Your privacy protection practices go beyond having a good Privacy Policy.
That's just one tool to protecting your company from liability and communicating expectations with users, but it's not effective if you do not have the business policies to back it up.
That is where Privacy by Design (PbD) enters the picture. In addition to advocating for sound agreements and good communication, it also recommends systems to assure that the information you collect from users remains safe.
Here's an overview of PbD and how to implement it into your own practices.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
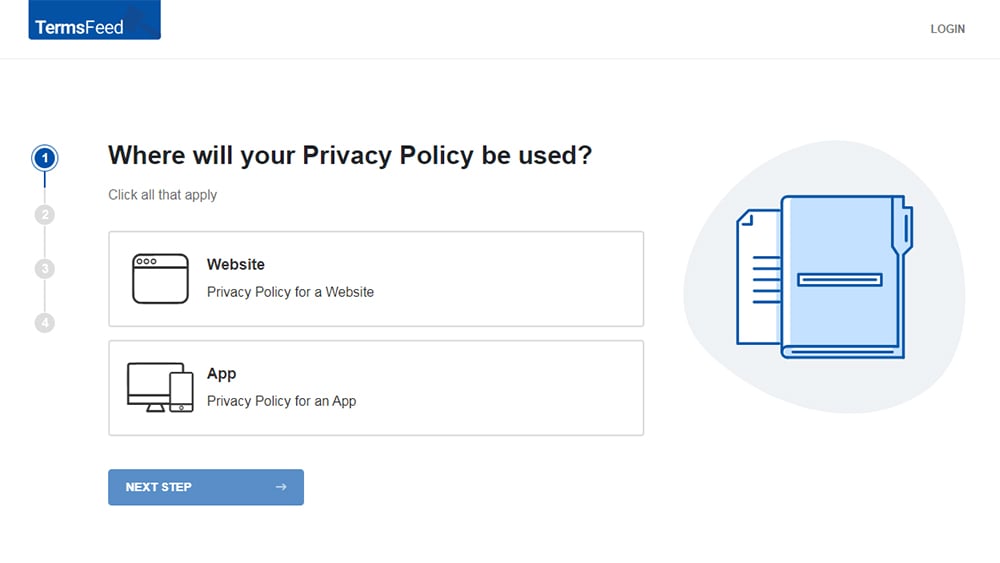
At Step 1, select the Website option or App option or both.
-
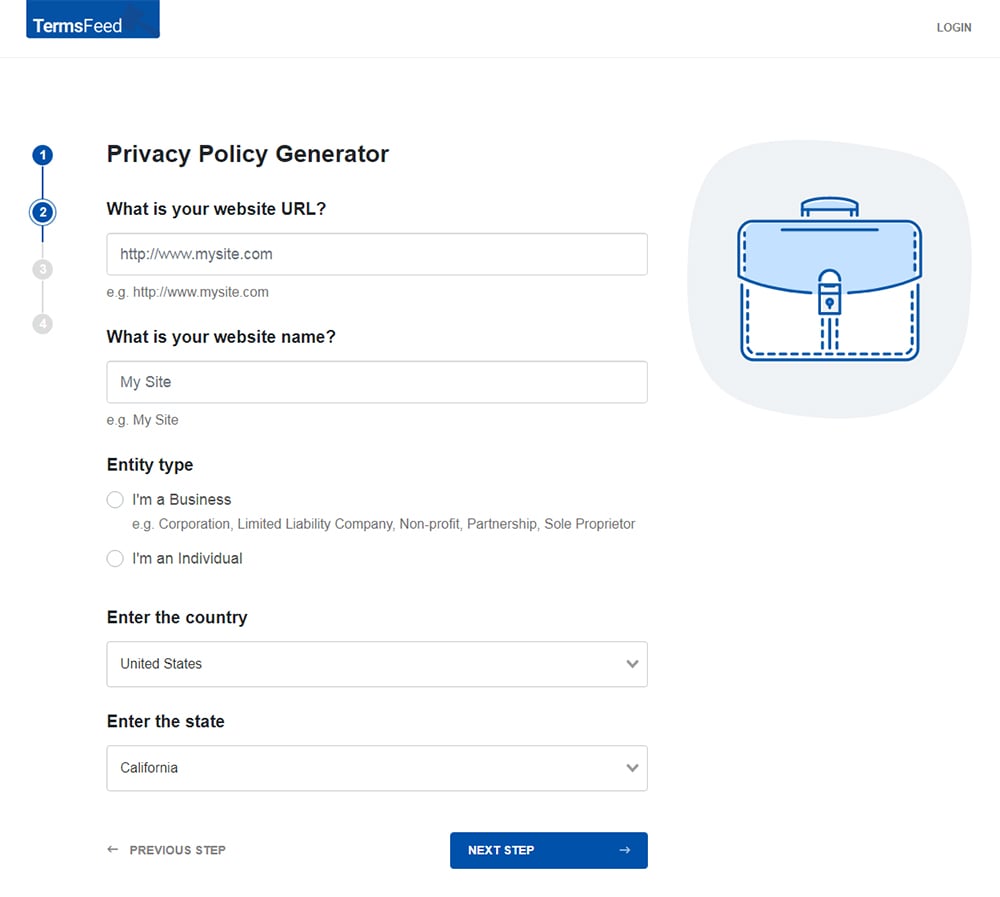
Answer some questions about your website or app.
-
Answer some questions about your business.
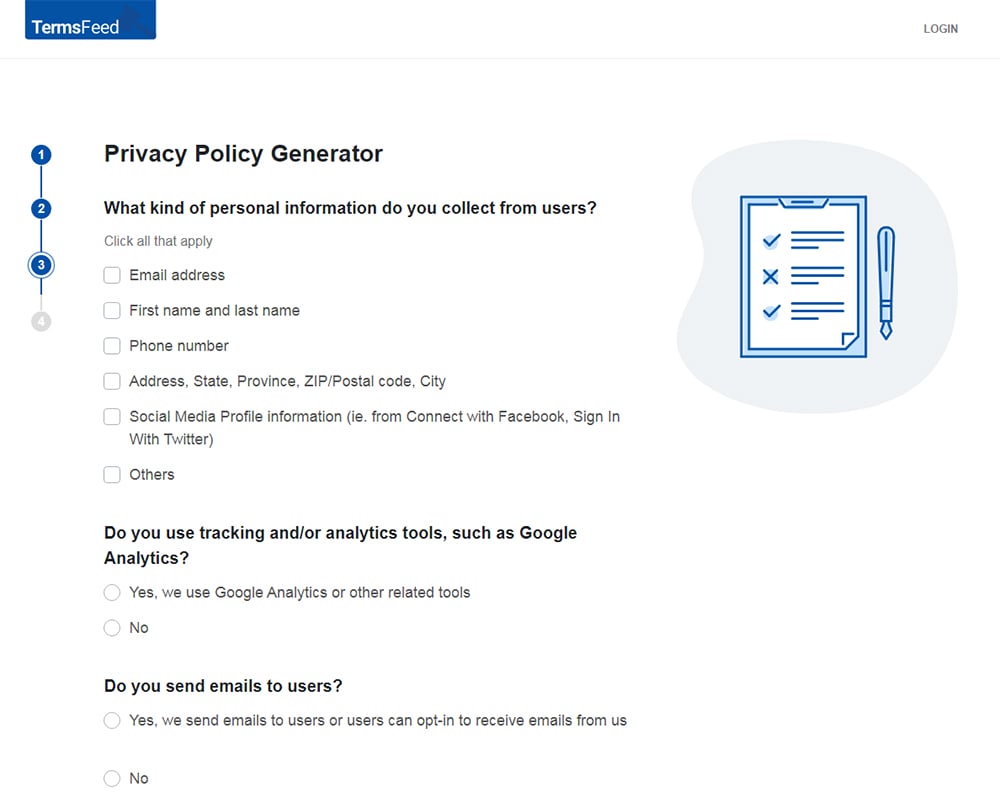
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
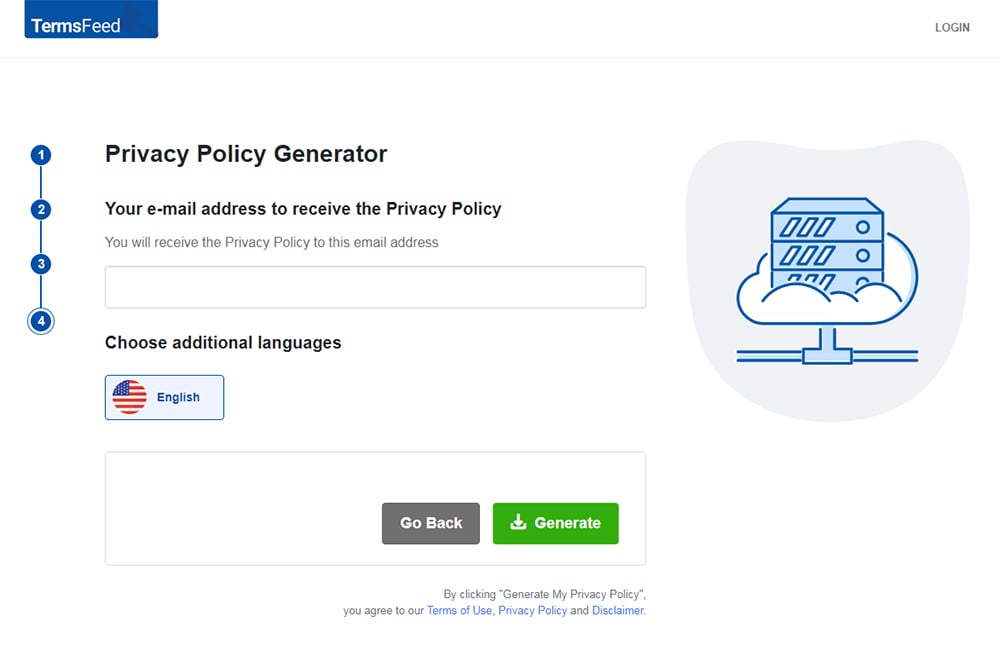
You'll be able to instantly access and download your new Privacy Policy.
- 1. Who is Privacy by Design For?
- 2. What is Privacy by Design?
- 2.1. Evolution of Privacy by Design
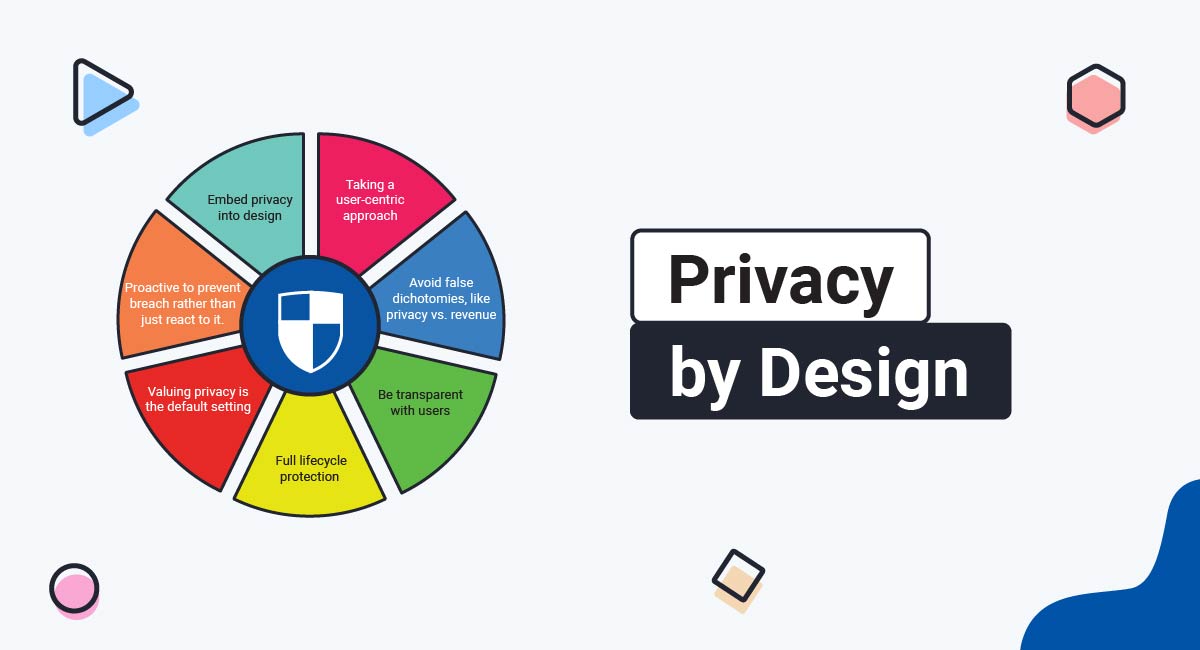
- 2.2. Foundation Principles of Privacy by Design
- 2.2.1. 1. Proactive to prevent breach rather than just react to it.
- 2.2.2. 2. Valuing privacy is the default setting
- 2.2.3. 3. Embed privacy into design
- 2.2.4. 4. Avoid false dichotomies, like privacy vs. revenue
- 2.2.5. 5. Full lifecycle protection
- 2.2.6. 6. Be transparent with users
- 2.2.7. 7. Taking a user-centric approach
- 3. Laws on Privacy by Design
- 4. Privacy by Design cheat sheet
- 4.1. Assess the nature of the information you collect
- 4.2. Don't wait for a breach to make changes
- 4.3. Know your protection baseline
- 4.4. Design retention procedures
- 4.5. Review your encryption and authentication processes
- 4.6. Check your privacy lifecycle
- 4.7. Be open
- 5. Summary
Who is Privacy by Design For?
Privacy by Design is most applicable to data controllers, or those who decide what data is collected and how it is to be used.
What is Privacy by Design?
Privacy by Design advances data protection and privacy from the start, even in the design phase of an online service or app.
Besides the documentary requirements of Privacy Policies and good online explanations, it also includes integrating IT systems that securely store data, supporting privacy protection legislation and regulations, securing data sharing systems, and being careful with the use of personal data.
The guidelines around Privacy by Design offers many benefits that reassure consumers and protect your bottom line.
Evolution of Privacy by Design
Privacy by Design was invented by Dr. Ann Cavokian, the former Information and Privacy Commissioner of Ontario.
She developed the system after noticing that too many businesses deal with privacy protection shortcomings after a data breach. Very few developed measures to prevent data breaches or at least control the damage.
There were some entities that rested on the Privacy Policies as all they needed to assure data protection. However, only seven percent of users read the Terms and Conditions agreements before clicking "I agree" and Privacy Policies are likely neglected in the same way.
Users may not understand the privacy implications of using your app or service but still rely on you to protect your data. For this reason, alone, you need to do more.
That is where Privacy by Design proves to be a helpful guide.
Foundation Principles of Privacy by Design
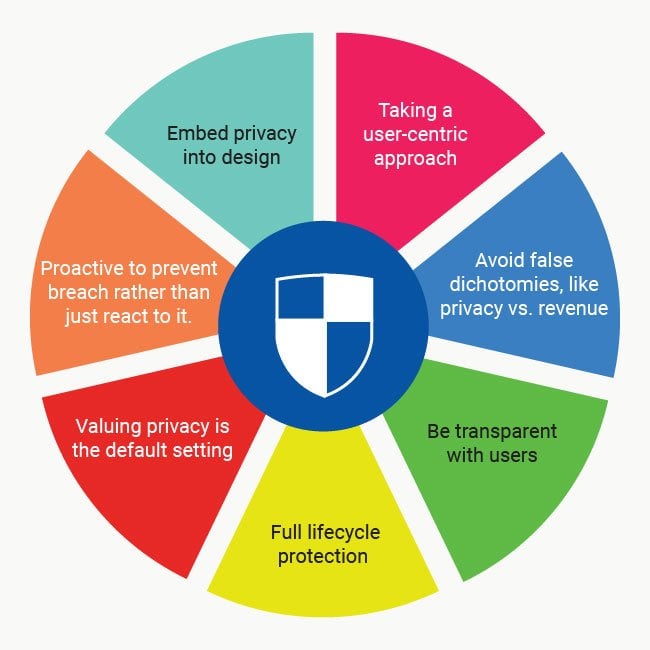
The principles of Privacy by Design are intentionally simple so they could be easily translated into other languages.
These are the seven principles.
1. Proactive to prevent breach rather than just react to it.
This is the foundation of Privacy by Design.
Since the previous trend was to respond to a privacy breach after it occurred, the better approach is to prevent it in the first place.
Privacy by Design recommends thinking of privacy at the beginning of app or online service development. If you have a product in development, consider the data collection, retention, and use procedures so you can also design the best way to protect that user information.
2. Valuing privacy is the default setting
This is often a difficult one for most developers. There is often a tendency to over-collect data rather than get just exactly what you need.
Using privacy as a default setting means you only collect necessary information, rather than what you think you might need in the future.
You can always make adjustments later and have your Privacy Policies and FAQs reflect that.
However, starting out with a bare minimum of data collection gives you less to protect and results in a less damaging breach - should one occur.
3. Embed privacy into design
You will likely find this principle challenging as well. This involves not only considering privacy a primary end but also implementing alongside with the functions of your service (website or app).
Your designers are likely most concerned with whether your app or service works. If features are added on, that concern continues - will this meet consumer expectations or we will continue to release patch updates until this works well? In addition to these concerns, your designers also have to integrate privacy protections.
Authentication and encryption must be embedded into design as much as functional capabilities. This would include testing for hacker vulnerabilities before you release your product!
Basically, privacy protection would be implemented at the same time as the functional capabilities.
4. Avoid false dichotomies, like privacy vs. revenue
It's possible to protect privacy and enjoy growth.
There are entities that see the cost of putting extra emphasis on privacy and worry about their bottom line. Make the effort to show that prevention is better than remedial strategies in that it avoids litigation costs and encourages user confidence.
5. Full lifecycle protection
The private information you collect will go through stages starting with collection or creation, sharing, and retention.
Protecting this data should happen at each stage; your responsibility does not end with sharing it. When you have kept it for as long as you need it, also assure the destruction of the data.
Encryption and authentication are the best ways to offer full lifecycle protection.
6. Be transparent with users
Earning the trust of your users is one reason to adopt Privacy by Design.
Write your policies in lay language and make headings clear in your privacy agreements. You want users to know what to expect with the handling of their information but you also want to avoid appearing untrustworthy. Vague policies written in legal language will give them that exact impression.
7. Taking a user-centric approach
Remember each time you collect data, that information belongs to your users. They are giving it in trust to you so you can perform a service for them.
Never forget that while they may click the right boxes to give you permission, they can revoke that authorization at any time.
Laws on Privacy by Design

Following Privacy by Design offers four distinct advantages:
- Reduced chance of legal liability
- Better regulatory compliance
- Protecting your business reputation and brand
- Preserving customer confidence and loyalty
However, its practices are well-suited to ensuring compliance with current laws because they demand that you go beyond the requirements and take an effective big-picture approach to privacy protection.
These laws include:
-
The GDPR. The GDPR was the first privacy law that truly emphasized principles of Privacy by Design and made it a common practice. Soon, other laws followed.
-
The Information Commissioner's Office (ICO) is a big advocate of Privacy by Design. While the agency is clear that following these guidelines is not required to be in compliance with the Data Protection Act, it is a helpful way to not only comply with the act but exceed expectations.
-
Canada (Ontario): Freedom of Information and Protection of Privacy Act. Since the founder is a former Information and Privacy Commissioner of Ontario, you could say Canada is the birthplace of Privacy by Design.
Being proactive also ensures compliance with this act as well.
-
Canada: PIPEDA - PIPEDA has principles that are founded with the spirit of Privacy by Design.
-
US: Federal Trade Commision (FTC) recommendations and other laws.
The FTC published a report recommending the adoption of PbD principles. It advocated for it based on consumer protection while recognizing the risks of the free flow of data. In addition, the U.S. has several federal laws regarding the protection of personal data.
The point of the FTC report was to point out that many of the recommendations in PbD would also help companies comply with the current laws that protect personal information.
Privacy by Design cheat sheet

Assess the nature of the information you collect
Your company should always be aware of the privacy effects when adding new features or upgrading your website or mobile app.
Staying aware will help you design more effective privacy protection.
This includes whether you are collecting just enough data for your service to operate. If your data requests go beyond what is needed for users to make optimal use of your service, then you need to reduce your data collection demands.
You should only request as much as need - not as much as you want. That reduces the amount of data you need to collect and the chances of disclosing it inappropriately.
Don't wait for a breach to make changes
Privacy needs to be considered in the design stage, not when something goes horribly wrong. When you take a reactive rather than proactive approach, your money will go towards PR campaigns and defending class action lawsuits. Trust from consumers can be impossible to earn back if you get it back at all.
If you form an effective preventative approach before launching your product, that will also cost money but offers rewards of consumer confidence and lower legal bills. Encourage your designers to take privacy of data in account at the beginning and make that a habit. It may take the time to realize the benefits of this but trust that they are definitely there.
Even if your product is not new, you can still make a proactive plan to protect data. Perform an audit to see where you can do better with privacy and make it the default setting from this point moving forward.
This way, designers will feel like they can be candid about shortcomings and you can implement needed changes before something happens.
Know your protection baseline
At a minimum, your company should offer explicit opt-in and opt-out procedures, virus and malware protection to prevent security breaches, and restricted sharing ("need to know").
If there are holes in any of these policies, you must reassess your privacy priorities and adjust them so you are communicating clearly with users and keeping their data safe.
Design retention procedures
Privacy protection is not limited to data collection. It also extends to data retention. If you only require data for a certain amount of time, make policies that allow that retention but destroy the data once it is no longer needed.
You may need to hire a security firm to assure the complete destruction of any data since the release of mirror data after destruction can still result in legal liability.
Review your encryption and authentication processes
If you make data available to third parties, be careful of your means of sharing it. Emailing records or providing the data through a nonpublic website address does not offer the same level of security as encrypting data or using log-in procedures.
You should also consider requiring frequent password changes so that users are not complacent about security. If there are doubts on whether your security protocol is effective, consider hiring an outside firm to perform an audit on your procedures.
Authentication can be as easy as setting up a login process.
Deloitte offers consulting services, including those associated with Privacy by Design. It also offers authentication platforms so company resources are not misused. This is what they set up for company Lexis accounts:

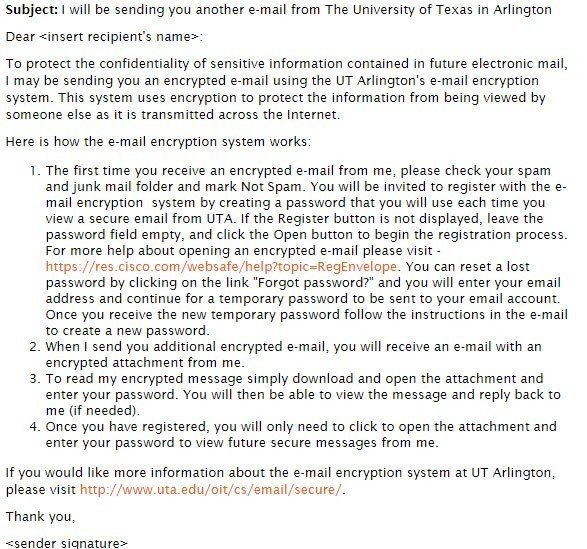
Encryption is often handled first through email. There is usually first an announcement email with instructions before the encrypted email arrives. This is the template used by University of Texas at Arlington:
Check your privacy lifecycle
You need to review privacy protection at each stage of the data's lifecycle.
This includes when you collect, create, share, and archive it. Do not neglect data at any step; your responsibility remains even when you share the information with a third party.
Authentication and encryption procedures offer protection but you should also know who actually requires access to this data. You need to have a strict policy of "need to know" when it comes to making users' personal information accessible and apply that uniformly at every stage of the data lifecycle.
Be open
Your users should be aware of your privacy practices. You can put this in your Privacy Policy but remember that only a small percentage of users may read the agreement.
If you trade in many types of information, consider setting up a Privacy FAQ.
Amazon collects fairly substantial personal information from its customers and offers a clearly explained Privacy Notice.
It is easy to navigate with questions and when a user clicks to one, they have the opportunity to read a simple explanation in layperson language.
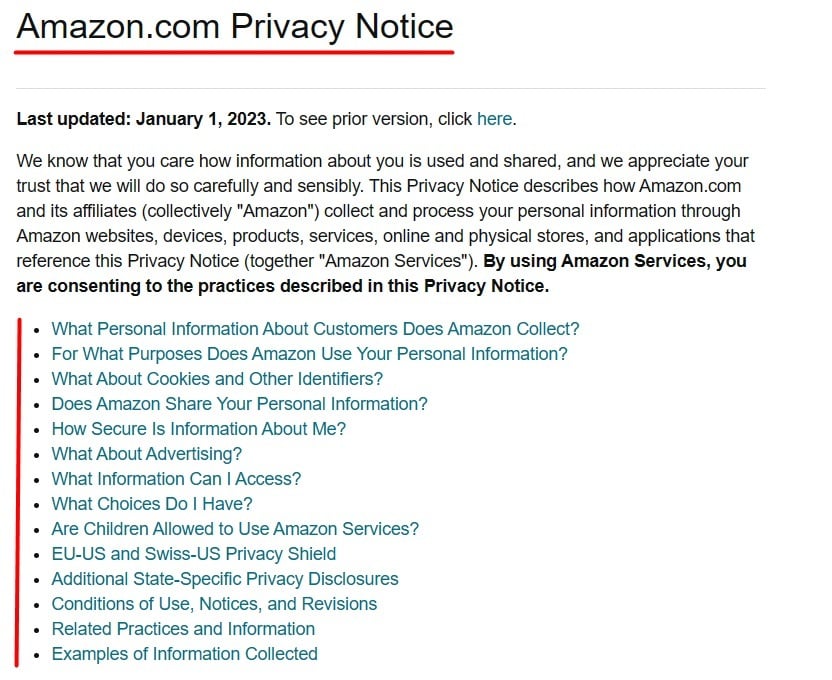
You want to keep all explanations focused on the consumer. If you offer vague language, it will appear that you wish to hide how you use consumer data. This could backfire badly in the long run so always be user-centric and transparent.
Summary
There is a reason Privacy by Design is so popular in this day of free flowing data and information exchange. It offers reassurance to your users but also protects your reputation, bottom line, and legal compliance. Look into how you can make data privacy a priority in your company today by practicing PbD.
Start at the beginning and assess all the data you collect and use, how you collect and use it, and how you secure it. Be open with your users about all of this by publishing a compliant Privacy Policy. And have plans in place for if or when a data breach does happen so you can quickly stop the damage and alert your affected users.
Practicing PbD principles can help you stay legally compliant, while helping push privacy rights and security for your users base.

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.