The EU General Data Protection Regulation (GDPR) imposes strict rules on transferring personal data out of the European Economic Area (EEA).
Before you make an international data transfer by sharing personal data with another organization outside the EEA, you must ensure that the organization can protect the data to EU-equivalent standards.
A Transfer Impact Assessment (TIA) helps determine whether a transfer is legal. A TIA is legally mandatory in certain circumstances.
This article explains the most authoritative version of the TIA: A six-step process devised by the European Data Protection Board (EDPB). It will break down each step of the process and let you know what you need to do.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
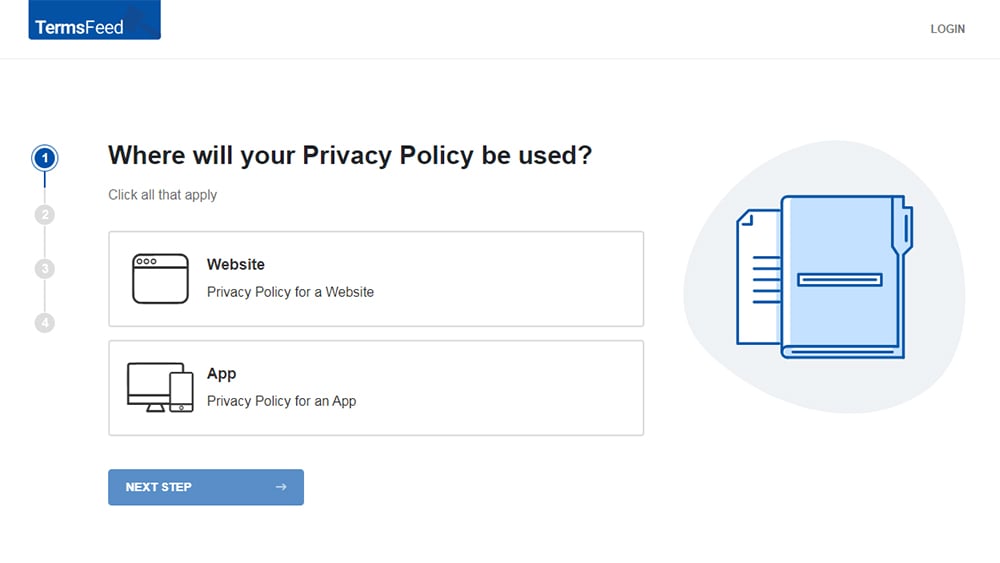
At Step 1, select the Website option or App option or both.
-
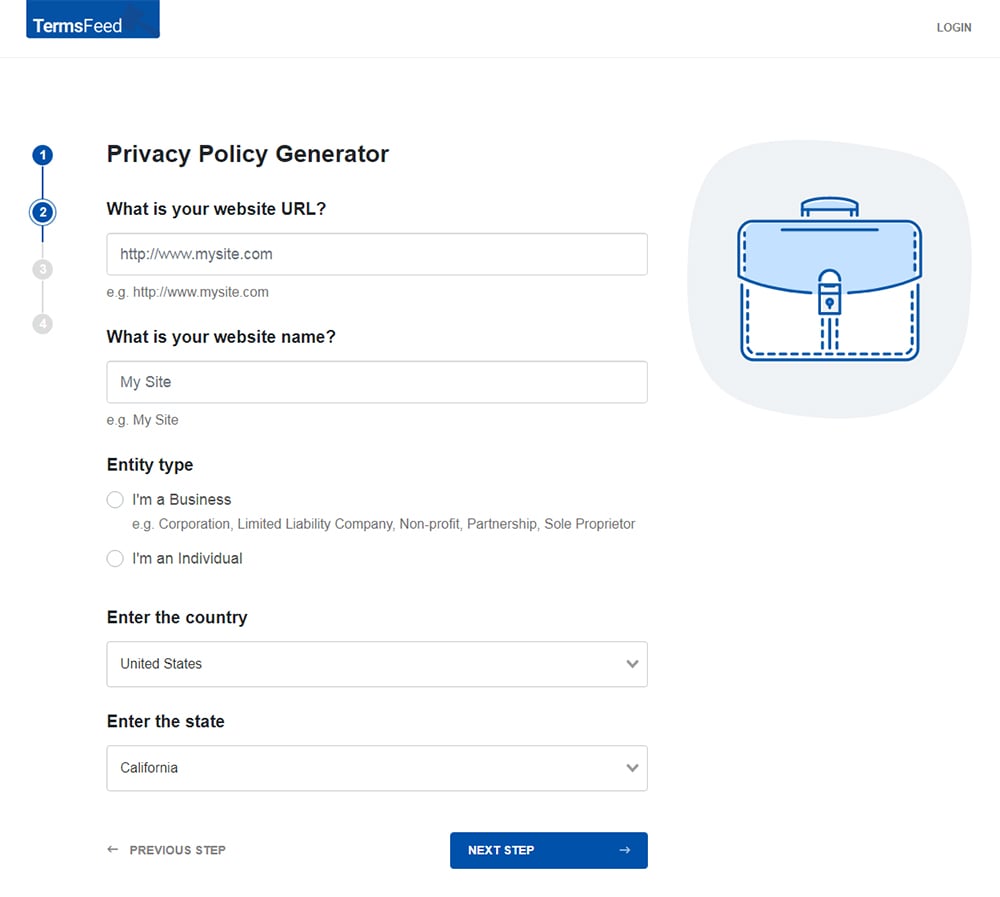
Answer some questions about your website or app.
-
Answer some questions about your business.
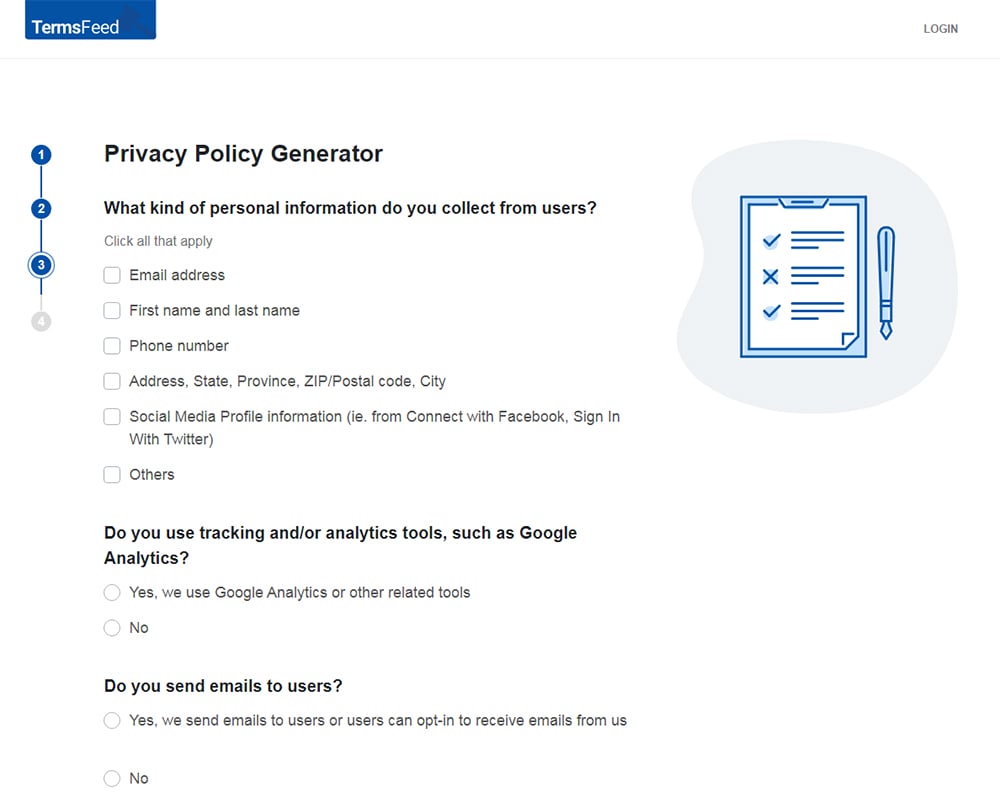
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
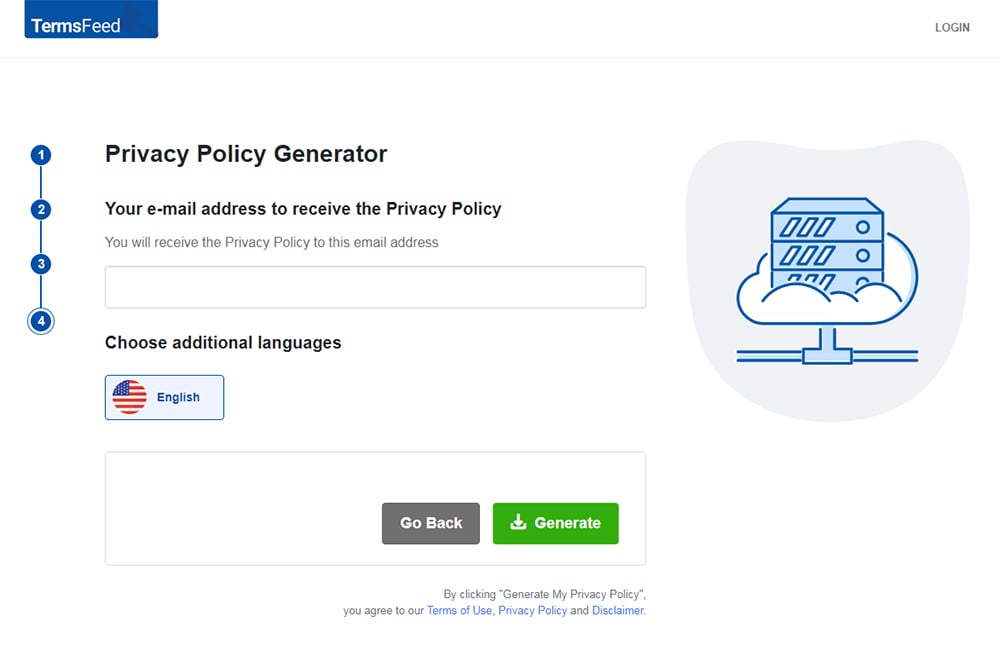
You'll be able to instantly access and download your new Privacy Policy.
- 1. International Data Transfers: A Brief Introduction
- 1.1. What are GDPR Transfer Tools?
- 1.2. How Does Schrems II Impact Data Transfers?
- 2. When is a Transfer Impact Assessment (TIA) Required?
- 3. How Do You Do a Transfer Impact Assessment (TIA)?
- 3.1. What is the EDPB's Six-Step Transfer Impact Assessment (TIA) Process?
- 3.2. Step 1: Know Your Transfers
- 3.3. Step 2: Identify Your Transfer Tools
- 3.3.1. Standard Contractual Clauses (SCCs)
- 3.3.2. Transfer Derogations
- 3.4. Step 3: Assess Whether the Transfer Tool is Effective
- 3.4.1. Specific Circumstances of the Transfer
- 3.4.2. Identifying Relevant Third-Country Laws
- 3.4.3. Assessing 'Problematic Laws'
- 3.5. Step 4: Adopt Supplementary Measures
- 3.6. Step 5: Take Any Necessary Procedural Steps
- 3.7. Step 6: Re-Evaluate
- 4. Transfer Impact Assessment (TIA) Summary
International Data Transfers: A Brief Introduction
Before we describe when and how to conduct a TIA, we'll briefly talk you through the basics of international data transfers under the GDPR.
As noted, you generally may only transfer personal data out of the EEA if the data importer can keep the data safe in the third country (non-EEA country) in which it is based.
Some third countries, like Uruguay, New Zealand, and (partly) the United States, have an adequacy decision. This means the European Commission has determined the country has sufficiently strong data protection standards.
But to share personal data with an organization in a third country without an adequacy decision, you'll normally need to implement one of the GDPR's "transfer tools."
What are GDPR Transfer Tools?
The GDPR's transfer tools (also known as "transfer safeguards" or "transfer mechanisms") are set out at Article 46:

The most common transfer tool is known as standard contractual clauses (SCCs) (highlighted in green). Binding corporate rules (BCRs) (highlighted in blue) are also relevant to the TIA process, but they are only used by large, international enterprises.
SCCs are contractual terms written by the European Commission. You can put these terms into a contract between your organization and the organization to which you intend to transfer personal data.
SCCs are legally binding. They seek to ensure that the data importer protects the data to EU standards.
For example, under the SCCs, the data importer must:
- Help you fulfill data subject rights requests
- Apply GDPR-strength security safeguards
- Only allow "public authorities," such as the government, police, or intelligence services, to access the data under certain conditions
The first two points are achievable. But keeping personal data safe from public authorities is not always possible. That's where a TIA comes in.
How Does Schrems II Impact Data Transfers?
In July 2020, the Court of Justice of the European Union (CJEU) interpreted the GDPR's data transfer rules in a case known as Schrems II.
The CJEU invalidated an adequacy decision in respect of the U.S., known as "Privacy Shield." This issue was solved (perhaps temporarily) three years later with a new US adequacy decision called the EU-U.S. Data Privacy Framework (EU-U.S. DPF).
The CJEU stated that before carrying out an international data transfer under SCCs (and certain other transfer tools), organizations ("controllers" or "processors" under the GDPR) must:
- Assess whether SCCs are effective
- If not, put "supplementary measures" in place or suspend the transfer
The TIA process comes from this part of the Schrems II judgment.
When is a Transfer Impact Assessment (TIA) Required?
You must do a TIA if all three of the below conditions apply:
-
You are making an international data transfer
- This means you (the "data exporter") are sharing personal data with a separate organization in a non-EEA country (the "data importer").
- The data importer is in a third country not covered by an adequacy decision.
-
You intend to use SCCs or another Article 46 "transfer tool"
- You might be covered by a "derogation," in which case you won't need to do a TIA. We'll come back to derogations later
Most organizations make international data transfers regularly, for example, when using email service providers, cloud storage companies, or payroll services based outside the EEA.
How Do You Do a Transfer Impact Assessment (TIA)?
The best source for conducting a TIA comes from the EDPB's Recommendations 01/2020.
Here's an overview of the EDPB's guidance.
What is the EDPB's Six-Step Transfer Impact Assessment (TIA) Process?
The EDPB divides the TIA process into six steps:
- Know your transfers
- Identify your transfer tool
- Assess whether the transfer tool is effective
- Adopt supplementary measures
- Take any necessary procedural steps
- Re-evaluate
Step 1: Know Your Transfers
The EDPB's first TIA step is to get comprehensive oversight of what data you transfer, where you transfer it, and why.

Here are some pointers from this part of the guidance:
- Conduct a data-mapping exercise to understand where your data is going.
- Map out any "onward transfers" the data importer might make (by sending the personal data to another third country).
- Consider whether you need to make an international data transfer at all. The GDPR's principle of "data minimization" applies.
- Be aware that even allowing access to personal data from a third country can constitute a "transfer."
Step 2: Identify Your Transfer Tools
Next, you must identify which of the Article 46 transfer tools you intend to rely on.

Here's how iManage's TIA explains that the company relies on SCCs:

Standard Contractual Clauses (SCCs)
This article assumes you intend to use SCCs as your transfer tool.
The European Commission provides four SCC "modules" to be used in different situations:
- Module 1: Controller to Controller
- Module 2: Controller to Processor
- Module 3: Processor to Processor
- Module 4: Processor to Controller
You must decide which SCC module you need for your transfer.
Transfer Derogations
At Step 2 of its TIA guidance, the EDPB also mentions the GDPR's "transfer derogations:"
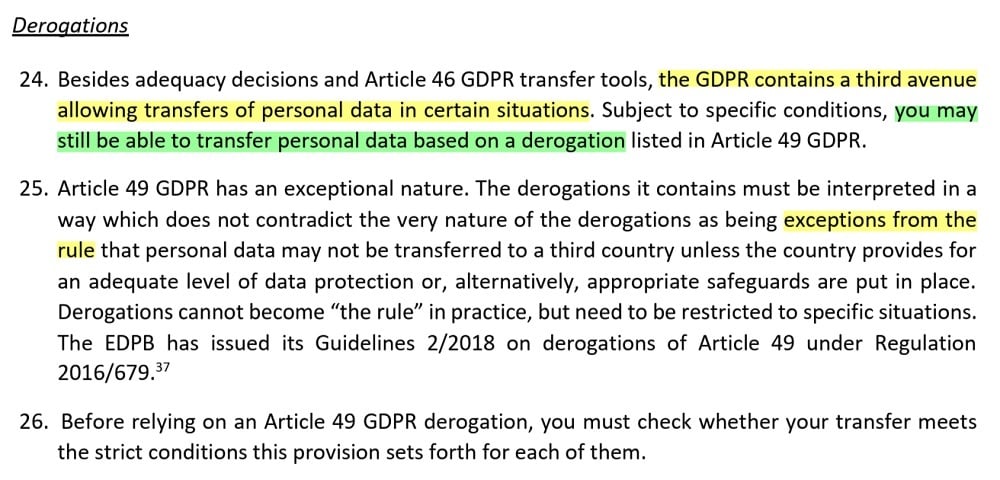
The derogations are exceptions from the international data transfer rules, and they're set out at Article 49 of the GDPR:

We won't cover the derogations in detail, as they are only for exceptional circumstances. But if your transfer falls under one of the derogations, you don't need to use a transfer tool or do a TIA.
Step 3: Assess Whether the Transfer Tool is Effective
At Step 3, the EDPB recommends you assess whether your transfer tool is effective "in light of all circumstances of the transfer."
This might be the trickiest part of the TIA process. Here's an excerpt from the EDPB's recommendations:

Before conducting an international data transfer, you must assess whether public authorities in the destination country could access the personal data, either by:
- Ordering the data importer to provide access to the data
- Intercepting the data en route to the data importer
How do you know whether public authorities could access the data? You have to do some research.
Specific Circumstances of the Transfer
First, the EDPB says you should consider the "specific circumstances of your transfer," including:
- Purpose of the transfer (e.g., marketing, HR, cloud storage)
- Nature of data exporter and importer (e.g. public or private sector, controller or processor)
- Sector (e.g., health, finance, marketing)
- Types of personal data (e.g., names, cookie IDs, "special category data")
- Location of the data, and the possibility of remote access (e.g. stored in France but accessed by an Indian service provider)
- Format of the data (e.g., plaintext, pseudonymized, or encrypted)
- Possibility of onward transfer to another third country by the importer
This assessment should consider all parties to the transfer, including the exporter, the importer, and anyone else who might access the data.
Identifying Relevant Third-Country Laws
Next, the EDPB recommends assessing the legal framework of the data importer's country. This part of the TIA process can get complex, and you may need to consider external legal advice.
The EDPB identifies two types of relevant laws:
- Laws requiring the importer to provide public authorities with access to personal data
- Laws granting public authorities powers to access or intercept personal data
Context matters. For example, a law requiring finance companies to report certain transactions to the police might not be relevant when transferring health-related data to a university.
You should also consider the general human rights situation in the third country, including:
- The "rule of law" - Does the country have an independent judiciary that can facilitate appeals against unlawful surveillance?
- The data protection framework - Does the country have a GDPR-like law that protects personal data against access by public authorities?
The EDPB provides some recommended sources of information about third-country laws in Annex 3 of its recommendations. Here's an excerpt from Annex 3:

Assessing 'Problematic Laws'
Once you have gathered information about the third country's laws, you'll need to assess whether any of the laws are "problematic" in the context of your transfer.
Laws might be problematic if they:
- Do not respect the "fundamental rights and freedoms" enjoyed under the EU Charter of Fundamental Rights
- Go beyond what is "necessary and proportionate in a democratic society" to safeguard important objectives (such as national security)
If there's a chance that personal data could be accessed by third-country public authorities operating under such laws (after considering "supplementary measures" at Step 4), the transfer cannot proceed (unless it falls under a "derogation").
On the other hand, some countries have a robust human rights framework underpinning otherwise problematic laws. If so, the transfer might be able to proceed.
There are likely to be many relevant laws in any given third country. Unfortunately, there is no centralized list of relevant laws provided by the EDPB, the European Commission, or any other official body.
However, the EDPB provides some guidance on how to assess third-country laws in its Recommendations 02/2020 (on the "European Essential Guarantees").
This excerpt from a TIA conducted by Innominate lists some relevant laws in the U.S., including the Fourth Amendment to the U.S. Constitution, the Wiretap Act, and the Stored Communications Act:

In this TIA, ContractSafe provides some (arguably generous) analysis of "FISA 702," a law specifically cited as problematic by the CJEU in Schrems II:

Remember: You don't currently need to do a TIA when transferring personal data to the U.S. as long as the data importer is self-certified under the EU-U.S. DPF. Here's the list of EU-U.S. DPF-certified U.S. businesses.
Step 4: Adopt Supplementary Measures
At Step 4, you'll need to figure out whether you can protect the exported personal data via "supplementary measures" (extra protections).
The EDPB identifies three types of supplementary measures:
- Technical: Techniques like encryption and pseudonymization designed to keep personal data confidential
- Organizational: Policies, procedures, and training that can help control access to personal data
- Contractual: Legally binding agreements that oblige the importer to protect the personal data
The EDPB states that organizational and contractual measures alone are unlikely to provide sufficient protection. Public authorities normally have extensive surveillance powers that override internal company policies and private contracts.
Here's what the EDPB has to say about staff training as an organizational measure:

You're likely to need technical measures to protect the personal data, both during the transfer and in the importer's country.
This excerpt from a TIA conducted by Akeyless sets out the company's technical measures:

The EDPB provides some "use cases" (scenarios) involving technical measures. Here's its Use Case 1:

In this scenario:
- The personal data is encrypted by the exporter using strong encryption
- The exporter has exclusive access to the decryption key
- The importer cannot access the personal data or the key, and neither can third-country public authorities
In this scenario, the transfer can proceed. But most data transfer scenarios don't look like use case 1.
Data importers typically need access to unencrypted personal data for analysis, technical support, or just the general provision of their services.
Such a transfer is covered in the EDPB's Use Case 6, in which:
- The importer is subject to "problematic laws" (see Step 3)
- The importer can access personal data "in the clear" (unencrypted)
In this scenario, the EDPB says it is "incapable of envisioning an effective technical measure to prevent that access from infringing on the data subject's fundamental rights."
In other words: There's no known technical measure to protect personal data in this scenario (or at least the EDPB didn't know of any in 2021), so the transfer can't proceed.
For this reason, many EU-based companies received sanctions for using popular digital products such as Google Analytics and Facebook Business Tools between July 2020 (Schrems II) and July 2023 (the passing of the EU-U.S. DPF).
While the problem is currently resolved for U.S. data transfers, the rules still apply to transfers to other third countries.
Step 5: Take Any Necessary Procedural Steps
If you have identified supplementary measures at Step 4, the EDPB's Step 5 requires that you take any necessary "procedural steps" to ensure these are effective.
This step is unlikely to be relevant if you're relying on SCCs.
But if you're implementing supplementary measures that contradict the SCCs (for example, additional contractual measures that clash with the data importer's obligations), you'll need to contact your Data Protection Authority (DPA) for advice.
Step 6: Re-Evaluate
Finally, Step 6 of the EDPB's TIA process is to "re-evaluate at appropriate intervals."
What's an appropriate interval? It depends.
The EDPB says you should "monitor" the conditions of your transfer on an "ongoing basis" and redo your TIA whenever something might affect the protection of personal data. For example, if the third country changes its law or the data importer relocates.
Transfer Impact Assessment (TIA) Summary
International data transfers are arguably the toughest aspect of GDPR compliance.
Conducting a TIA is a resource-intensive process, but it's mandatory when relying on a transfer tool such as SCCs.
Remember the EDPB's six-step TIA process:
- Know your transfers
- Identify your transfer tool
- Assess whether the transfer tool is effective
- Adopt supplementary measures
- Take any necessary procedural steps
- Re-evaluate

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.