The COVID-19 pandemic has prompted big changes in how companies operate.
Remote working may be mandatory for some time. Even once restrictions ease off, you may find that your employees wish to continue working from home.
Working remotely has many advantages, but also presents a risk to the security and confidentiality of your company's data.
We've compiled a checklist, suitable both for employers and employees, of data security essentials when working from home. Consider all of these points as you adapt to the new business environment.
- 1. Data Security Policies
- 1.1. For Employers
- 1.2. For Employees
- 2. Phishing Awareness
- 2.1. For Employers
- 2.2. For Employees
- 3. Company-Approved Devices
- 3.1. For Employers
- 3.2. For Employees
- 4. Sharing Company Devices
- 4.1. For Employers
- 4.2. For Employees
- 5. Securing Company Devices
- 5.1. For Employers
- 5.2. For Employees
- 6. Security Software
- 6.1. For Employers
- 6.2. For Employees
- 7. Using Work Email Accounts
- 7.1. For Employers
- 7.2. For Employees
- 8. Network Protection
- 8.1. For Employers
- 8.2. For Employees
- 9. Work-From-Home Checklist Summary
Data Security Policies
For Employers
Now is the time to revisit your company's data privacy and security policies to ensure they are relevant to the new remote-working environment.
If you don't have any data privacy or security policies, now's the time to create these documents.
What customers say about TermsFeed:
This really is the most incredible service that most website owners should consider using.
Easy to generate custom policies in minutes & having the peace of mind & protection these policies can offer is priceless. Will definitely recommend it to others. Thank you.
- Bluesky's review for TermsFeed. Read all our testimonials here.
With TermsFeed, you can generate:
Such documents may include:
-
IT Security Policy: Your internal IT Security Policy should set out best practice for remote working, including:
- Device hardware standards
- Password management
- Minimum password standards
-
Data Breach Policy: Whether integrated into your IT Security Policy or available as a separate document, your Data Breach Policy should help your employees respond to the loss or theft of company data, including:
- What constitutes a data breach (i.e. the loss or unauthorized access of personal or sensitive data)
- How to recognize a data breach
- What action to take in the event of a data breach
-
Privacy Policy: Your company's Privacy Policy may require updating if your employees are accessing or processing personal information in new ways, for example:
- Conducting meetings on new video conferencing platforms
- Sharing personal information with new service providers (such a Zoom or Microsoft)
You should ask your employees to review these documents regularly.
For Employees
Your employer should have a set of data security policies such as an IT Security Policy, a Data Breach Policy, and a public-facing Privacy Policy.
You are responsible for reviewing these documents to ensure you understand the data security standards that apply when accessing company data.
If you don't know whether your employer has such documents, or they don't answer all your questions about working remotely, ask your employer for more information. It's particularly important that you know what to do in the event of a data breach.
Phishing Awareness

For Employers
COVID-19 has seen an unprecedented surge in phishing scams.
Phishing awareness should already be part of your company's cybersecurity training program. As your employees begin working from home, they'll be more vulnerable than ever to phishing.
Make sure you remain alert to the latest phishing scams, and that you quickly communicate warnings and guidance to your employees.
For Employees
Phishing scams involve tricking individuals into giving up personal or sensitive information. This common type of cybercrime can compromise your company's security.
Phishing scams may include malicious emails or "spoof" websites designed to steal your login credentials.
Here are some tips to avoid phishing scams:
- Do not respond to emails, SMS, or social media messages unless you are sure you can verify the sender.
- When receiving an email from an unknown sender, don't click on links or download attachments.
- Check for the "padlock" symbol in your browser address bar when visiting a website.
Company-Approved Devices

For Employers
Your employees' remote-working setup should be a top priority.
Ideally, your employees should only access company data on devices under your company's control.
Your employees may have been working on a laptop or computer that they can simply take home. If not, you may need to buy new devices for your employees.
You should ask your employees to send you the specifications of any devices on which they are accessing company data. Older operating systems, such as Windows 7 or macOS 10.12 Sierra, are no longer supported by their developers and should be upgraded.
For Employees
Company data should only be accessed on devices with a high standard of security. Your employee may have specific hardware requirements.
If you're used to working on a particular computer or device in your office, you may wish to ask if you can work on this device at home for the time being.
If not, you should check with your employer before working from a personal device. It is best not to access company data on outdated equipment, which may be vulnerable to malware or unauthorized access.
Sharing Company Devices

For Employers
If your budget won't stretch to purchasing your employees devices for their own exclusive use, you should urge them not to share devices used to access company data.
Of course, refusing to share a personal device might not be practical for all employees. In which case, you may need to provide guidance on setting up multiple user profiles.
For Employees
It's important not to share your company devices with other members of your household. This could result in the compromise of personal or company information.
If you're stuck at home with only one laptop, and other members of your household absolutely need to use it, then you should set up multiple user profiles to ensure that company information is off-limits to anyone other than yourself.
In Windows 10, you can add new users to your device using in the "Family & other users" section of your PC's settings:
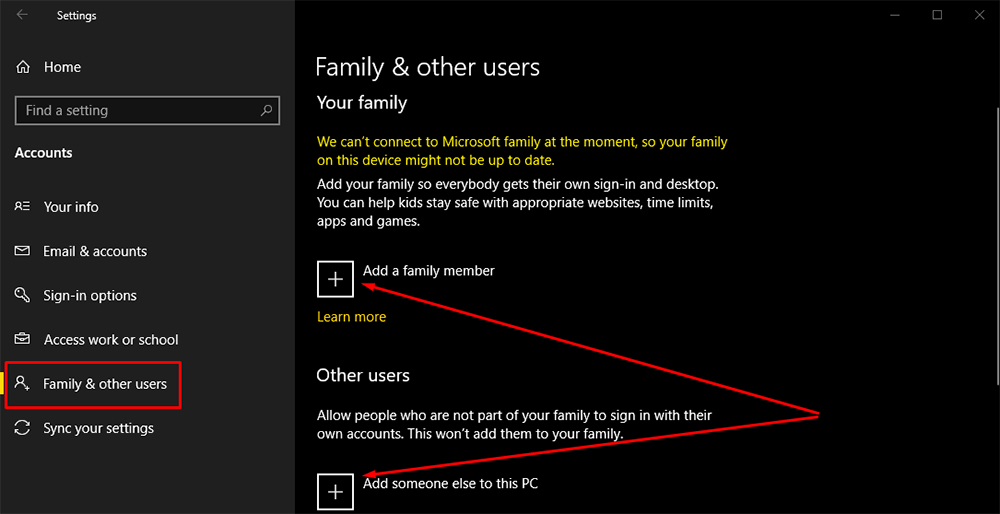
You can also set up multiple user profiles in macOS, and even on Android and iOS mobile devices.
Securing Company Devices

For Employers
Your IT Security Policy should require employees to lock any company-approved devices when not in use. You should have minimum standards for device-locking, specifying:
- The minimum length and complexity of passwords
- What unlock methods are acceptable on mobile devices (e.g. pattern, PIN, fingerprint)
- The mandatory timeout period, after which a device locks automatically
Consider whether multi-factor verification (MFA) represents an appropriate option for company devices. It may be possible to distribute MFA hardware devices such as YubiKey.
For Employees
Don't leave company devices unlocked. Leaving devices unlocked represents a security risk, even if you only live with your close family.
Ensure you set a short timeout period so that your device locks automatically when not in use. Your employer may specify this timeout period in your IT Security Policy.
For mobile devices, using a PIN, passcode, or pattern is more secure than using biometric information such as fingerprint, voice, or face unlock.
Security Software

For Employers
Company-approved devices should be secured by company-approved security software.
This should include anti-malware software capable of detecting advanced threats such as malware. It may also include password management software to ensure your employees are using sufficiently long and complex passwords.
If you already have security software installed on your office computers, now might be the time to invest in some additional licenses. This will allow your employees to install security software on any personal devices they use to remotely access company data.
For Employees
Security software such as anti-malware (antivirus) applications and password management software is an important means by which to keep your company's data secure.
However, be aware that some security software can do more harm than good. Check with your employer before accessing company data on a personal device with security software installed.
Using Work Email Accounts

For Employers
Employees who are accustomed to a particular email client in the office may struggle to access email remotely. This can result in employees forwarding work-related correspondence to their personal email account.
Your employees' personal email accounts may provide a lower level of data security than your company's email provider. Certain email providers use weak encryption, enforce low standards of password security, and can be subject to cyberattacks.
Your IT Security Policy should make it clear that only company email accounts should be used for work-related correspondence.
For Employees
It can be tempting to forward work-related email correspondence to your personal Gmail, Yahoo, or Hotmail account. However, forwarding work-related emails to such services can compromise the confidentiality of your company's data.
If you're used to a particular work email setup, it can be difficult to adapt. For example, using browser-based web apps can feel awkward if you're used to a desktop-based software client.
If you're finding the transition to remote email access difficult, reach out to your IT department for guidance.
Network Protection

For Employers
Your employees' home networks may not be sufficiently secure.
To protect against man-in-the-middle attacks, consider setting up a virtual private network (VPN) via which employees can access resources on your company network.
A VPN provides a secure, encrypted tunnel between your employees' devices and your company's servers.
A VPN doesn't have to be manually set up by your IT department. There are many commercial VPN providers that provide packages for business customers.
For Employees
You should run a security check on your home network to determine whether there are any security issues. You should also consider using a VPN to access sensitive company data.
Ensure your router is password-protected and up-to-date.
If you're planning to use a VPN, or if you already use one for personal reasons, you should check with your employer before accessing company data. While VPNs are generally very secure, some less reputable VPN brands have security issues.
Work-From-Home Checklist Summary
- Make sure data security policies are up-to-date
- Be aware of phishing scams
- Only use company-approved devices
- Avoid sharing company-approved devices
- Ensure company-approved devices are locked and secure
- Install security software on company-approved devices
- Do not use personal email accounts to send or receive company data
- Ensure home networks are sufficiently secure

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.