Since the California Consumer Privacy Act (CCPA/CPRA) came into effect, there have been several high-profile lawsuits against businesses that have allegedly failed to properly secure consumers' personal information.
California has the most data breaches of any state, so we can expect to see many more CCPA (CPRA) claims. However, the CCPA/CPRA's private right of action is relatively narrow and will only apply in quite specific situations.
In this article, we'll take a detailed look at how the CCPA/CPRA's private right of action works, and how to avoid being taken to court by California consumers.
(Note that the CPRA updated, amended and expanded the CCPA in January of 2023.)
- 1. Who is Covered by the CCPA (CPRA) Private Right of Action
- 1.1. Businesses, Consumers, Personal information
- 1.2. Relevant Types of Personal Information
- 2. Violations That Can Give Rise to Private Legal Action
- 2.1. Elements of a Data Breach
- 2.2. Unauthorized Access and Exfiltration, Theft, or Disclosure
- 2.3. Reasonable Security Procedures and Practices
- 3. Amount of Damages
- 3.1. Actual Damages
- 3.2. Statutory Damages
- 4. Notice and Cure Provision
- 4.1. Thirty Days' Notice for Statutory Damages
- 4.2. Curing a Violation
- 5. Avoiding Private Claims Under the CCPA (CPRA)
- 5.1. Secure Consumers' Personal Information
- 5.2. Comply With All Other CCPA (CPRA) Provisions
- 6. Summary
Who is Covered by the CCPA (CPRA) Private Right of Action
The CCPA/CPRA's private right of action allows consumers to bring a private legal case against a business that will be heard before the California courts.
Businesses, Consumers, Personal information
The CCPA (CPRA) protects "consumers," meaning California residents. As such, only consumers can exercise the CCPA/CPRA's private right of action, and can do so as individual plaintiffs or in a class action.
Consumers can only bring a private legal claim under the CCPA/CPRA's private right of action against businesses, not service providers or other parties.
Under the CCPA (CPRA), a "business" is a legal entity that:
- Operates for profit in California
- Decides why and how to process personal information
-
Meets one or more of the following thresholds:
- It has annual gross revenues of at least $25 million
- It buys, sells, and/or receives or shares for commercial purposes the personal information of at least 100,000 consumers, devices, or households
- It derives at least 50 percent of its annual revenues from the selling or sharing of consumers' personal information
Relevant Types of Personal Information

Businesses may be relieved to learn that only certain types of personal information are relevant to the CCPA/CPRA's private right of action provision.
As such, only businesses that collect these relevant types of personal information are likely to be subject to a successful private action.
For the most part, the CCPA (CPRA) has an extremely broad definition of personal information:
"Information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household."
However, with regard to the private right of action, the definition of personal information only includes those types of data identified in Section 1798.81.5 (D) (1) (A) of the California Civil Code, also known as California's Data Breach Notification Law (available here).
This means that "personal information," for our purposes, refers to a data set including both elements 1 and 2 below, where at least one of the elements is not encrypted and is not redacted:
- A person's first name or first initial, AND their last name
-
One or more of the following elements:
- Social security number
-
Any unique ID number that is "issued on a government document commonly used to verify the identity of a specific individual," such as:
- Driver's license number
- California ID card number
- Tax ID number
- Passport number
- Military ID number
-
Account number or credit/debit card number, in combination with any required information that would permit access to the account, such as:
- Security code
- Access code
- Password
- Medical information
- Health insurance information
-
Biometric information, not including a physical or digital photo (unless used for identification purposes), such as:
- Fingerprint
- Retina image
- Iris image
The above types of personal information are particularly sensitive, and you should take extra steps to secure them to avoid a claim under the CCPA (CPRA).
The following lists the types of data that individuals and their attorneys will have the right to sue under the CCPA/CPRA's private right of action if a data breach occurs:
- Unique biometric data (must include name)
- Health insurance data (must include name)
- Medical information (must include name)
- Debit card number (with required security code or password and name)
- Credit card number (with required security code or password and name)
- Financial account number (with name and that permits access to the account)
- Military identification number (must include name)
- Passport number (must include name)
- Tax identification number (must include name)
- California identification card number (must include name)
- Driver's license number (must include name)
- Social security number (must include name)
- Other unique identification numbers issued on government documents used to verify identity. (must include name)
Violations That Can Give Rise to Private Legal Action

Unlike the CCPA/CPRA's civil penalties provision, whereby the California Attorney-General can take legal action against a business that violates any part of the CCPA (CPRA), the private right of action applies only in the event of a data breach.
The nature of an actionable data breach is also quite specific and will not apply in all cases.
Elements of a Data Breach
The type of data breach that can give rise to private legal action under the CCPA (CPRA) is set out in section 1789.150 (a) (1):
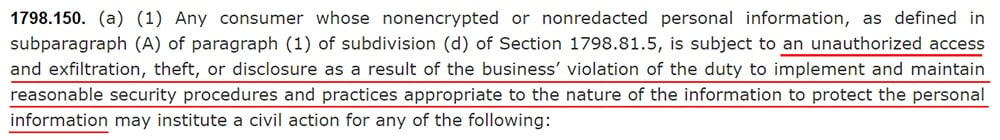
Note that there are four interlinked elements here, all of which must be present for a claim to succeed:
- Unauthorized access, AND
- Exfiltration, theft, or disclosure, AS A RESULT OF
- Failure to implement and maintain reasonable security procedures and practices to protect the personal information, THAT ARE
- Appropriate to the nature of the information
Unauthorized Access and Exfiltration, Theft, or Disclosure

For the purposes of the CCPA (CPRA), the fundamental definition of a data breach is the unauthorized access and exfiltration, theft, or disclosure of personal information.
Note that the breached personal information must be both accessed and exfiltrated, stolen, or disclosed.
Therefore, the mere loss of personal information (e.g. if an employee leaves a USB drive on a train) should not give rise to private action unless the information is also subject to unauthorized access.
This would appear to be a high threshold for consumers, but the courts may interpret this provision more narrowly.
Remember that "unauthorized access" may arise from inside your business as well as from outside actors.
Reasonable Security Procedures and Practices
An actionable breach occurs when a business fails "to implement and maintain reasonable security procedures and practices appropriate to the nature of the information to protect the personal information."
The CCPA (CPRA) doesn't define "reasonable security procedures and practices." The best starting point for understanding what this means is the California Data Breach Report from February 2016 (available here).
The key takeaway from this report is below:
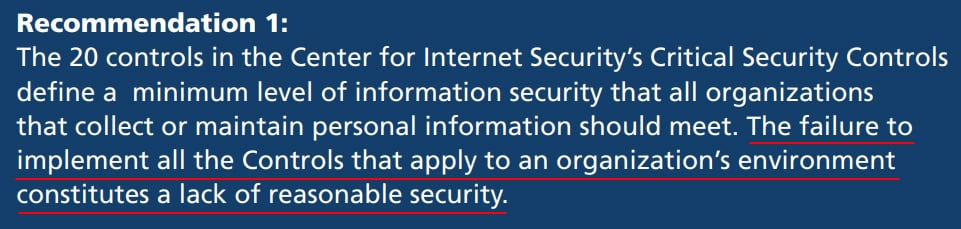
Here, the California Attorney-General's defines a reasonable standard of security as the implements of all 20 of the Center for Internet Security (CIS) Critical Security Controls (insofar as they relate to your business).
We'll be examining the CIS Controls below.
Amount of Damages

Damages resulting from a private action under the CCPA (CPRA) can be calculated in two ways:
- Actual damages
- Statutory damages
The greater of these two will be awarded to the consumer(s) (not both).
Actual Damages
"Actual damages" means losses that resulted directly from the business's failure to properly secure user data.
For example, if a consumer's credit card details are breached, actual damages will equate to the money that is stolen from them.
Many data breaches involve other types of personal information, and actual damages can be difficult to prove. Therefore, claims for actual damages are likely to be less common than those for statutory damages.
Statutory Damages
The extent of statutory damages will be decided by the court, and this amount is not directly related to any actual losses incurred by the consumer bringing the case against the business.
Statutory damages will be calculated as an amount between $100 and $750, per consumer, per incident.
One "incident" occurs each time a consumer's data is breached. Most data breaches involve large numbers of consumers and so the volume of "incidents" will typically be very high.
The court will consider several factors when assessing the amount of statutory damages to be awarded to a consumer:
- The nature and seriousness of the business's misconduct
- The persistence of the misconduct
- The duration of the misconduct
- The willfulness of the business's misconduct
-
The business's:
- Assets
- Liabilities
- Net worth
Notice and Cure Provision

Before a consumer can pursue statutory damages from a business, the CCPA (CPRA) requires them to give the business an opportunity to fix the problem.
This is known as the "notice and cure" provision.
Thirty Days' Notice for Statutory Damages
A consumer (or group of consumers) must give a business thirty days' written notice before bringing a private legal claim.
The consumer must specify which provisions of the CCPA (CPRA) they allege the business is violating.
A consumer pursuing "actual pecuniary damages" (pecuniary meaning monetary) is not required to give this notice period.
Curing a Violation
Within 30 days of receiving notice, the business must:
- "Actually cure" the violation, and
-
Provide the consumer with an express written statement that:
- The violation has been cured
- No further violations will occur
The CCPA (CPRA) does not provide a definition of "actual cure." There are several possible interpretations of this term.
A "cure" could be the effective stemming of a data leak, together with the rectification of whatever security flaws gave rise to the leak.
Note, however, that the statute acknowledges that a cure may not be possible. Previous California cases suggest that the prevention of possible future violations does not serve to cure the original violation with respect to a consumer.
It may be that once a data breach has occurred, and a consumer's personal information is lost, "the damage is done" and an actual cure will be impossible in most cases.
However, businesses "on notice" of a CCPA (CPRA) violation should be making every effort to reassure consumers by improving the security of their systems, re-training employees, etc. Even if this is not deemed to be an "actual cure," it may lead to a lower liability in statutory damages.
Avoiding Private Claims Under the CCPA (CPRA)

The CCPA (CPRA) gives businesses the opportunity to avoid private legal action for statutory damages even where a data breach has occurred.
But with sufficiently good data protection practices, it is unlikely that your business will encounter any threats of legal action under the CCPA (CPRA).
Secure Consumers' Personal Information
As noted, the CCPA (CPRA) is not specific about how to implement reasonable security controls.
However, the California Attorney-General has indicated that implementing the Center for Internet Security (CIS) Controls represents a minimum standard of reasonable security in similar contexts (more information about the CIS Controls is available here).
Here's an overview of the 20 controls:
- Inventory of authorized and unauthorized devices
- Inventory of authorized and unauthorized software
- Secure configurations for hardware and software on mobile devices, laptops, workstations, and servers
- Continuous vulnerability assessment and remediation
- Controlled use of administrative privileges
- Maintenance, monitoring, and analysis of audit logs
- Email and web browser protection
- Malware defenses
- Limitation and control of network ports, protocols, and services
- Data recovery capability
- Secure configurations for network devices such as firewalls, routers, and switches
- Boundary defense
- Data protection
- Controlled access based on the need to know
- Wireless access control
- Account monitoring and control
- Security skills assessment and appropriate training to fill gaps
- Application software security
- Incident response and management
- Penetration tests and red team exercises
Read more about the steps you can take to implement data security in your business in our articles: NY Shield: How to Implement a Data Security Program and IT Security Policy.
Remember that the private right of action is relevant only to personal information that has not been encrypted or redacted. Therefore, you should encrypt personal information wherever possible.
One of the top ways for businesses to stay compliant with the CPRA amendments to the CCPA and keep themselves from the risk of liability is to enact the type of strict security protocols called for under Europe's General Data Protection Regulation (GDPR).
Obviously, preventing security breaches is a top-level concern. Businesses need to find ways to improve whatever data security plans they have to lessen the likelihood of such a breach. If they don't have them, they need to develop and establish them.
Just some ways companies can begin to further boost security and protect sensitive data are:
- Conduct a Security Audit: Recall that regular audits of your security plans are essential. You need to be proactive in your plan, and regular audits allow you to find gaps in your current strategy. Eliminating risk is the goal.
- Create a data-centric security strategy: Internet of Things (IoT), cloud services, and mobile have all but destroyed traditional network boundaries. Businesses must now approach network security in a holistic fashion, focusing on strategy. Security experts emphasize that businesses need to implement a data-centric approach in order to understand the information they possess and how valuable it is to their company's operations. Once a business knows what information it has, it must then secure it through strong encryption. Additionally, a powerful backup strategy must be developed and tested.
- Hire a dedicated security professional: Many of the largest tech companies are hiring for positions such as "Chief Security Officer." These aren't security professionals hired to protect physical assets. They're not building security. Instead, these professionals are hired to protect and secure a company's sensitive business information. In other words, they're cybersecurity experts.
- Use multi-factor authentication: Following a data breach; many executives switch out their login details. However, that's far too late once the breach has occurred. In fact, most security experts state that many businesses don't even realize a data breach has happened until weeks or months after the fact. During that time, hackers are able to take advantage of your data's compromised state. One of the methods to prevent this from ever occurring in the first place is to stop hackers from viewing your company as "low-hanging fruit." By establishing multi-factor authentication (MFA) to all administrative accounts, you can lessen risk considerably.
- Educate Staff: Together with the growth of the Internet of Things, there are a few different ways to ensure data protection. One of the most vital has to do with educating your staff on the importance of overall data security. By informing them on current security trends, you can be proactive in keeping your information secure. Additionally, you should ensure that passwords are changed regularly and that those authorized to access sensitive data are limited.
Remember that with the changes brought by the CPRA, it is increasingly important for your business to evaluate its security controls, its information retention practices, and systems, and your response plans in case of a data breach.
The more prepared you are to prevent a data breach, the more able your business is to mitigate security failures, the less risk of liability your company faces due to the CPRA's expansion of the CCPA.
Comply With All Other CCPA (CPRA) Provisions

The first wave of class actions under the CCPA (CPRA) has begun, and some of these cases make various claims about businesses violating CCPA (CPRA) provisions other than the obligation to secure consumers' personal information.
For example, in the class action against Zoom, the plaintiffs accuse video conferencing software company Zoom Inc. of failing to provide proper notice of the collection and disclosure of their personal information.
The plaintiffs in the Zoom case may have reasonable grounds to argue that Zoom failed to give proper notice under the CCPA (CPRA). However, it is unclear how their case will succeed, given that failing to give notice is not a violation that should give rise to the private cause of action.
According to the CCPA (CPRA), it is for the Attorney-General to bring a case for a civil penalty against a business that has violated the CCPA/CPRA's other provisions.
That being said, it is clear that the violation of other CCPA (CPRA) provisions is leading to class action cases being brought against businesses. Regardless of the merits of such cases, this is something every business will want to avoid.
Therefore, proactive compliance with all obligations under the CCPA (CPRA) is essential for any business falling under its jurisdiction.
Some key ways in which you can ensure your business complies with the CCPA (CPRA) include:
- Ensuring your Privacy Policy complies with the CCPA/CPRA's requirements
- Providing adequate notice when collecting consumers' personal information
- Complying with requests under the CCPA (CPRA) consumer rights within 45 days
- Ensuring service providers are operating under a contract
Summary
Here's what you need to know about the CCPA/CPRA's private right of action:
- The private right of action allows consumers to bring private legal cases against businesses
- A case can only be brought by a consumer or group of consumers against a business
- The private right of action only covers a data breach involving certain types of personal information
- A "breach" occurs when there has been both unauthorized access and exfiltration, loss, or theft of personal information that has not been subject to reasonable security procedures
- Consumers can pursue actual damages or statutory damages from a business
- Before bringing a claim for statutory damages, a consumer must provide the business with 30 days' notice
- If the business can "actually cure" its CCPA (CPRA) violation within the 30-day period, it may escape liability

Comprehensive compliance starts with a Privacy Policy.
Comply with the law with our agreements, policies, and consent banners. Everything is included.




