Over the last few years, data breaches increased worldwide. Even though many governments have placed a greater emphasis on securing data, hackers are almost always ahead of the curve, with security professionals playing catch-up.
Business owners and leaders of organizations worldwide have found cybercriminals applying techniques such as supply chain attacks, social engineering tactics, and various types of malware to get inside corporate systems to steal and expose information and ultimately make some cash.
The state of Vermont passed updates to its Security Breach Notice Act (the Act) which became effective July 1, 2020.
In the article below, we'll go over Vermont's data breach notification law, what it aims to do, whom it applies to, and what your business needs to do to ensure compliance.
Our Privacy Policy Generator makes it easy to create a Privacy Policy for your business. Just follow these steps:
-
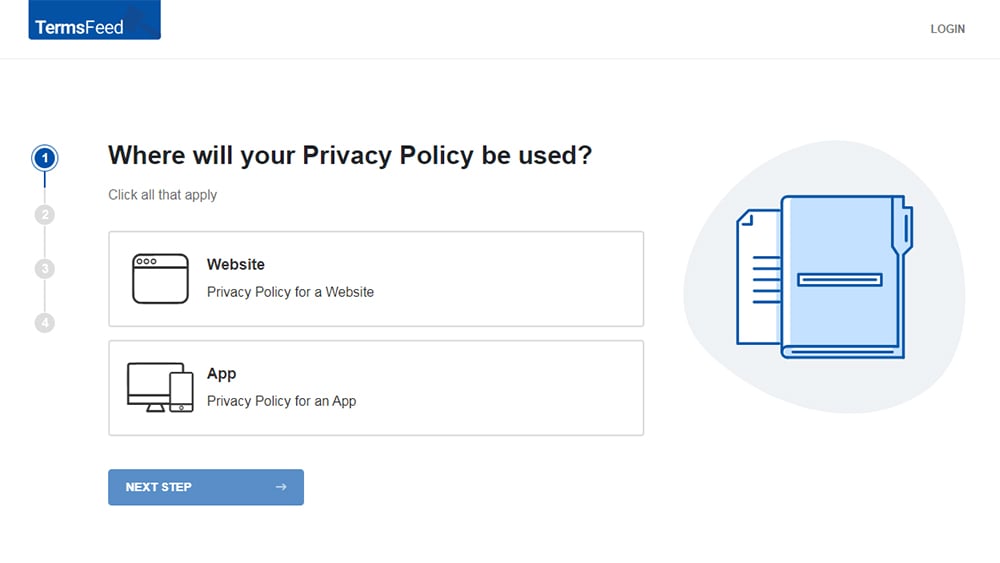
At Step 1, select the Website option or App option or both.
-
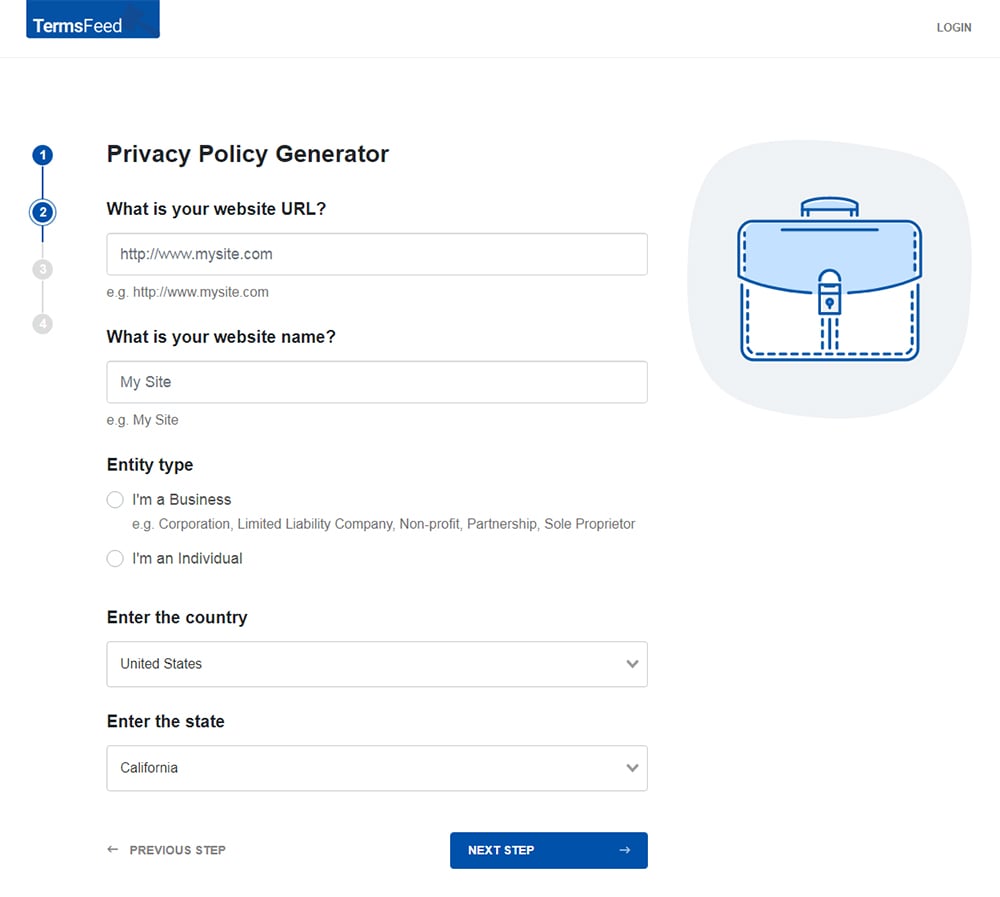
Answer some questions about your website or app.
-
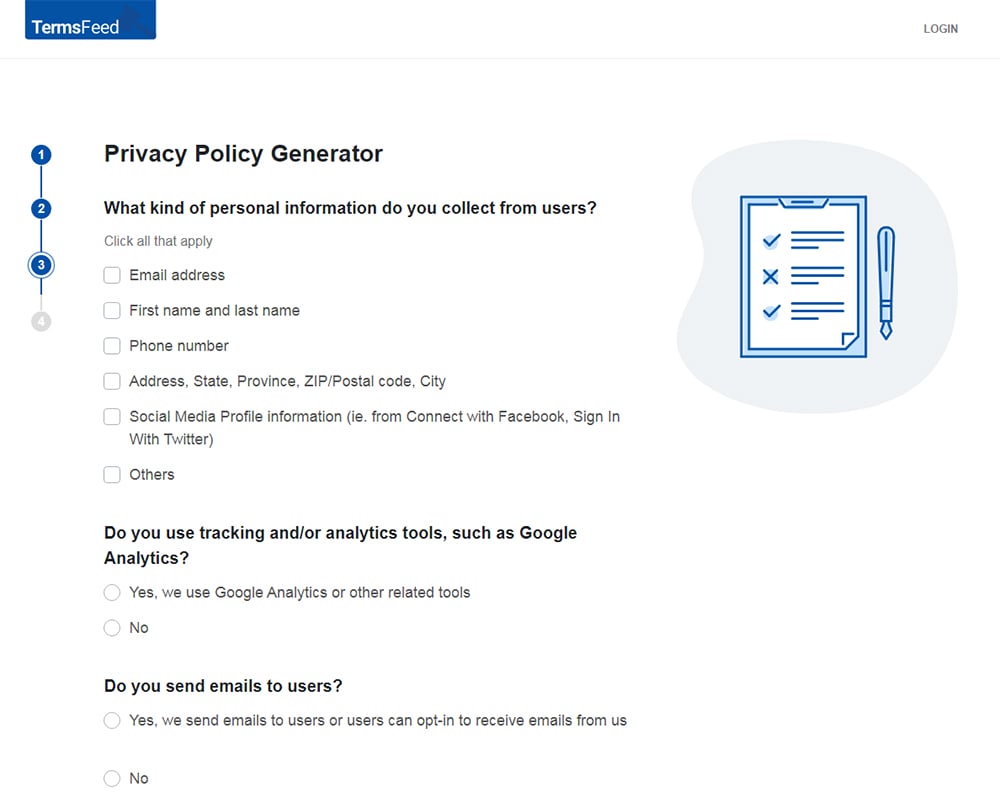
Answer some questions about your business.
-
Enter the email address where you'd like the Privacy Policy delivered and click "Generate."
You'll be able to instantly access and download your new Privacy Policy.
- 1. What is Vermont's Data Breach Notification Law?
- 2. Updates to Vermont's Security Breach Notice Act
- 3. Who Does Vermont's Security Breach Notice Act Apply to?
- 3.1. Your Location Doesn't Matter
- 3.2. Exemptions from the Act
- 4. What Should You Do if There's a Security Breach?
- 4.1. Secure the Data
- 4.2. What Else Should You Do?
- 4.3. What Shouldn't You Do if There's a Security Breach?
- 5. Overall Compliance with Vermont's Data Breach Notification Act
- 5.1. Notice to Consumers
- 6. In Sum
What is Vermont's Data Breach Notification Law?
According to Vermont's Security Breach Notice Act, which was originally passed in 2006, with subsequent updates in 2012, 2013, 2015, and then in March of 2020, state agencies and businesses have to notify consumers and the Attorney General if they experience a security breach.
The definition of a security breach, according to the Act is the:
"unauthorized acquisition or a reasonable belief of an unauthorized acquisition of electronic data that compromises the security, confidentiality, or integrity of personal information maintained by the [business or state agency]."
Under the Act, Personally Identifiable Information (PII) is defined as an individual's first initial or first name and last name put together with at least one of the following digital data elements when these elements are not redacted, encrypted or otherwise protected by other methods that render them unusable or unreadable by unauthorized parties:
- Records of a wellness program or health records or a similar health promotion program for disease prevention such as a medical doctor's diagnosis or treatment of the individual, or a health insurance policy number
- Genetic information
- Biometric data that is generated from technical analysis or measurements of human body characteristics used by the licensee or owner of the data to authenticate or identify the individual, such as a retina or iris, a fingerprint, or some other digital representation or unique physical representation of that biometric data
- An access code for a financial account, a personal identification number (PIN), or a password
- A credit card number or financial account number if that number can be used without other identifying information, passwords, or access codes
- A passport number, drivers license or nondriver State identification card number, military identification card number, individual taxpayer identification number, or other identification numbers that originate from a government identification document, which is commonly used to verify IDs for commercial transactions
- Social Security number
In addition to the above, the Attorney General's office considers the front of a check that contains the account number, name, and routing number (also potentially the signature and address) to be PII.
Finally, even if a credit card's expiration date and security code (CVV) are not included, the credit card number and name on the card are still considered PII.
Updates to Vermont's Security Breach Notice Act

As stated at the outset, the Act was amended in 2020 and went into effect on July 1 of that year. This amendment applies only to security breaches for which a data collector was notified or that were discovered after the Act's amendment became enforceable.
Immediately below are the significant changes brought about by the 2020 amendments.
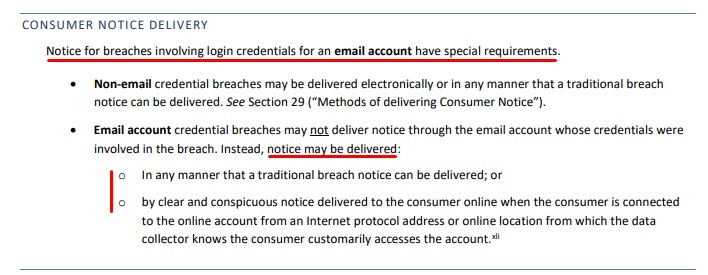
- A different type of notice is now required for breaches involving login credentials. Under the Amendments, Login credentials mean a consumer's username or email address, combined with a password or an answer to a security question, which allows access to an online account. See below for details on the new type of notice for breaches involving logins (at page 20 of the linked PDF):
- Substitute notices are not permitted any longer based on how many consumers were affected by the breach. Additionally, conditions under which substitute notices are still permitted have been narrowed to where the lowest cost of providing Direct Notice through telephone, email, or writing would surpass $10,000, or the data collector doesn't have enough contact information.
- Finally, Amendments to the Act introduce the Data Broker Security Breach. This does not change the Security Breach Notice Act. However, it does require yearly reporting and/or disclosure of the number of data broker security breaches suffered during the prior year.
Who Does Vermont's Security Breach Notice Act Apply to?

If your company is a data collector and you've suffered a data breach, then you are bound to abide by the regulations set forth in the Act.
The definition of "Data Collector" in this context is an entity that, "for any purpose, whether by automated collection or otherwise, handles, collects, disseminates, or otherwise deals with nonpublic personal information."
Other types of entities besides businesses, which are affected by the Act, are state agencies, public and private universities, non-profit organizations, and municipalities.
Your Location Doesn't Matter
Similar to many other data protection laws enacted across the United States, your business doesn't have to be located in the state.
If your organization does business in the state of Vermont and if even one state resident's data has been compromised due to a security breach, the Act applies to you.
Exemptions from the Act
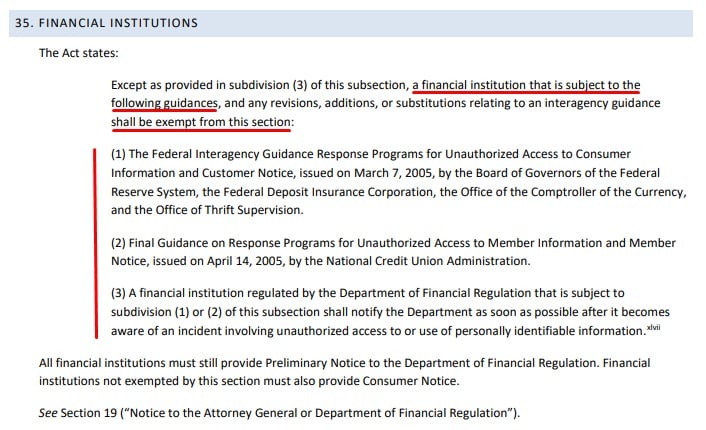
Many financial institutions are exempt. Here it is, taken from page 22 of the earlier-linked PDF:
Now that you understand a bit about the purpose behind the Act, how it came about and whether or not it applies to you, let's look at what practical steps will need to be taken to comply with the Act.
What Should You Do if There's a Security Breach?

If you believe that your business has been the victim of a security breach, you should do the following right away:
Go over the steps listed below as soon as you discover a security breach, and do as many of them as you're able, as fast as you can.
Secure the Data
As soon as a data breach is discovered, you should immediately disconnect your affected computers from networks and remove the impacted hard drives. This is a reasonable first step in stopping any ongoing information theft, which might still be occurring.
Try to take this step without destroying any evidence law enforcement might need when they investigate.
Additionally, you should:
- Call law enforcement before removing affected hard drives. Work with them and the head of your IT department to secure the data.
- Make backups of altered or damaged files.
- Make copies of old backups to show the status of the original.
- Choose one person to secure possible evidence.
- Evidence may consist of printouts and tape backups. Make sure these are initialed and dated by the individual you've chosen to obtain the evidence. Also ensure that the evidence is locked in a cabinet accessible only to one person.
- Keep records of everything, including any efforts to locate the perpetrator or reestablish your system.
What Else Should You Do?
As noted above, you should get law enforcement involved right away. If you happen to be storing someone else's data, ensure that you contact them immediately.
You'll also need to:
- Provide preliminary notice to the Attorney General's office within 14 days of the security breach. (This notice is kept confidential.)
- Notify affected individuals in the fastest time possible and no later than 45 days after you've been notified or you discover the security breach.
- If you're going to send a notice of a security breach to more than 1,000 affected consumers, you'll need to notify the three major credit reporting agencies.
What Shouldn't You Do if There's a Security Breach?
You should never alter, delete, or move files from systems that you believe were affected by a security breach without consulting law enforcement or a forensic expert.
You should also never contact the person or person you believe may have perpetrated the crime.
Finally, never procrastinate when it comes to sending a preliminary notice of a security breach to Vermont's Attorney General.
Overall Compliance with Vermont's Data Breach Notification Act

There isn't a specific requirement to investigate potential breaches. However, it is assumed that you will conduct one. In fact, if you even suspect there's been a breach, but you fail to notify the Attorney General's office and the affected consumers, then you've violated the Act.
Additionally, if you fail to cooperate 100 percent with third-party investigators like the Payment Card Institute (PCI) so that the investigation takes longer than authorities deem it should, you have also violated the Act.
Authorities will look at whether you, as the data collector, have acted in the most expedient manner possible. This is measured from the moment you are notified or first discover a security breach.
Moreover, it's possible that if you fail to properly investigate a security breach, it might be considered a deceptive or unfair act in violation of Vermont's Consumer Protection Act.
Notice to Consumers
Data collectors that do business in the state of Vermont and who maintain or possess PII have to notify the licensors or owners of the PII if they believe that data has been compromised. This is true regardless of whether the PII is in an electronic or hard-copy format.
Electronic or digital formats include:
- Text messages (SMS)
- Instant message
In Sum
What customers say about TermsFeed:
This really is the most incredible service that most website owners should consider using.
Easy to generate custom policies in minutes & having the peace of mind & protection these policies can offer is priceless. Will definitely recommend it to others. Thank you.
- Bluesky's review for TermsFeed. Read all our testimonials here.
With TermsFeed, you can generate:
Remember that data breach laws across the United States are changing at a rapid pace. It's possible that Vermont's data breach notification law could be amended again in the future. Therefore you should pay close attention to updates as they occur so that you can make sure any response plans you have are current.
It's vitally important to remember how short a time you have to notify the office of Vermont's Attorney General in case of even a suspected security breach. You only have 14 days. This is the shortest time frame for notification in the entire United States.
Business owners are advised to ensure that they plan in advance for the possibility of a security breach, have written response policies, and test those response policies regularly.

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.