If your business is registered in Australia or you have customers or end users in the Australian market, you must comply with Australia's Privacy Act of 1988.
This article looks at what this act requires while giving you practical steps and best practies for how to comply, including a breakdown of each of the privacy principles under the act. Following our guide will help protect your company from legal liability, potential fines and penalties, as well as customer mistrust.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
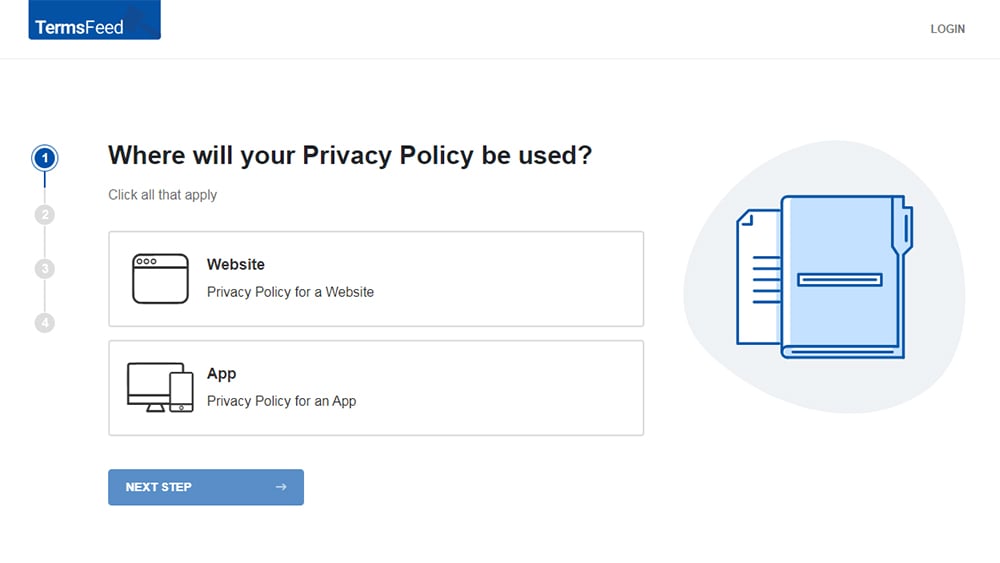
At Step 1, select the Website option or App option or both.
-
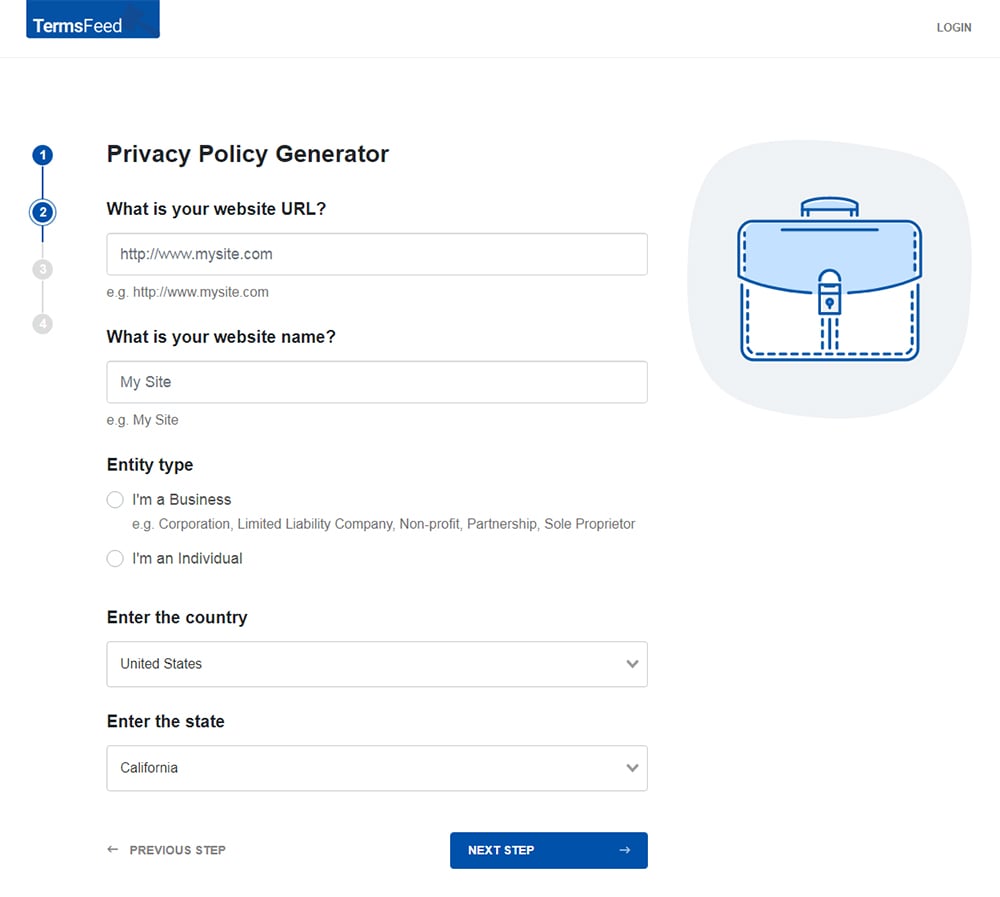
Answer some questions about your website or app.
-
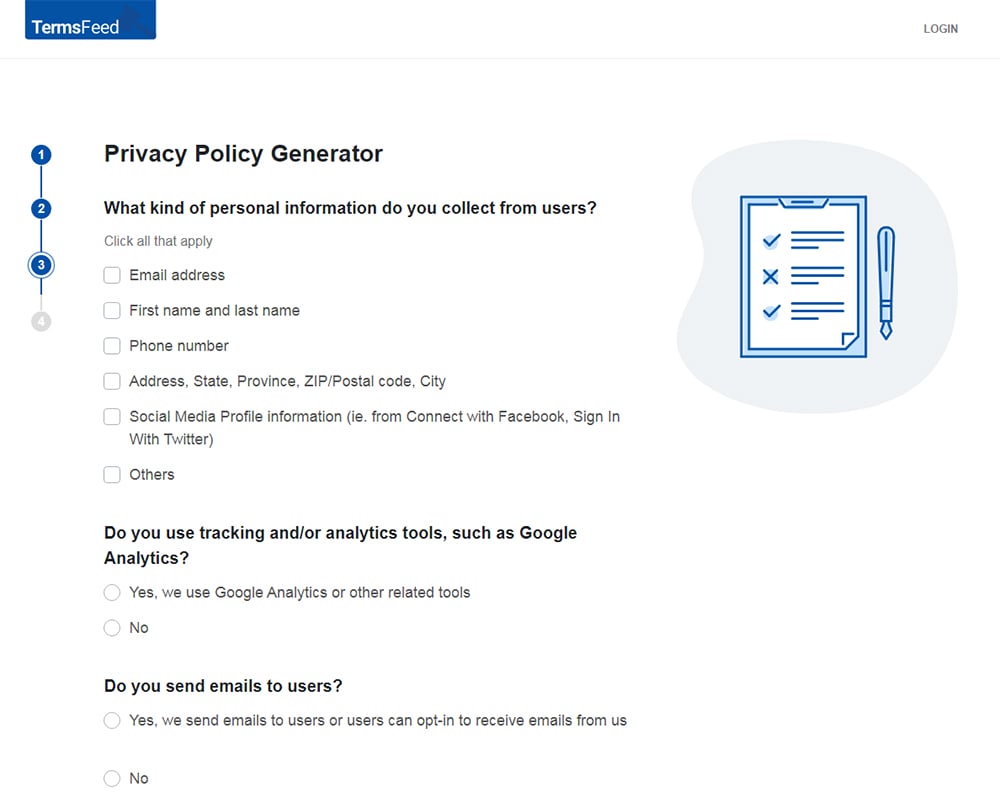
Answer some questions about your business.
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
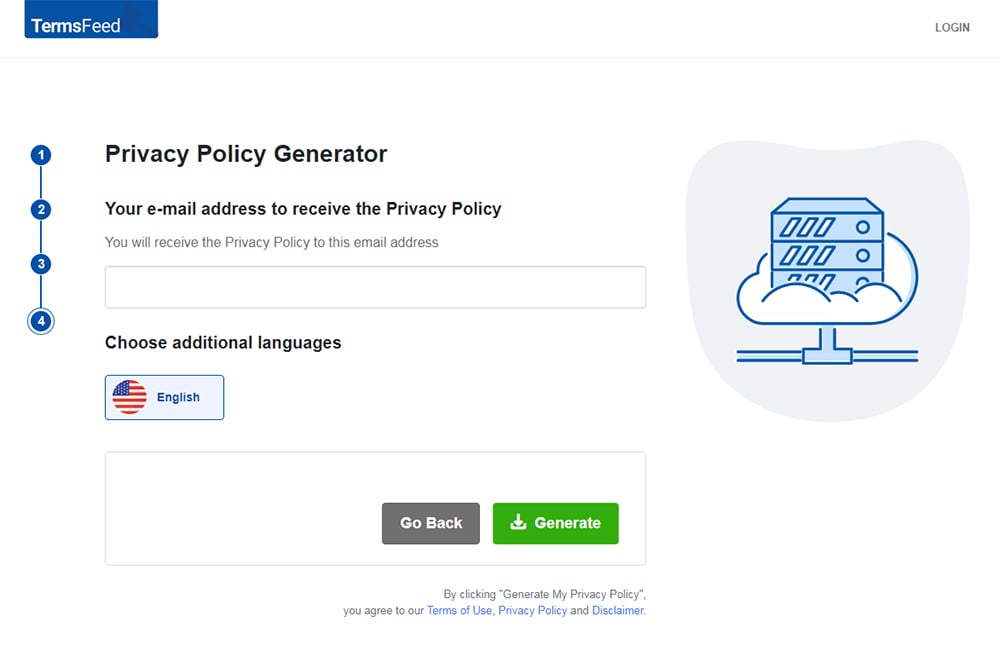
You'll be able to instantly access and download your new Privacy Policy.
- 1. Evolution of the Australia Privacy Act
- 1.1. Australia Privacy Act: Original 1988 Version
- 1.2. Australia Privacy Act: 2014 Updates
- 1.3. Australia Privacy Act: 2022 Updates
- 1.3.1. Increased Penalties
- 1.3.2. Expanded Reach
- 1.3.3. Enhanced Enforcement Powers
- 2. Australian Privacy Act Principles
- 2.1. Australia Privacy Act Principle 1: Be open and transparent
- 2.2. Australia Privacy Act Principle 2: Provide an anonymous or pseudo-anonymous option
- 2.3. Australia Privacy Act Principle 3: Know how to handle personal information
- 2.4. Australia Privacy Act Principle 4: Design an unsolicited personal information policy
- 2.5. Australia Privacy Act Principle 5: Keep users informed
- 2.6. Australia Privacy Act Principle 6: Address how to use or disclose personal information
- 2.7. Australia Privacy Act Principle 7: Do not disclose for direct marketing purposes
- 2.8. Australia Privacy Act Principle 8: Follow principles always, even when dealing outside Australia
- 2.9. Australia Privacy Act Principle 9: Limit government related identifiers
- 2.10. Australia Privacy Act Principle 10: Keep personal information up to date
- 2.11. Australia Privacy Act Principle 11: Maintain security precautions
- 2.12. Australia Privacy Act Principle 12: Allow individuals access to their own information
- 2.13. Australia Privacy Act Principle 13: Maintain a process for correcting personal information
- 3. Australia Privacy Act Compliance Best Practices
- 3.1. Assess what personal information you actually need
- 3.2. Use layperson terms and be as clear as possible
- 3.3. When in doubt, obtain consent for collecting and processing information
- 3.4. Set up in-house information assessment systems
- 3.5. Be mindful of third party compliance
- 3.6. Display your contact information prominently
- 3.7. Perform data security audits
- 4. Summary
Evolution of the Australia Privacy Act
The Australia Privacy Act was originally enacted in 1988 due to concerns about the availability of records to unauthorized individuals. It underwent changes in 2000, with updates outlined below in 2014 and 2022.
This is how the act evolved.
Australia Privacy Act: Original 1988 Version

The original version of the Australia Privacy Act was limited to state agencies or companies that contracted with government offices. It expanded to include private companies in 2000 and its principles applied to them despite their government contract status.
Australia Privacy Act defines personal information as facts or opinions about an individual that made the identity of that individual apparent or reasonably ascertainable.
Generally, this would include names, addresses, numerical identifiers, birth dates, bank account details, telephone numbers, email addresses, and even rumors or gossip about a person's private life.
Ethnic identity, sexual orientation, gender, trade information, education, and other personal facts are considered sensitive information that falls under similar protection.
The 1988 version of the Australia Privacy Act was the beginning of enacting privacy principles. Before, there was no guarantee of privacy in Australia.
Called the "Information Privacy Principles or IPPs," there were 11 guidelines for handling information. They addressed the following topics:
- Manner and purpose of collecting personal information
- Solicitation for personal information from the individual concerned
- Solicitation for personal information generally
- Storage and security of personal information
- Information regarding records
- Access to records
- Altering records
- Record keeper duties to check accuracy of information before use
- Relevant purposes for personal information
- Limits on using personal information, and
- Limits on personal information disclosure
In 1988, the focus was on paper records since there were no cloud drives or massive data exchange that year as there is now. Needless to say, the digital revolution required privacy reforms.
Australia Privacy Act: 2014 Updates

Here's a brief summary of the 2014 updates of the Privacy Act.
A noteworthy change from this update was centered around covered organizations. While the updates in 2000 changed the law so it applied to private companies, the 2014 developments expanded that net further.
Covered entities now included any company of any size with a gross income of AUD $3M.
Companies may fall under the duties of the Australia Privacy Act even if they do not meet the revenue standard. These exceptions include:
- Personal information disclosed for benefit, service or advantage
- Personal information collected in order to provide a benefit, service or advantage
- Mobile applications that require an email address for account activation
- Special organizations, like health care providers, who handle a large amount of sensitive data
The other change to the law included expanding the 11 IPPs to 13 Australian Privacy Principles or APPs. These prove handy for guiding your entity to compliance. While the 13 new principles are similar to the original 11, they do a better job of taking the digital age into account.
Australia Privacy Act: 2022 Updates

In 2022, a string of severe cyber security breaches targeted a number of high-profile Australian corporations. This led to the expedited passing of the Privacy Legislation Amendment (Enforcement and Other Measures) Bill in December of 2022.
This bill enhanced and amended the Australia Privacy Act in three key ways:
- Increased penalties possible
- Expanded reach
- Enhanced enforcement powers for regulators and authorities
Increased Penalties
First, the bill increased the possible penalty amount for serious or repeated breaches of privacy for corporations or organizations from $2.22 million to the greater penalty of the following:
- $50 million,
- 3 times the value of any benefit that the corporation and any related corporation obtained, directly or indirectly, that can reasonably be attributed to the conduct that created the violation, or
- If the court can't determine the value of the benefit, then 30% of the adjusted turnover of the corporation during the breach turnover period for the violation
For purposes of the above, the "breach turnover period" is whichever of the following is the longer period of time:
- The 12 month period that ends at the end of the month when the violation was reasolved, or
- The period of time that starts at the beginning of the month that the violation occurred, and ends at the end of the month that the violation stopped
These penalty increases are designed to help incentivize compliance and decrease the likelihood of violations, and thus privacy breaches.
Expanded Reach
The second way this bill enhances the Australia Privacy Act is by expanding the reach of the act's extraterritoriality provisions.
Previously, a corporation that isn't located in Australia must "collect or hold" the personal information of Australian citizens in order for the Privacy Act to apply.
Under the 2022 amendment, corporations that "carry on business" in Australia will now be required to comply with the act's requirements, regardless of whether they "collect or hold" personal information of Australian citizens.
This is a controversial and strict change that may now put the Privacy Act in conflict with other laws, so this change is one to watch to see if it's amended further or dropped in time.
Enhanced Enforcement Powers
The third key effect of the bill is to enhance the Information-sharing powers of the Australian Information Commissioner. This will help facilitate engagement between regulators domestic and abroad, help keep consumers informed, and is intended to help authorities act more quickly, efficiently and effectively.
The Commissioner now has the authority to publish notices about data breaches when they occur, and have more involvement in ensuring anyone affected by the breach is appropriately informed of the breach. Corporations that experience a data breach can be compelled to have external reviews of their systems and corporate practices to ensure adequate protection against breaches.
Australian Privacy Act Principles

The Privacy Act has 13 privacy principles that must be adhered to by anyone who must comply with the act. The privacy principles help make sure personal information is being collected and used fairly, is being protected, and that users are aware of their privacy rights and given a way to exercise them.
If your business or organization implemented a Privacy by Design approach, you are already ahead with meeting these 13 principles as many of the concepts are shared.
However, if you are still considering making internal changes compatible with Privacy by Design, carefully review these principles if any part of your business occurs in Australia.
Australia Privacy Act Principle 1: Be open and transparent
You are required to open and transparent with your users about the information you collect and how you use it. Explain clearly how you collect information, the purpose of collection, how you use it, how your user can correct any information, and any possible overseas disclosures.
Terms can be present in a Privacy Policy and that will likely meet your requirements.
However, entities that handle immense amounts of personal information also offer a privacy FAQ.
St. George Bank certainly handles personal information, as it is one of the largest banks in Australia. If you visit its Privacy Statement page, you'll find summary sections that help users find specific information on certain topics very quickly and in an organized fashion:
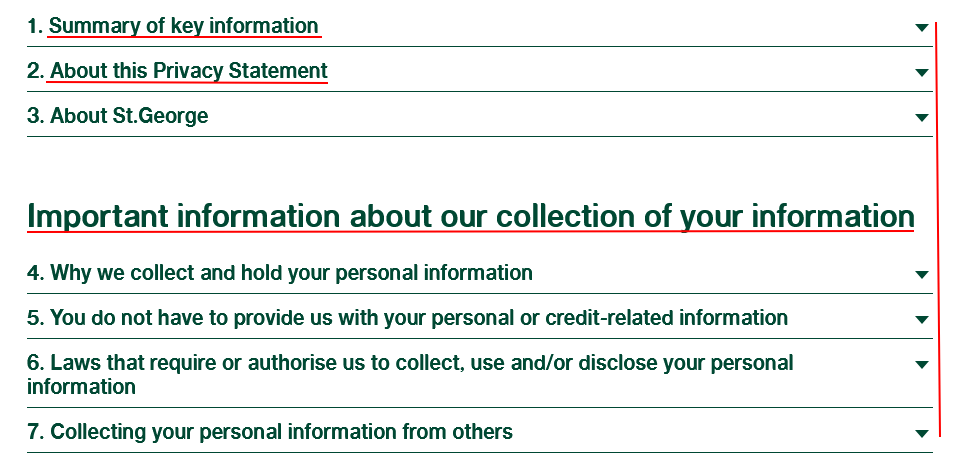
When you click on the arrows to the right of the section headings, you find a very clear and concise elaboration into the topic. Here's an example of the summary of key information section, where users can go to get an overview of the full Privacy Policy:

The actual long-form Privacy Policy is also available on the site as its own document.
Australia Privacy Act Principle 2: Provide an anonymous or pseudo-anonymous option
Individuals may wish to use a service under an alias or anonymous identity. As an online service (website or mobile app), you are required to provide this option unless it is impractical for you.
Obviously, a banking or insurance service cannot cater to anonymous or pseudo anonymous identities. For some services, this is less essential.
IYou may wish for personal information for targeted marketing or account maintenance. However, it may not necessarily be impractical if you bypass collecting it. In these cases, you likely want to provide the option for a user to remain anonymous or offer a pseudonym.
Australia Privacy Act Principle 3: Know how to handle personal information
This principle addresses the collection and sharing of information, including points like obtaining consent to collect and use data, and what scope of data you collect.
If you have the consent of the user to collect personal or sensitive information, the collection and use will be authorized. That's why if you are in doubt of whether you can collect information, you should attempt to secure consent first.
When it comes to collecting information automatically or without explicit consent, make efforts to only solicit information that's necessary for the transaction.
For example, asking a user about sexual orientation is not relevant when you are securing car insurance for them. However, date of birth, name, where they live, and types of cars they own is necessary information for an insurance policy.
Second, the transparency requirement in the first principle also applies to this one.
Little Tikes lists the following types of information collected voluntarily from people as well as the methods of collecting it in its Privacy Policy:
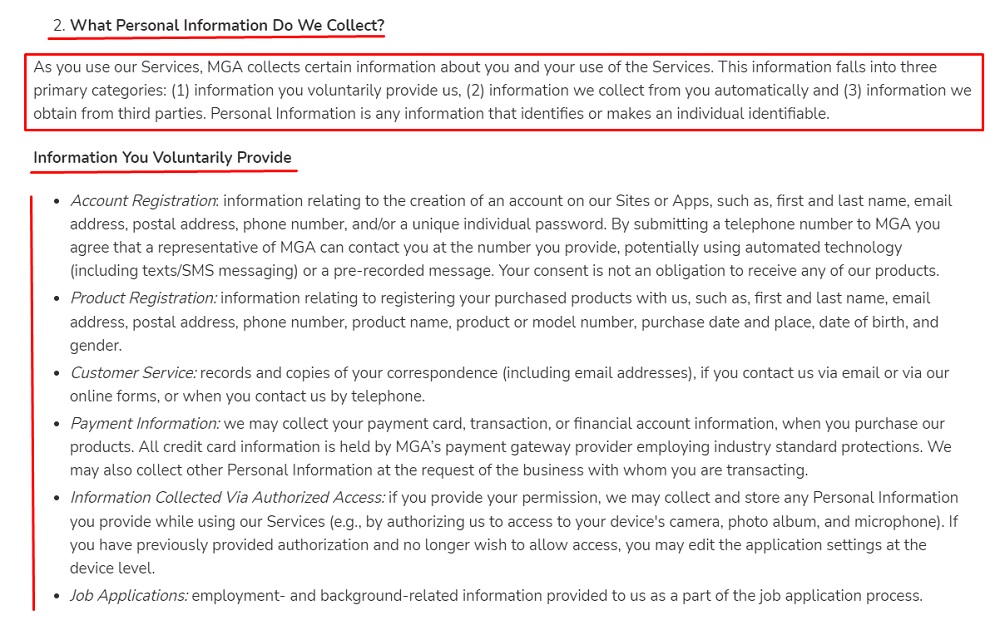
It also includes any information collected automatically, as well as from other sources such as third parties:
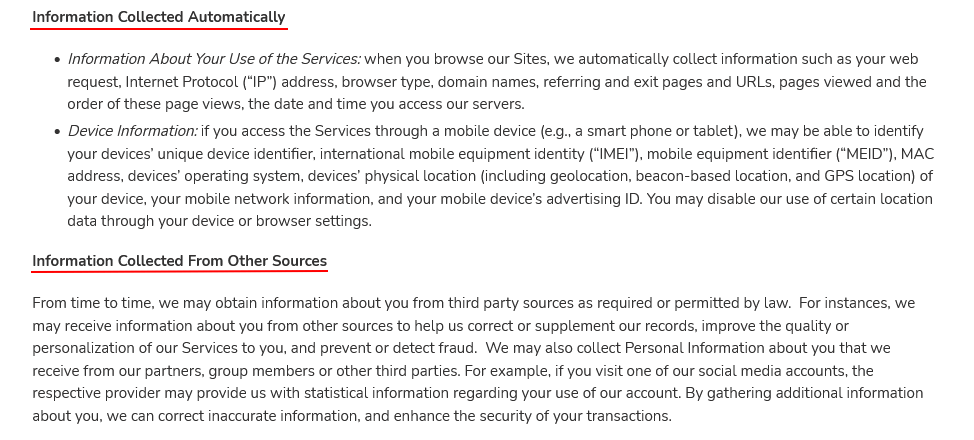
Australia Privacy Act Principle 4: Design an unsolicited personal information policy
You need an in-house process that deals with unsolicited personal information because sometimes a security breach or user error results in personal information being disclosed to you that you do not need to hold. Even though you did not ask for or solicit the information, there are still responsibilities when this happens, and these should be outlined in your policy or procedure.
Your first step is to determine if receiving the information was appropriate under Australian Privacy Principle 3. If that is the case, you can retain it.
However, if it is not appropriate for you to keep this information, then determine if it could be found in a commonwealth record. Arrest records and pending civil lawsuits, for example, are public record so you could conceivably find those facts in them if you looked. That would also be a lawful collection under the Australian Privacy Principle 3.
If the information does not fall under either of these considerations, then you need to destroy it or unlink the individual's identity from it. You will not be permitted to retain it.
Australia Privacy Act Principle 5: Keep users informed
Under this principle, you must take reasonable steps to notify users of certain matters. This include:
- Your company identity and contact details
- Any changes to information collection methods
- Legal changes that affects your information collection methods
- Changes in the purposes of information collection
- New information needed for your service and how it affects the functioning of new features
- Changes to your disclosures
- Privacy Policy updates
As expected, this mainly affects you when you change your Privacy Policy or when a new feature in your service requires additional personal information. These notifications must be reasonable meaning they can be email updates or pop-up updates on your websites.
Bridgecrest sent an email notice, shown below, that lets customers know that its Financial Privacy Notice was recently updated. While this was primarily aimed at a U.S. audience, this would meet the Australian requirements:
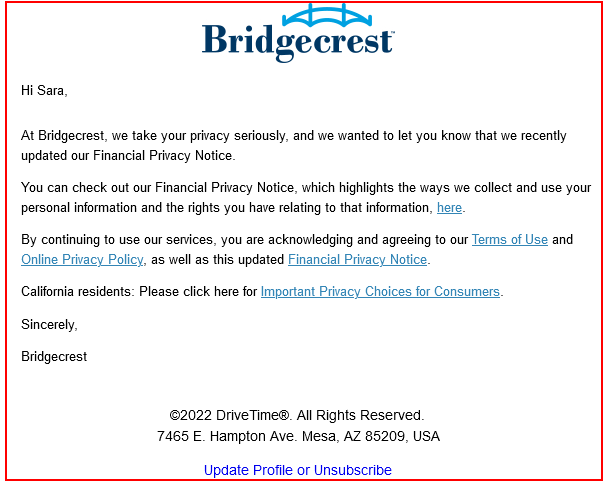
Australia Privacy Act Principle 6: Address how to use or disclose personal information
The act allows for the disclosure and use of personal information if that will satisfy the primary purpose for its collection. You are not allowed to disclose or use information for curiosity sake or for other purposes not connect to your business goals.
If there is a secondary purpose for use or disclosure, you must meet one of the exceptions. Most are connected to civil lawsuits or criminal activity and since you will normally receive a court order in these instances, you will likely understand your need to disclose.
In other cases, you need the consent of the user or at least set up a reasonable expectation that their information would be disclosed in this matter. Health situations, like sharing records between doctors, would be an example of the latter.
Apple explains in its Privacy Policy how it uses personal data in ways that may involve it sharing the data:
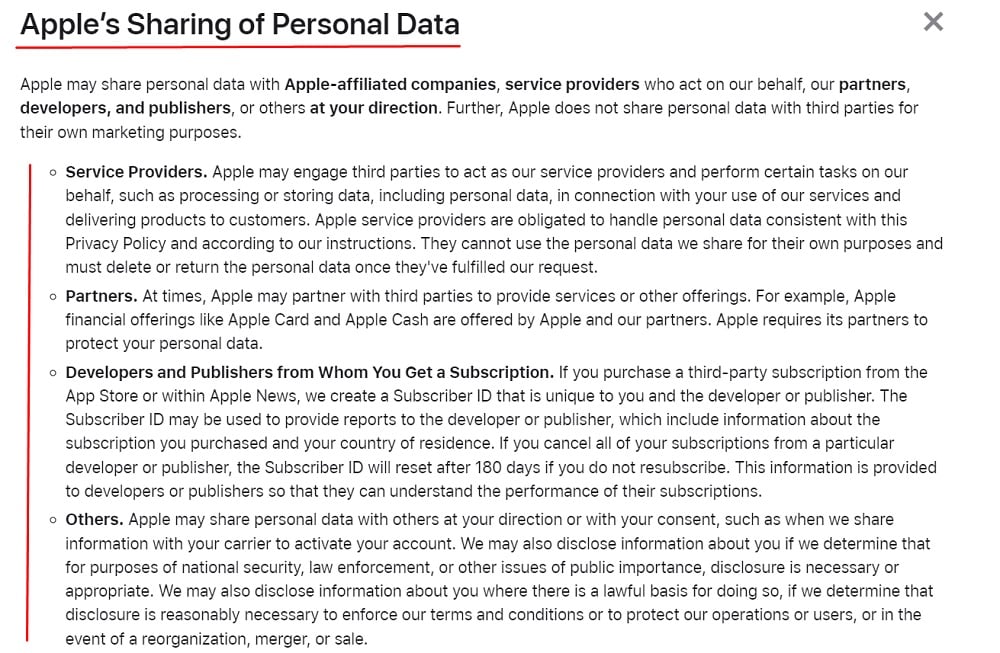
Australia Privacy Act Principle 7: Do not disclose for direct marketing purposes
Disclosure of information for direct marketing is generally not allowed. You can do so if you have consent through an opt-in procedure. However, you also need to offer users a choice to opt out.
Lowes Menswear discussing direct marketing in its Privacy Policy. It brings up direct marketing when it discusses disclosure of personal information:
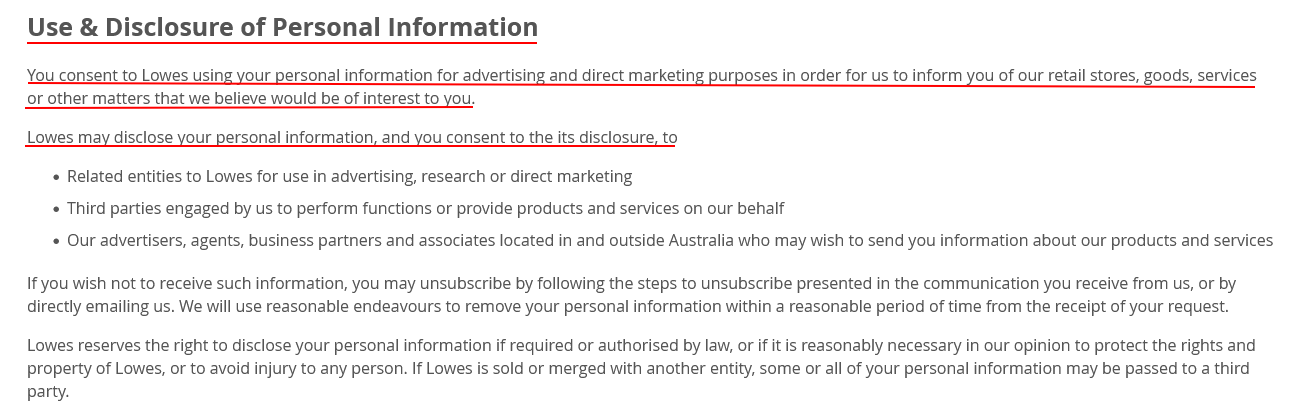
Notice that while it is clear that data will be disclosed, it also provides the opt-out procedure. A user also can email them and request removal from these lists. Under Australian Privacy Principle 7, Lowes must comply with that request in a timely manner.
Australia Privacy Act Principle 8: Follow principles always, even when dealing outside Australia
Overseas disclosures become tricky because the Privacy Act will no longer comply. While other countries have their own privacy laws, many Australian citizens will not be reassured by them. Therefore, you must follow the principles even as you disclose information to your overseas partners.
Part of this also includes informing users that this could happen. This does not have to be a particularly long part of the Privacy Policy.
Officeworks contains this short paragraph in its Privacy Policy and includes the countries of its partners:

Lowe's also embraces this step but does not name in particular partner countries:

Be aware if you disclose information overseas, your company will be responsible for any privacy breaches by your partner company.
You want to choose your foreign partners and vendors very carefully if you plan to disclose user personal information to them.
Australia Privacy Act Principle 9: Limit government related identifiers
The Australian Privacy Principle 9 restricts the use of government identifiers and includes a number, letter, symbol or any combination of those things to identify an individual. These are assigned by an agency, state or territorial authority, or contracted service provider of an agency or authority.
Since users are unlikely to be aware of or disclose these to you, there is only a small chance you will come across this situation.
Australia Privacy Act Principle 10: Keep personal information up to date
Since personal information can include opinions, it's important that you keep it updated and if notified of errors, correct it. You should take precautions to only collect accurate information in the first place but also take the additional step of allowing users to correct their personal information.
Here's an example of a type of clause you can include in your Privacy Policy that lets users know they have a role in keeping their personal information up to date, and gives them guidance on what to do if they wish to review or correct the information you hold on them:
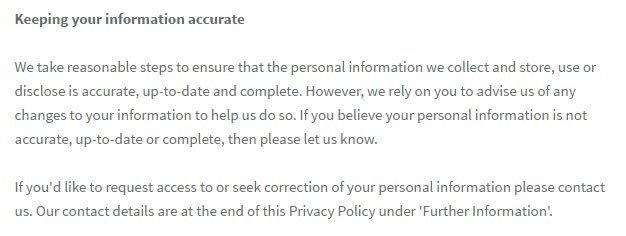
If you make decisions based on inaccurate information you can face liability. You want to assure accuracy when it is within your control but also make corrections quickly when you are notified of errors.
Australia Privacy Act Principle 11: Maintain security precautions
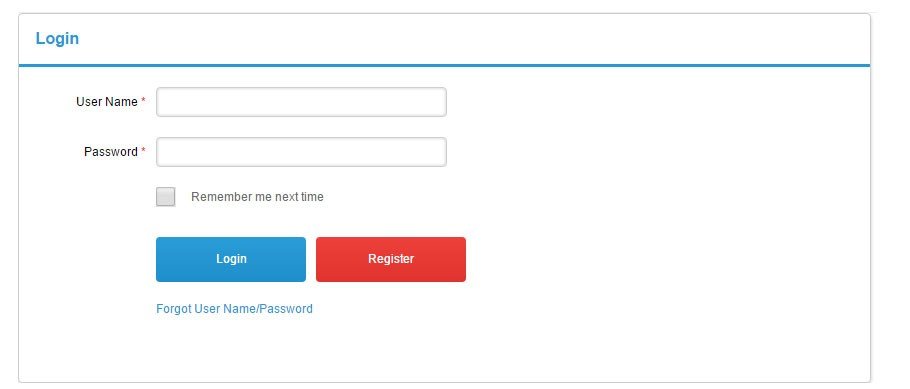
This privacy principle requires that you take steps to protect data from interference, loss, and misuse. Authentication, meaning a login screen with a username and password, is one way to control access. If you are dealing with very sensitive information, like providing banking notices to customers, you may wish to use encryption.
In most cases, providing a login and authentication is sufficient.
Here's an example of a common, best practice type of login screen that would be sufficient to providing front-end security. A user must enter both a user name and password to access an account and the protected, secured information within:
Australia Privacy Act Principle 12: Allow individuals access to their own information
Unless you have a compelling reason, you must allow users to access their own personal information. The only exceptions to this rule include government secrets and protected documents.
This is a common privacy right granted to individuals, and is something that you can disclose in your Privacy Policy.
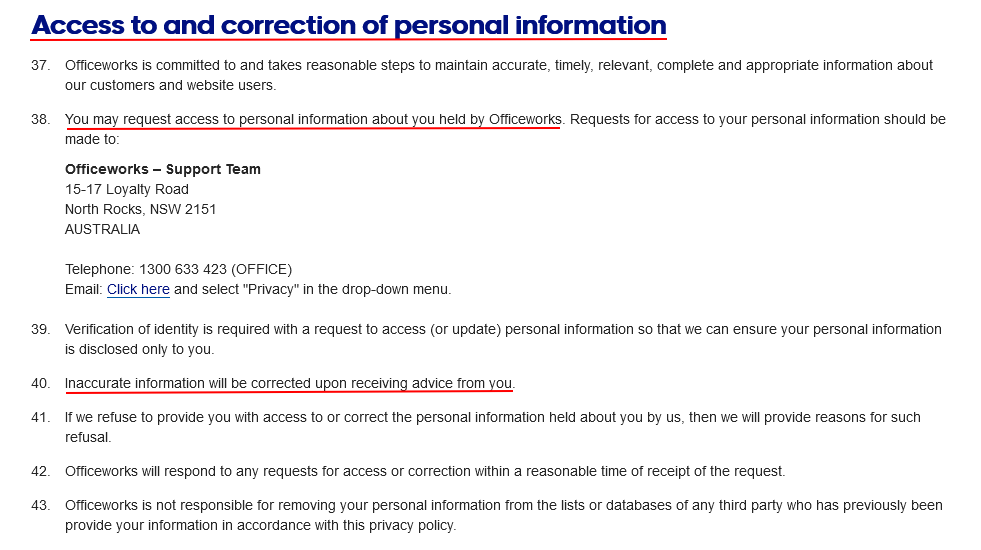
Here's how Officeworks offers contact information for users who want to view the personal information they hold as well as make corrections:
Australia Privacy Act Principle 13: Maintain a process for correcting personal information
This is similar to Australian Privacy Principles 10 and 12. Australian Privacy Principle 13 takes this idea one step further and requires that you have a process for fixing errors when you are notified of them or discover them.
As shown in the examples under Privacy Principles 10 and 12 above, Privacy Policies can be used to disclose to users how they can review their information and make corrections if errors are discovered.
You will need an in-house process for addressing these situations, especially when the error involves an opinion about another person.
Not only must you keep your own records accurate but any third parties that have access to the information must be informed of the changes.
Australia Privacy Act Compliance Best Practices

The Australian Privacy Principles listed above create a checklist for your privacy protection procedures.
In addition to following them, here are a number of best practices to follow as you navigate compliance with the Privacy Act.
Assess what personal information you actually need
When you collect more personal information than necessary to run your website or app, you risk exposing yourself to unnecessary liability. This is based on the simple formula that the more private information you collect, the more difficult it is to keep it safe.
That is why when you design the app you need to realistically assess what is needed to help it operate. The same is true for an ecommerce site or another online service.
When you add features or upgrade, reassess the need for information.
If you require more data from users, you will need to update your agreements and policies. However, if your changes lead you to require less information, that will likely make your business practices legal.
Use layperson terms and be as clear as possible
You should always write your legal agreements in layperson terms, avoiding legalese. Consider breaking down your full legal agreement such as your Privacy Policy into smaller components, such as an FAQ section, or a summary at the beginning of the full policy.
This all helps with transparency by making your policies clear and easy for anyone to understand.
When in doubt, obtain consent for collecting and processing information
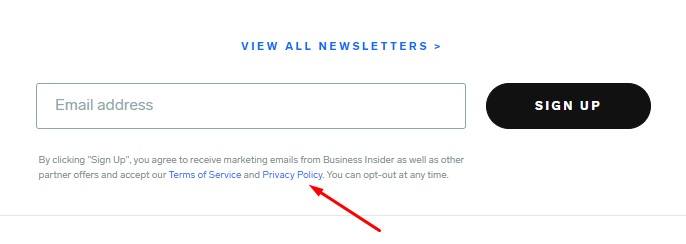
Consent overrules many restrictions under the Privacy Act and the Privacy Principles. Consider getting explicit consent to process personal information from individuals.
A commonly used method for this is to use an "I Agree" checkbox where appropriate, such as this example from Business Insider:
Set up in-house information assessment systems
Your company will have to assess information constantly. As mentioned, you'll need to determine if you are collecting just enough to provide your service. In addition, you also have to monitor it for accuracy and make corrections when errors come to your attention.
The best way to manage this system is to limit it to one department or employee whose main job is assessing information.
You always need to be aware of when your information needs change and keep up with those developments. That will help you remain compliant.
Be mindful of third party compliance
If you disclose personal information to third parties, only share with those who are also held to the standards of the Privacy Act or other robust privacy laws.
Display your contact information prominently
You need to be accessible to your user, whether it's to answer questions about your information practices or to receive requests for making data corrections.
Create separate email addresses if needed.
Here's how the Hormel Foods displays its contact information in its Privacy Policy:
Support better goodwill and compliance by keeping contact information visible, and including numerous different ways to contact you.
Perform data security audits
Checking your data protection measures frequently helps users trust you and keeps you in compliance with the principles. If you have specialists in this area, you can perform these audits in-house. However, it is often recommended that you hire an IT security consultant since they can often find shortcomings that you might miss.
The Privacy Act provides a good checklist with its principles. If you follow them plus apply these general good practices, you are likely to stay in compliance with the Privacy Act and reassure users that their personal data is safe with you.
Summary
Australia's Privacy Act is a long-standing privacy law that has been updated a number of times, including most recently in 2022. it applies not only to businesses located in Australia, but can apply to operators located outside of the country who have enough of a connection with Australian citizens.
The Privacy Act works to protect Australian citizens from privacy violations by requiring that 13 Privacy Principles be followed by anyone who the Privacy Act applies to.
These 13 principles address concepts of privacy ranging from consent to use personal information, so transparency of how information is collected and used, and help create an outline of steps to take to help ensure compliance.
By maintaining an accurate, detailed Privacy Policy, minimizing data collection, utilizing security protocols and giving users a way to contact you to exercise rights or ask questions, you will be on the way to compliance with Australia's Privacy Act.

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.