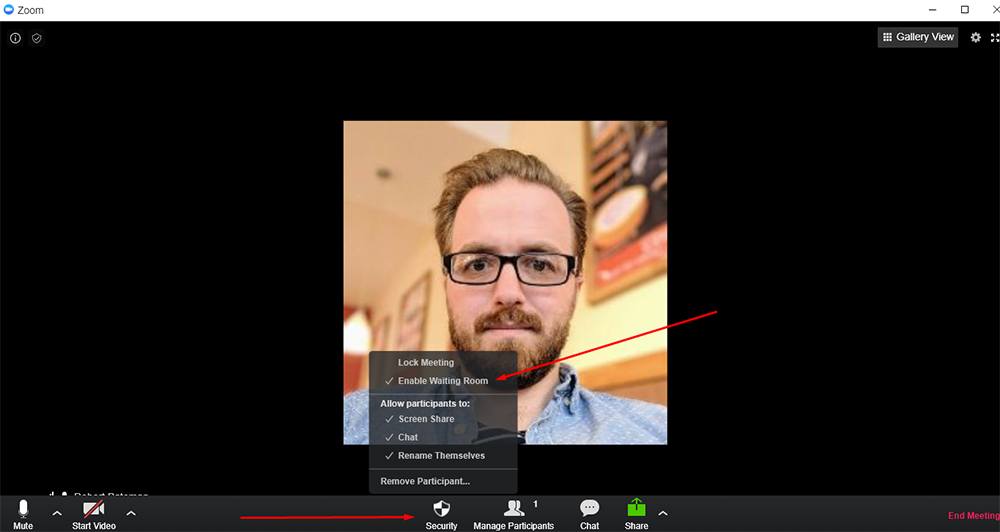
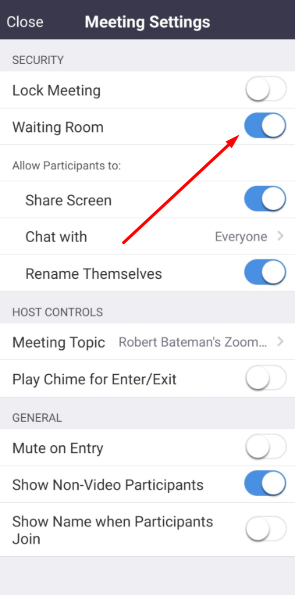
When using the Zoom mobile app, you can toggle "Waiting Room" in the "Meeting Settings" menu:
Lock Your Meetings
Once all invited participants have entered your Zoom meeting, you should lock the meeting as an additional security measure.
You can do this by selecting "Lock meeting" from the "Security" tab at the bottom of the main Zoom application window:
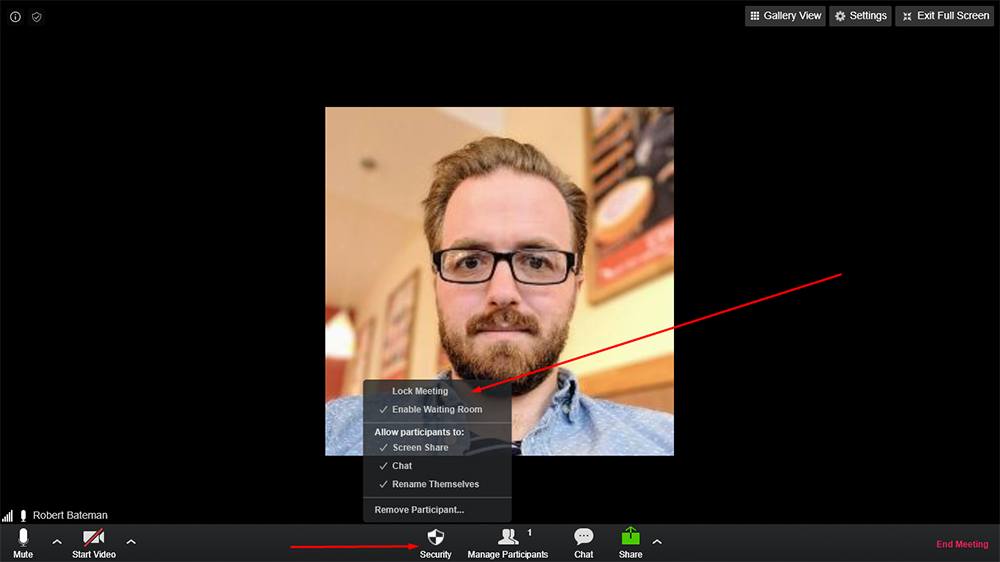
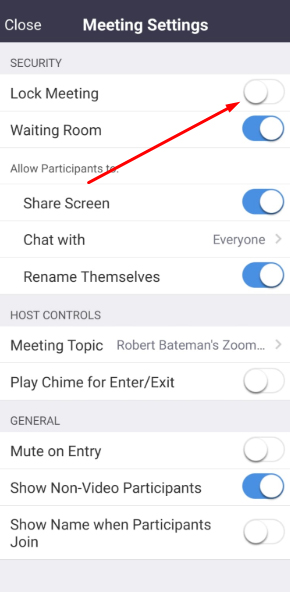
When using the Zoom mobile app, you can toggle "Lock Meeting" in the Meeting Settings" menu:
Disable File Transfer
The host of a Zoom meeting should have a clear purpose for the meeting in mind. Unless it's necessary to transfer files using the Zoom client itself, you should disable the "File transfer" setting by default.
You'll find the "File transfer" setting in the "In Meeting (Basic)" section of the "My Settings" menu in Zoom's web app:
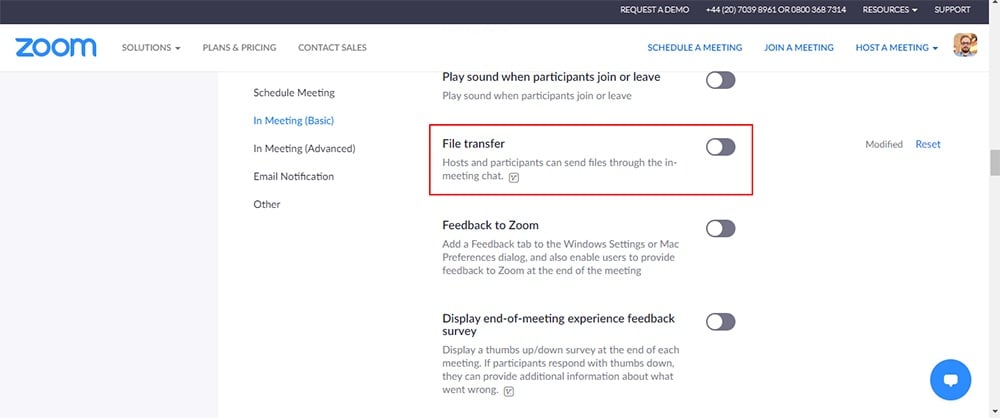
Disabling this setting prevents the possibility of any user sending unnecessary personal information or malicious files to the meeting participants.
Prevent Participants from Screen Sharing
As further protection against the malicious actions of Zoom-bombers, you should prevent participants from sharing their screens unless it's necessary for them to do so.
You'll find the "Screen sharing" settings in the "In Meeting (Basic)" section of the "My Settings" menu in Zoom's web app:
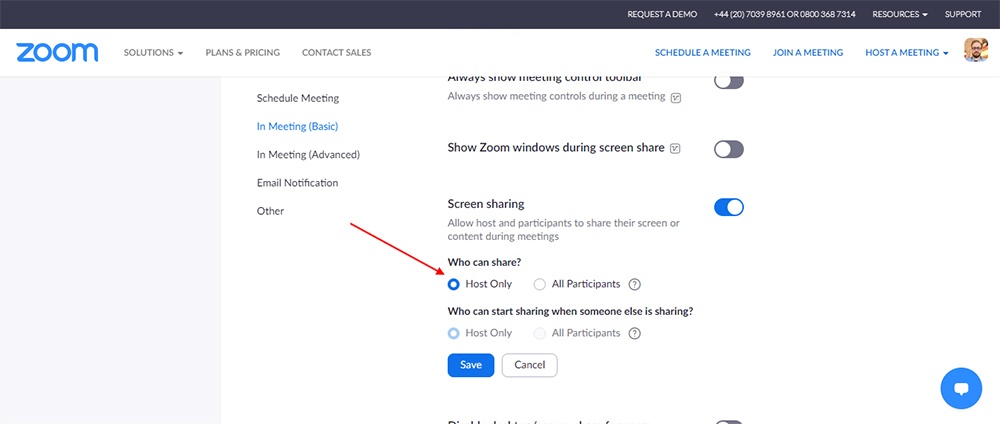
Keep Meeting Details Private
Ensure your Meeting ID and password are only made available to the intended meeting participants. Do not share these details on social media, or allow participants to do so.
Summary
Despite a few controversies, Zoom is a relatively secure platform and suitable for most non-sensitive contexts. Also, the company is continually taking steps to ensure it improves its security based on user feedback (and lawsuits!).
Here are some steps you can take to help ensure your Zoom meetings are secure and compliant with privacy law:
- Update your company's Privacy Policy to explain how you use Zoom
- Password protect scheduled meetings
- Enable the "Waiting Room" feature
- Lock your meetings once all participants have arrived
- Disable file transfer where feasible
- Prevent participants from screen-sharing where feasible
- Keep meeting details private

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.