As your company grows, it will handle increasing amounts of personal and sensitive information. As you bring on new staff and expand your operations, you'll acquire more and more devices, software, and network infrastructure.
It's easy to lose track of your IT equipment, which can lead to data breaches and misuse of company property. An IT Security Policy can help your company manage and protect its data and assets.
In this article, we'll be walking you through some of the key sections that an IT Security Policy should contain, and will provide some real examples of existing policies.
There are two main reasons why you need a Privacy Policy:
✓ Privacy Policies are legally required. A Privacy Policy is required by global privacy laws if you collect or use personal information.
✓ Consumers expect to see them: Place your Privacy Policy link in your website footer, and anywhere else where you request personal information.
Generate an up-to-date 2024 Privacy Policy for your business website and mobile app with our Privacy Policy Generator.
One of our many testimonials:
"I needed an updated Privacy Policy for my website with GDPR coming up. I didn't want to try and write one myself, so TermsFeed was really helpful. I figured it was worth the cost for me, even though I'm a small fry and don't have a big business. Thanks for making it easy."
Stephanie P. generated a Privacy Policy
- 1. What is an IT Security Policy?
- 1.1. Does Your Company Need an IT Security Policy?
- 1.2. Is an IT Security Policy Required By Law?
- 1.3. What are the Benefits of having an IT Security Policy?
- 2. What to Include in Your IT Security Policy
- 2.1. Purpose and Objectives
- 2.2. Scope
- 2.3. Applicable Laws
- 2.4. Roles and Responsibilities
- 2.5. Procurement of IT Equipment
- 2.6. Anti-Malware Software
- 2.7. Backups
- 2.8. Network Security
- 2.9. Use of Email
- 2.10. Use of the Internet
- 2.11. Password Security
- 2.12. Remote Access
- 2.13. Data Breach Response
- 3. Summary of Your IT Security Policy
What is an IT Security Policy?
An IT Security Policy sets out safeguards for using and managing IT equipment, including workstations, mobile devices, storage devices, and network equipment.
Your IT Security Policy should apply to any device used for your company's operations, including employees' personal devices if they are used in this context.
An IT Security Policy can help establish:
- How your company's staff use the internet and their company email accounts
- The standards that apply when procuring new IT equipment
- Rules for home working and remote access
In addition to an IT Security Policy, your company might also have other related policies, including:
Alternatively, you can integrate these other policies as sections of your IT Security Policy.
Note that your IT Security Policy is a very different document from your company's Privacy Policy. A Privacy Policy is a public-facing document that gives notice to your customers about how your company processes personal information.
A Privacy Policy should include information about the safeguards you implement to protect personal information, but it serves a much broader purpose than your IT Security Policy.
Does Your Company Need an IT Security Policy?

Any company with more than a handful of staff will find its data becomes spread out over numerous PCs, mobile phones, and other devices. This sort of situation can become messy very quickly.
Companies of any significant size should create an IT Security Policy. Even if it's a fairly brief document, it's important that you ensure all your staff are on the same page when it comes to data protection.
Is an IT Security Policy Required By Law?
There are many laws and regulations that set rules about cybersecurity and data protection.
The laws to which your company and its employees are subject will depend on where your company is based, and the sector in which it operates. Some examples include:
- California: Data Breach Security Reporting law (available here)
- New York: SHIELD Act
- European Union and United Kingdom: General Data Protection Act (GDPR)
- United Kingdom: Data Protection Act 2018, Computer Misuse Act 1990 (available here)
- Canada: Personal Information Protection and Electronic Documents Act (PIPEDA)
Not all of these laws require every company to produce a written IT Security Policy. However, they do require companies to safeguard the information under their care. They also require companies to be able to demonstrate their compliance with the law. An IT Security Policy can help achieve this.
What are the Benefits of having an IT Security Policy?

There are many benefits to having an IT Security Policy:
- It ensures all members of staff understand the importance of IT security
- It sets clear rules for managing and using IT equipment
- It helps you formulate strategies and procedures for keeping your company's data secure
- It reduces the chances of a data breach
- If a data breach does occur, an IT Security Policy can help you respond quickly and effectively
It is in the interests of your company, its staff, and its customers to ensure your IT security practices are clear and robust.
What to Include in Your IT Security Policy

The contents of your IT Security Policy will depend, to some extent, on the nature of your business. However, there are some sections that are common to most IT Security Policies.
Purpose and Objectives
Setting out the purpose and objectives of your IT Security Policy serves as an introduction to the policy.
You should first state the basic, overarching purpose of your IT Security Policy, namely, promoting information security by setting out the rules on the use of IT equipment within your company.
Here's how the Care Quality Commission does this (at page 4):
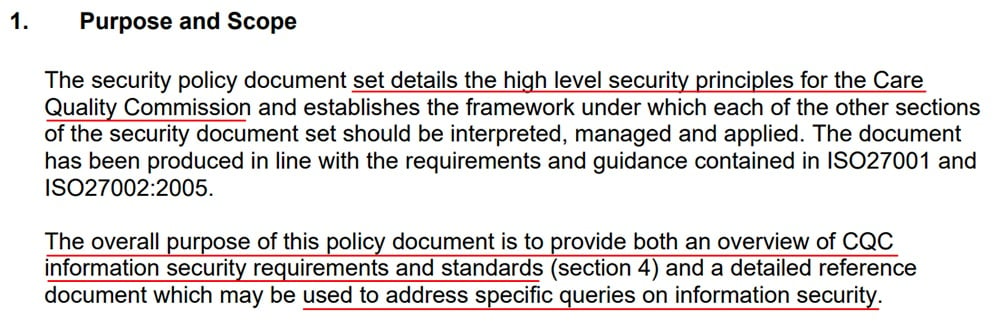
In this section of your IT Security Policy, you can also introduce the concept of the "CIA Triad." The CIA Triad is the classic model of information security and is central to many IT Security Policies. The three elements of the CIA Triad are:
- Confidentiality
- Integrity
- Availability
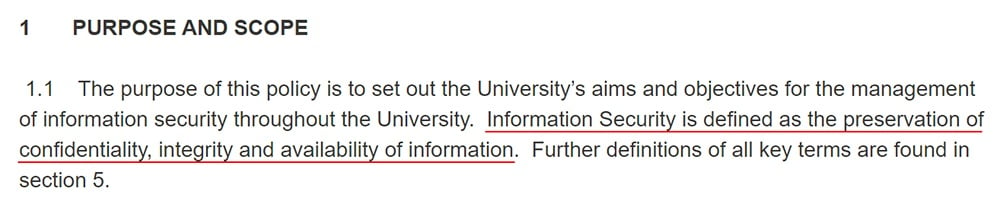
You don't need to go into detail about the nature of information security. You can simply note that the aim of your IT Security Policy is the preservation of the confidentiality, integrity, and availability of information.
Here's how Cardiff University does this:
Scope
In the "scope" section of your IT Security Policy, you should explain who the document applies to.
The scope of your policy may include all permanent and temporary members of staff at your company, and may also include contractors, employees of subsidiaries or partner companies, etc.
Here's how NHS England does this (at page 7):

Applicable Laws
Above, we looked at some of the laws that regulate IT security. It's important to figure out which laws apply to you, and inform your staff of their responsibilities under these laws within your IT Security Policy.
Here's an example from Aston University (at page 11):

Roles and Responsibilities
Your IT Security Policy should set out who is responsible for managing IT security within your organization. It should also establish the responsibilities of all other staff who are not directly involved in implementing the policy.
Take a look at this section of University College Cork's IT Security Policy (at page 6). It establishes the IT Director as responsible for managing the policy, and states that staff and students at the institution are responsible for adhering to the policy:
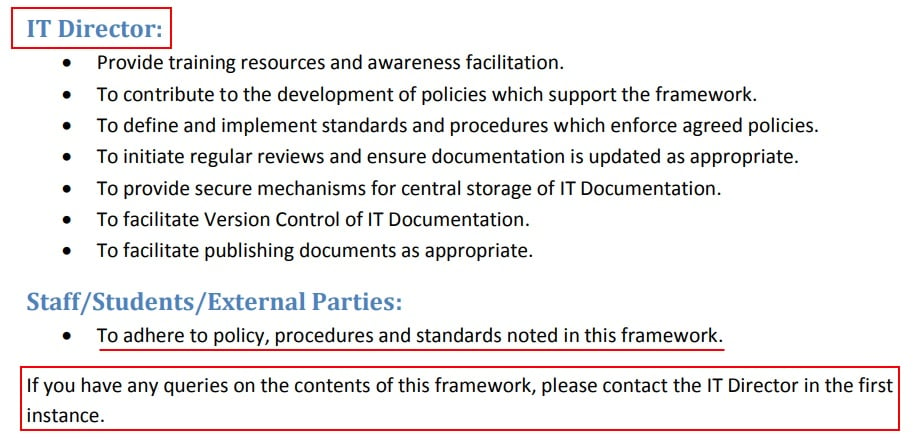
Note that the policy also advises staff to contact the IT Director if they have any questions about the policy.
Procurement of IT Equipment
You need to ensure a high level of information security when your company purchases new computers and other devices.
Your IT Security Policy can set specific standards for newly-procured IT equipment, or else it can state that all IT equipment purchases are subject to approval by a specific member of staff.
Here's a section from the IT Security Policy of South Kesteven District Council explaining the organization's rules about the procurement of IT equipment (at page 10):

The organization requires that all new IT equipment is approved by relevant members of staff, and assessed to ensure it serves a clear business purpose and does not represent a security risk.
Anti-Malware Software
You should ensure that all IT equipment has anti-malware equipment installed. This will help protect your company against viruses, spyware, and the increasingly common threat of ransomware.
Here's an example from Grande Prairie Regional College (at page 7):

Note that the organization requires anti-malware protection to be centrally managed. This would require a business-oriented anti-malware product that allows an IT administrator to manage multiple endpoint terminals.
Backups
You'll want to regularly back up important or sensitive data in case your systems suffer a technical error of data breach.
Your IT Security Policy can provide instructions to your employees regarding how often, and in what manner, they should back up your company's data.
Here's an example from iCIMS:
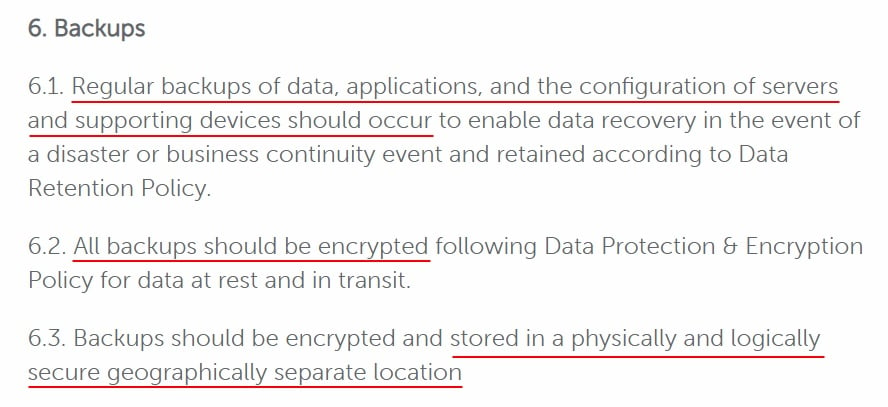
As noted by iCIMS, it's important to keep backups secure. Backups are a common target of cybercriminals.
Network Security
Your company's network is a key entry point for malware, cyberattacks and other threats.
Your IT Security Policy can set out the rules for using and connecting to the network. In this section, you can set out rules around:
- The conditions of connecting to your company's network (e.g. agreement to your Acceptable Use Policy)
- Who may connect to the network (e.g. staff or registered users only)
- What devices may be connected to the network (e.g. only company equipment)
- Administration of the network (e.g. allocation of IP addresses, etc.)
Here's an example from the IT Security Policy of Trinity College Dublin:
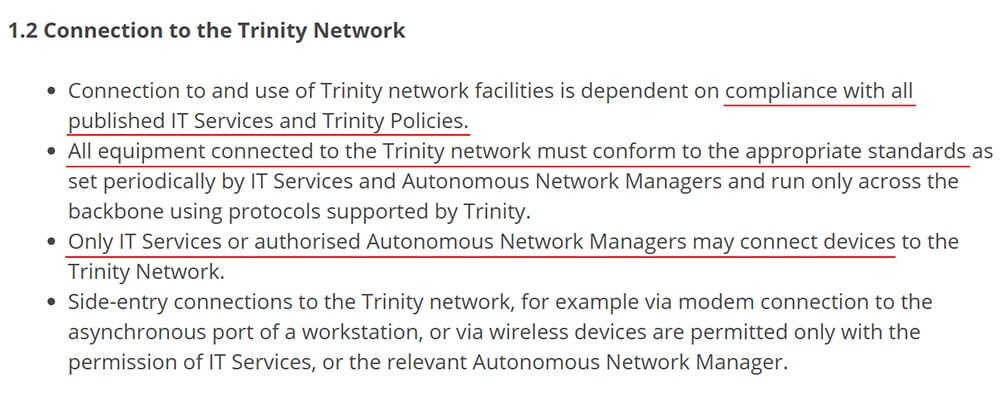
Use of Email
Hackers and scammers often target company email accounts. They can be a key vulnerability in your company's security.
Your IT Security Policy can set out the terms of use for your employees' company email accounts, including rules about:
- Not sending spam emails via the account
- Being vigilant about phishing scams
- Always having up-to-date anti-malware software installed on any device on which they access their company email account
Here's an example from Harrogate CCG (at page 5):
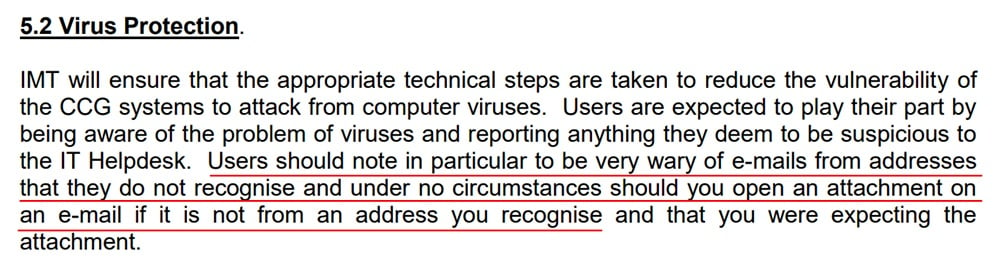
Use of the Internet
Your IT Security Policy should provide rules and guidance about how your staff use the company internet, for example:
- Rules about what websites employees may visit during working hours
- A prohibition on using the company internet for illegal activity
- A notification that on-site internet activity may be monitored
Here's an example from Newcastle NHS Trust. Here's how the organization notifies its staff that their internet usage will be monitored (at pages 2 and 7, respectively):

And here's a list of some of the prohibited categories of websites:

Password Security
Weak passwords are by far the biggest cause of data breaches and security issues within companies. Your IT Security Policy can set the rules about:
- The minimum number of characters your employees' passwords must have
- The frequency with which your employees must change their passwords
- Whether your employees must use password management software
You should also make it clear that your staff are prohibited from sharing their passwords.
Here's a relevant extract from the IT Security Policy of NHS Gateshead (at page 14):

Remote Access
Your staff will likely require access to work resources when working from home or otherwise working off-site.
You should ensure that remote working doesn't compromise the security of your company's systems. Your IT Security Policy can explain that:
- Employees using personal devices for work activities must ensure their devices are secured by anti-malware software
- Employees must ensure their operating system and applications are up-to-date
- When working remotely using public Wi-Fi networks, employees must not transfer sensitive company data
Here's an example from the University of Central Lancaster (at page 12):

Data Breach Response
Your staff must understand what to do in the event of a data breach. Acting quickly can significantly decrease the harm caused by a breach, as well as any resulting penalties or reputational damage.
Many organizations have a separate Data Breach Policy, but you can include your company's policy on data breaches within your IT Security Policy.
This section of your IT Security Policy should include:
- Information about whom employees should report to in the event of a suspected or actual data breach (e.g. your IT Manager)
- Instructions of what action to take to contain the breach (e.g. taking certain systems offline, resetting passwords, revoking access rights)
-
A procedure for making an initial assessment of risk, to determine:
- Who is affected by the breach
- What types of data have been compromised
- The cause of the breach
- Who must be notified (e.g. the individuals affected, the police, regulators)
- A procedure for assessing the severity of the breach
- A procedure for notifying the relevant authorities and/or individuals affected
- A post-breach evaluation process
Here's an example from the University of New South Wales (at page 2):
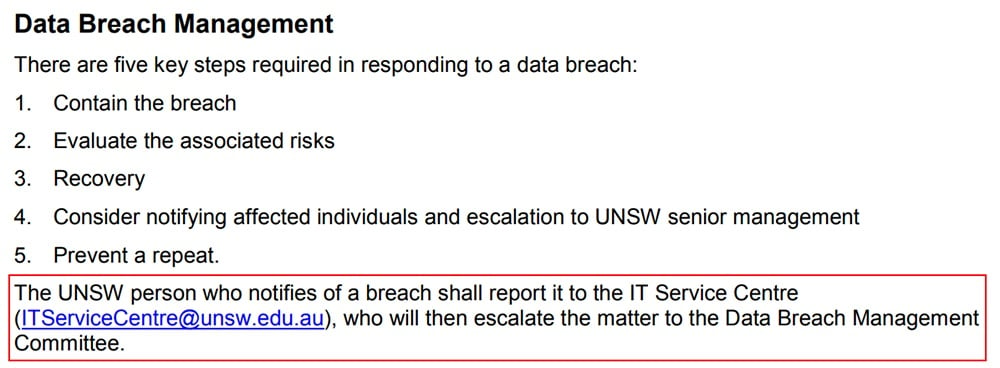
Summary of Your IT Security Policy
An IT Security Policy can help you keep control over your company's data and ensure its assets are not misused.
Some key sections of your IT Security Policy include:
- The purpose and objectives of the policy
- The scope of its application
- The applicable laws governing employees' use of IT equipment
- The roles and responsibilities of staff members
- The process for backing up company data
- Network security standards
- Rules governing the use of company email accounts
- Rules governing the use of the internet on company equipment/premises
- Password security standards
- Rules governing remote working/working from home
- The process for responding to a suspected or actual data breach

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.




